Cybersquatting Actors Love to Mimic PayPal, Apple, and Netflix
- Researchers detect hundreds of new cybersquatting domains each day, and a third of them are risky.
- Most internet security solutions aren't catching these domains' true nature even after 10 days following their registration.
- The actors' goal is often malware distribution and phishing, while various types of scams are also included.
The practice of cybersquatting remains a simple yet effective method to trick internet users and exploit them in a variety of ways. Malicious actors register domains that look similar to those of well-known brands. Their purpose is to convince visitors that they have landed on a legitimate website they can trust.
These domains usually have a typo that's hard to spot, or feature a combination with other words, or replace a character with a Unicode letter, or set up a subdomain that contains the spoofed brand's domain in it.
Source: Unit42
Researchers at Palo Alto Networks have taken a set of 13,857 squatting domains registered from December 2019 until recently (450 registrations per day) and studied their nature to come up with solid deductions about the current status of the scene.
The key takeaways of their report include the following points:
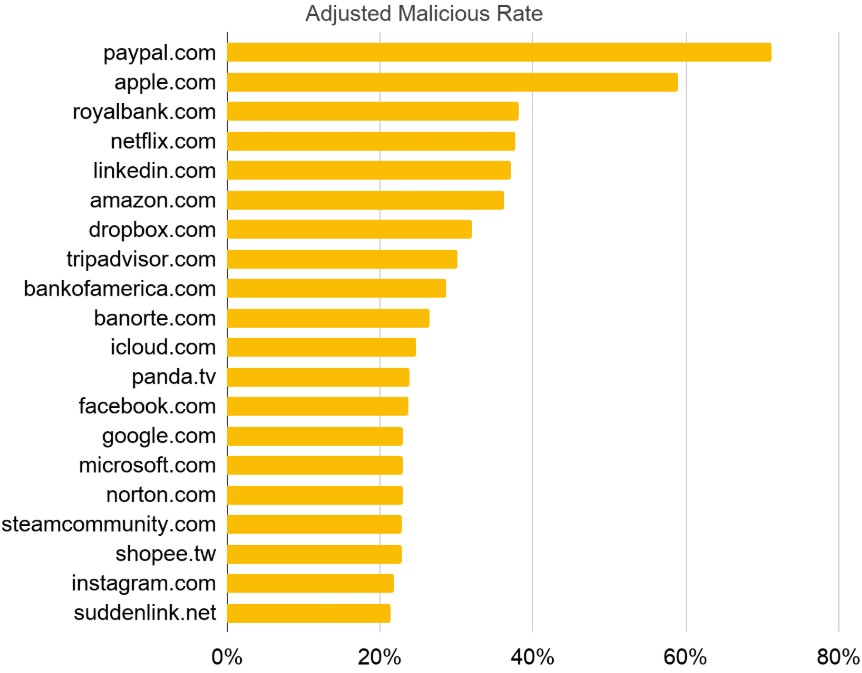
- The most frequently spoofed/targeted brand is PayPal, followed by Apple.
- The percentage of squatted domains that were confirmed to be malicious is 18.59%.
- The percentage of squatted domains that were confirmed to be risky is 36.57%.
- The most abused domain name registrar for cybersquatting is "Internet.bs."
- The most abused certificate authority for cybersquatting is "CloudFlare Inc ECC CA-2".
Source: Unit42
The actors' objectives range widely, from supporting phishing and malware distribution campaigns, setting up command and control servers, engaging in domain parking to trying to victimize internet users with fake tech support platforms. Reward scams, PUP, and re-bill scams are also included in the mix.
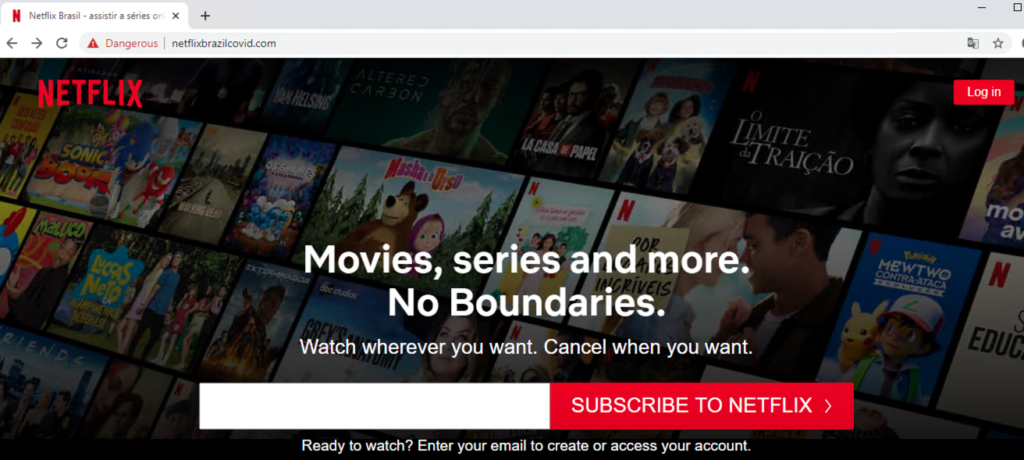
Related: Massive Phishing Campaign in Brazil Targeting Netflix Users
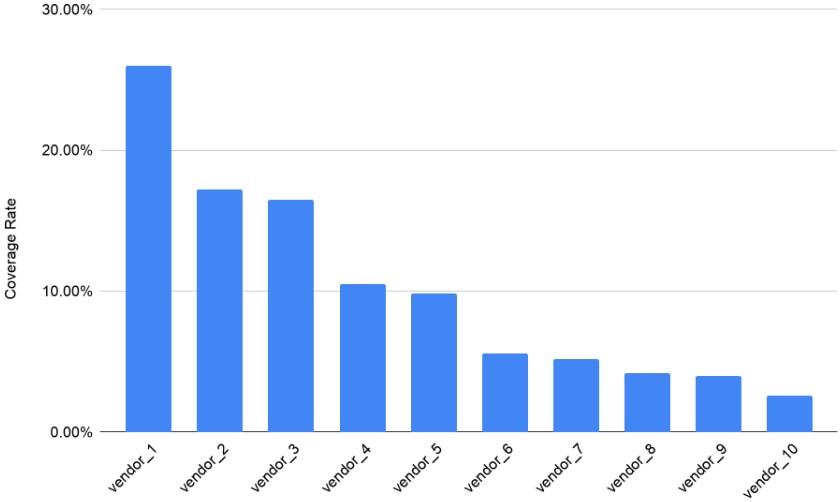
On the detection front, the Palo Alto researchers found that the detection rates on the majority of internet security solutions vendors are leaving a lot to be desired. Even the best performing vendor would only alert users in about 25% of the malicious or high-risk squatting domains, whereas the detection rates on next-best solutions drop below 18%.
Source: Unit42
All that said, users cannot rely on security solutions alone, and they shouldn't trust any domain they happen to land on. When you want to visit online banking services, buy something from an e-shop, or just search something on the net, check the domain name thoroughly and validate that it's the correct/official one.
Moreover, confirm that the domain has a valid SSL certificate and that you are on the website's HTTPS version.