D-Link Camera Vulnerable to Video Stream Interception
- The D-Link DCS-2132L is encrypting none of its sensitive communication information.
- An attacker could intercept the data stream, gather the packs, and then reconstruct them.
- Replacing the vendor’s firmware with a malicious one is also possible thanks to multiple flaws.
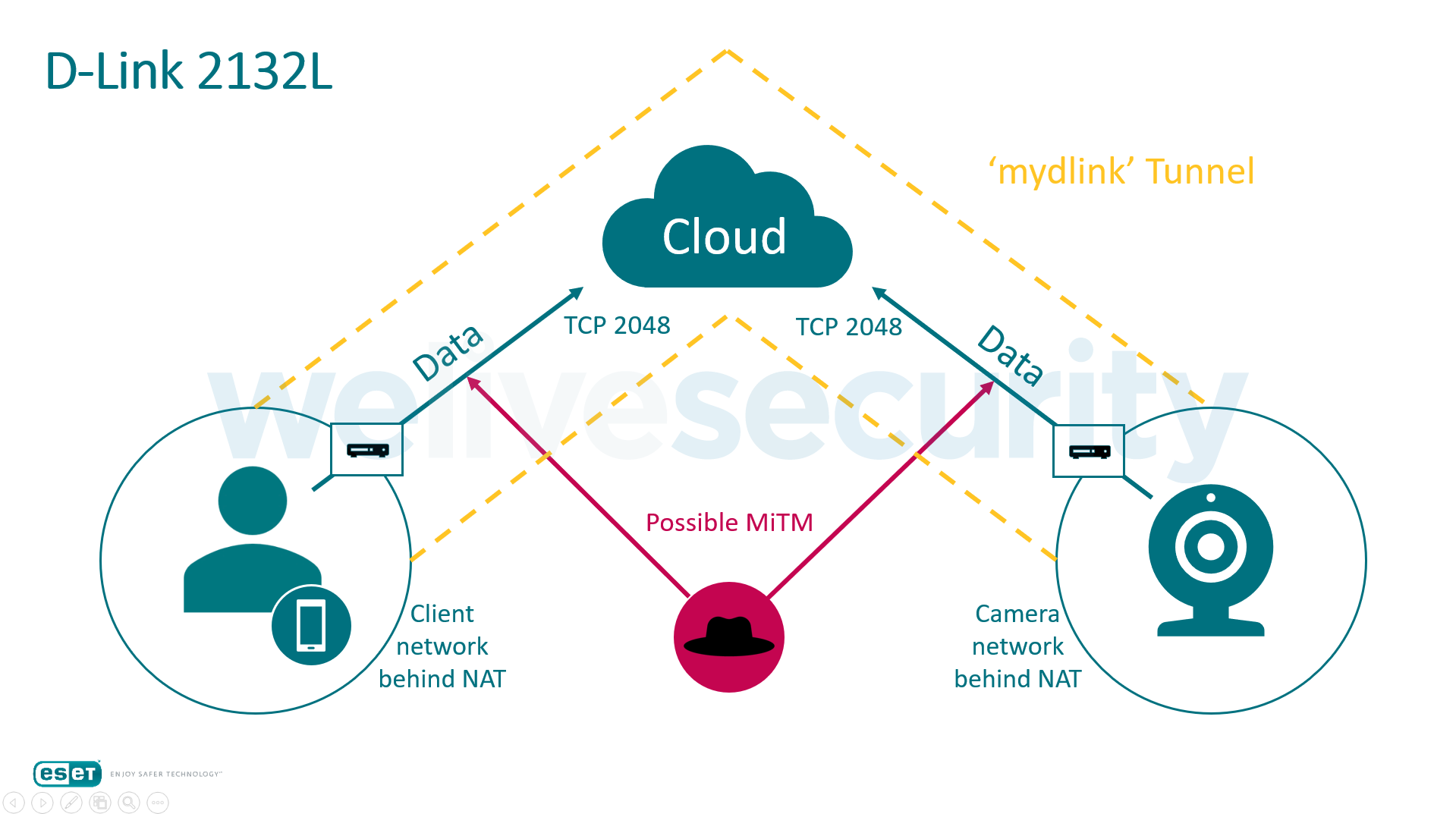
ESET security researchers have discovered a serious vulnerability that plagues the D-Link DCS-2132L cloud camera, a product that has been around since 2013 and has sold pretty well. Unfortunately, the camera which is placed to add security on a location is the very device that undermines it, by allowing someone to draw its live video stream. Because of the fact that the video stream transmission is unencrypted, the hackers could place themselves in between the cloud and the client or the camera and the cloud, and get a clear view of whatever the D-Link lens is pointing at. Long story short, conduct a man-in-the-middle attack to spy on the victim.
image source: welivesecurity.com
D-Link did make some kind of an effort to encrypt the video stream by using a proxy server for the communication and a TCP tunnel on a custom protocol, but unfortunately, most of the traffic running through these tunnels like the camera IP and MAC address are unencrypted. This makes it possible for sniffers to gather the required information to gain unconditional access to the device. The audio and video stream, as well as the firmware information and the camera information, are also passed through the tunnels without any encryption whatsoever.
The researchers have managed to get the stream in RAW video formats such as M-JPEG and H.264 by gathering the data packs that represent the video stream, separating the data parts from the headers, and then merging the data parts into a video file. The researchers have further discovered that D-Link’s browser plug-in (myDLink) opens the way for any application to send requests to the camera during the live video streaming, as the tunnel that is created locally is being made available OS-wide, and no further authorization is required. Now, this opens up the possibility of replacing the legitimate firmware with a backdoored one.
According to ESET’s report, even though D-Link issued a fix for their plug-in, the firmware replacement is still possible. The process involves the replacement of the video stream GET request with a specially crafted POST request that runs the firmware “update” which works more like a firmware replacement of course. As no verification process takes place at the next step, the new firmware could come with malware, spyware, or crypto-miners.
image source: welivesecurity.com
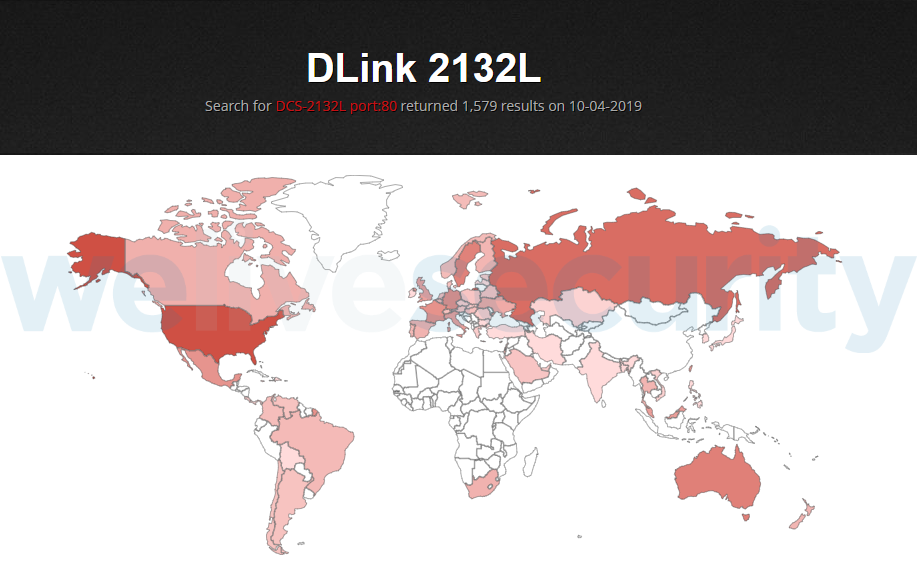
Finally, the researchers discovered that the device exposes its HTTP interface on port 80, so by running a Shodan search, they have found 1579 devices following this unsafe practice. Most of them are in the US, Russia, Australia, and Sweden. If you own a D-Link DCS-2132L, make sure to disable UPnP on your router.
Have any thoughts to share about the above? Do so in the comments down below, or on TechNadu’s socials, on Facebook and Twitter.