Dangerous Game Mods and Cheats Hide Malware Through a VB6 Cryptor
- A new, complex VB6-based cryptor is able to hide malware payloads inside game mods and cheats.
- The people who are using this kind of software are used to AV alerts and simply ignore them.
- Crooks could be after cyber-espionage, targeting remote-working employees.
There’s a new campaign taking place out there, targeting video game players who are keen to use mods and cheats. According to Cisco Talos, who have been following the activity closely, the actors are using a Visual Basic 6 cryptor along with shellcode and process injection techniques, hiding malware droppers that can fetch a variety of payloads.
Because these game mods are unofficial anyway, users find it natural to run untrustworthy tools to install the required packs, which is precisely why the crooks find this otherwise niche space so ideal for exploitation.
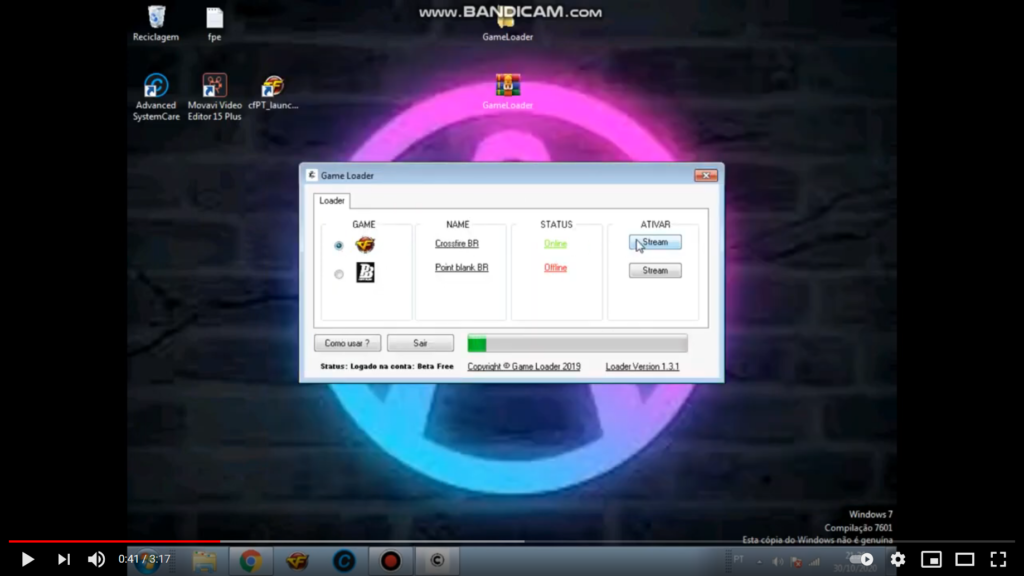
The campaigns are promoted on social media and YouTube, where the actors publish “How To” tutorials to showcase exactly how to install the game mods. Even if the promised cheats and tweaks are delivered, most of these packs are backdoored with dangerous RATs that can steal information from the infected machines.
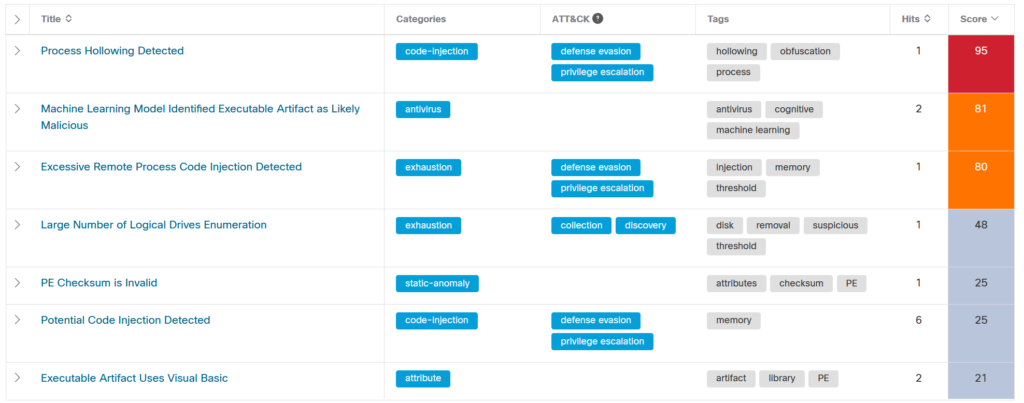
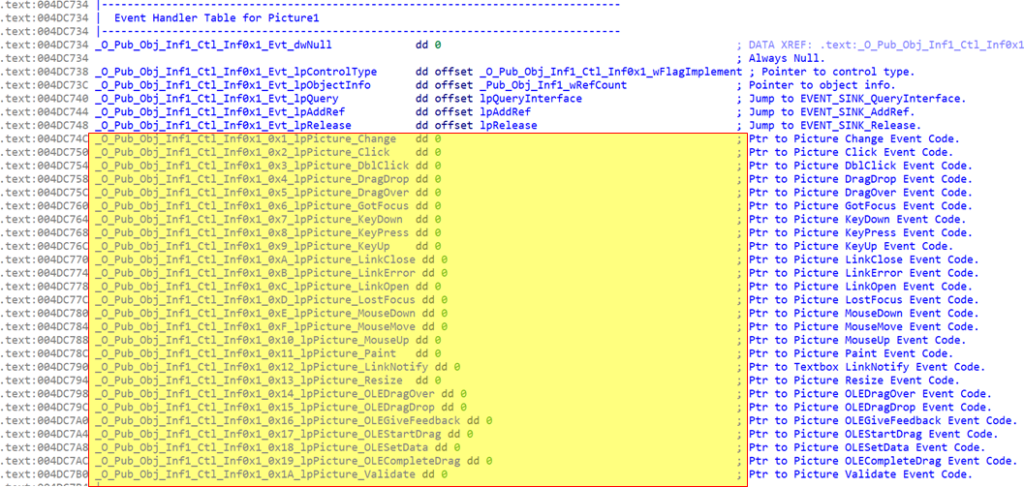
The Talos report goes deep into the obfuscation techniques and the identifiers of the sampled VB6 headers. In summary, we see a multi-faceted effort to hide the malware's malicious nature with decoy routines and invalid PE headers. Still, it seems that most AV engines will catch the threat, putting it between suspicious and malicious. But again, when people install these game mods, they actually expect to see a warning from their AV as no one signs these installation packs.
If the user proceeds, the dropper injects code into a new process so the final payload can be hidden better against malware detection engines, and from there, anything is possible for the actors. Talos comments that this campaign could be targeting corporate information, and considering the complexity of the VB-based cryptor, it doesn’t look like the work of amateurs. People working remotely from home may be using the same machines to play games and relax, so this could be the idea behind the campaign.
The takeaway from all that is never to trust unofficial mods and game cheats that come through obscure and untrustworthy installers. If you have to use one, don’t install it on the same system you are using for work. And if you still have to do that as well, make sure not to ignore any alarms raised by your anti-virus/anti-malware solution. If an executable is marked as suspicious, there’s a very good chance that it is malware.