D-Link Home Routers Were Targeted by DNS Hijackers Thrice
- DNS hijackers launched three waves of attack against vulnerable home modem routers.
- The attacks sought phishing and domain parking potential, but not many details about that are known yet.
- People are urged to check their router settings and update their firmware immediately.
According to a Bad Packets report, several thousand of home routers that are plagued by various vulnerabilities have fallen prey to malicious actors who have hijacked their network traffic for a period that spans over the past three months. Although the majority of the exploited routers are made by D-Link, Bad Packet’s honeypots detected exposed routers from TOTOLINK, ARG, and Secutech as well. The attackers have compromised the targeted routers by setting their preferred DNS Server to various sets of rogue ones, essentially hijacking the network traffic.
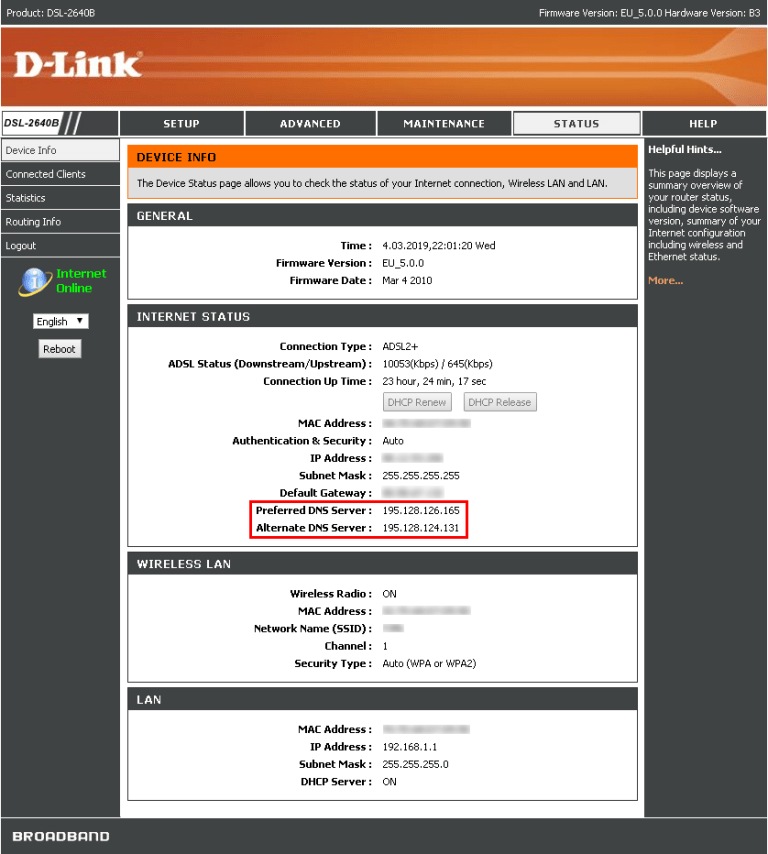
The first wave was detected at the end of December, last year, targeting various D-Link DSL modems such as the 264OB, 274OR, 278OB, and the 526B. The rogue DNS used in this first wave was 66.70.173.48, hosted by OVH Canada. The second wave came in the start of February 2019, targeting the same modem models, and using a different rogue server (144.217.191.145) hosted by OVH Canada again. The third wave which occurred on March 26, 2019, was more extensive, targeting more modem models from additional manufacturers, and originating from Google Cloud Platform hosts. The hosting services of the rogue DNS servers (195.128.126.165 and 195.128.124.131) were also differentiated this time, being hosted by the Russia-based Inoventica Services.
image source: badpackets.net
The researchers believe that the primary motive behind these attacks is domain parking, which helps generate advertising revenue quickly. Another possible incentive for these campaigns could be “silent phishing” activities that redirect the domain name of a targeted site by the rogue DNS server to one that is controlled by the phishing actor. Simply put, a user who has had his/her router compromised would end up in a clone of the site they are trying to access. Think of a PayPal login page for example, and you’ll get the idea of how the phishing works.
The researchers were not able to figure out what websites the hackers tried to spoof in these campaigns, so there can be no warning on that part. What you can do in order to figure out whether your modem has been compromised is to check your router’s settings and look for the indicators of compromise, in this case, the preferred DNS server numbers as given above. Also, if you are using D-Link, ARG, DSLink, Secutech, and TOTOLINK modem routers, upgrade your firmware as soon as possible, which should be a practice to follow whatever modem you’re using really.
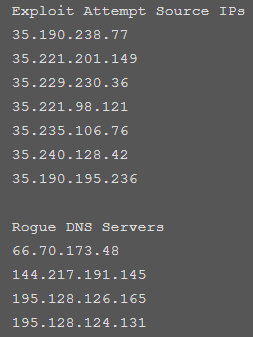
image source: badpackets.net
Care to share your thoughts on the above? Do so in the comments section beneath, and don’t forget to help us spread the word about the dangers of DNS hijacking by sharing this post through our socials, on Facebook and Twitter.