Cybercriminals Use CloudFlare’s IPFS Gateway For Phishing Attacks
- Phishing attacks taking advantage of Azure Blob storage solutions are also using Cloudflare’s IPFS Gateway for malicious activity.
- The IPFS gateway is being exploited just a month after Cloudflare launched it.
- This gives the cybercriminals ability to make phishing URLs seem legitimate.
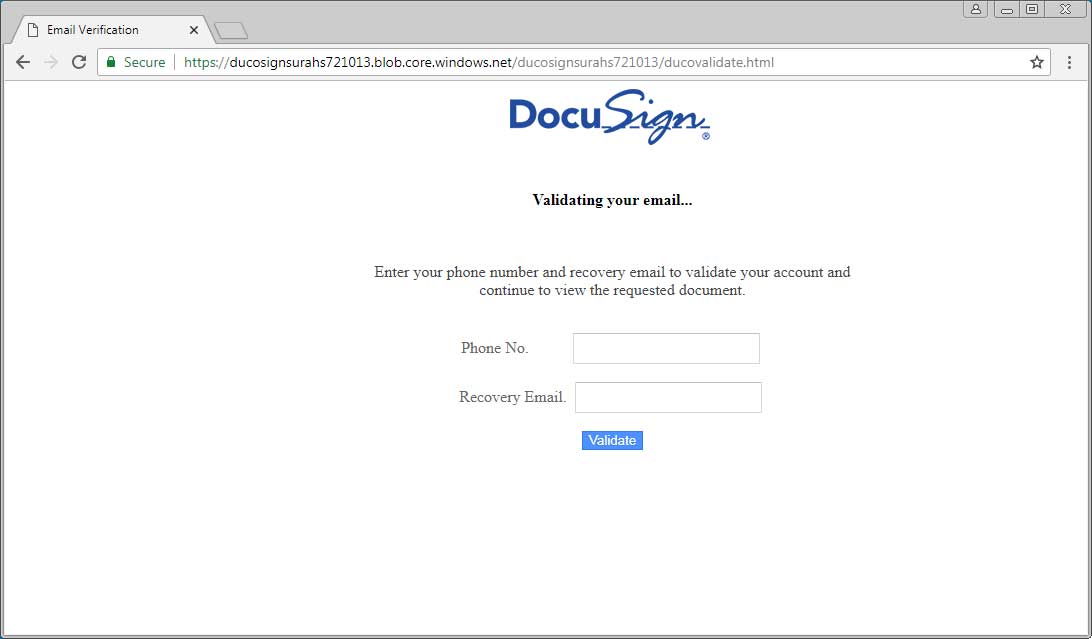
Cybercriminals have found a way to take advantage of Cloudflare’s newly launched IPFS gateway for phishing attacks. The gateway is used in similar fashion to how online attackers take advantage of Azure Blob storage to make login forms look secure and issued by Microsoft.
IPFS is defined as a “peer-to-peer or distributed file system that allows you to share files that will also be distributed to other computers, or nodes, throughout the networked file system. This makes it difficult to take down content stored on IPFS because even if one node is removed, the content will still be available from other nodes.”
Image Courtesy of Bleeping Computer
Cloudflare SSL protection is deemed to be secure, and browsers do not provide any warnings when visiting websites using IPFS gateways from the company. Phishing attacks take advantage of the security and lure unsuspecting internet users into putting in their personal data on unsecured websites.
Image Courtesy of Bleeping Computer
Attackers store the HTML data for phishing websites on the IPFS gateway and display the fake websites via the platform. With an SSL certification issued by Cloudflare, most users will be convinced about the legitimacy of the website and enter their private data.
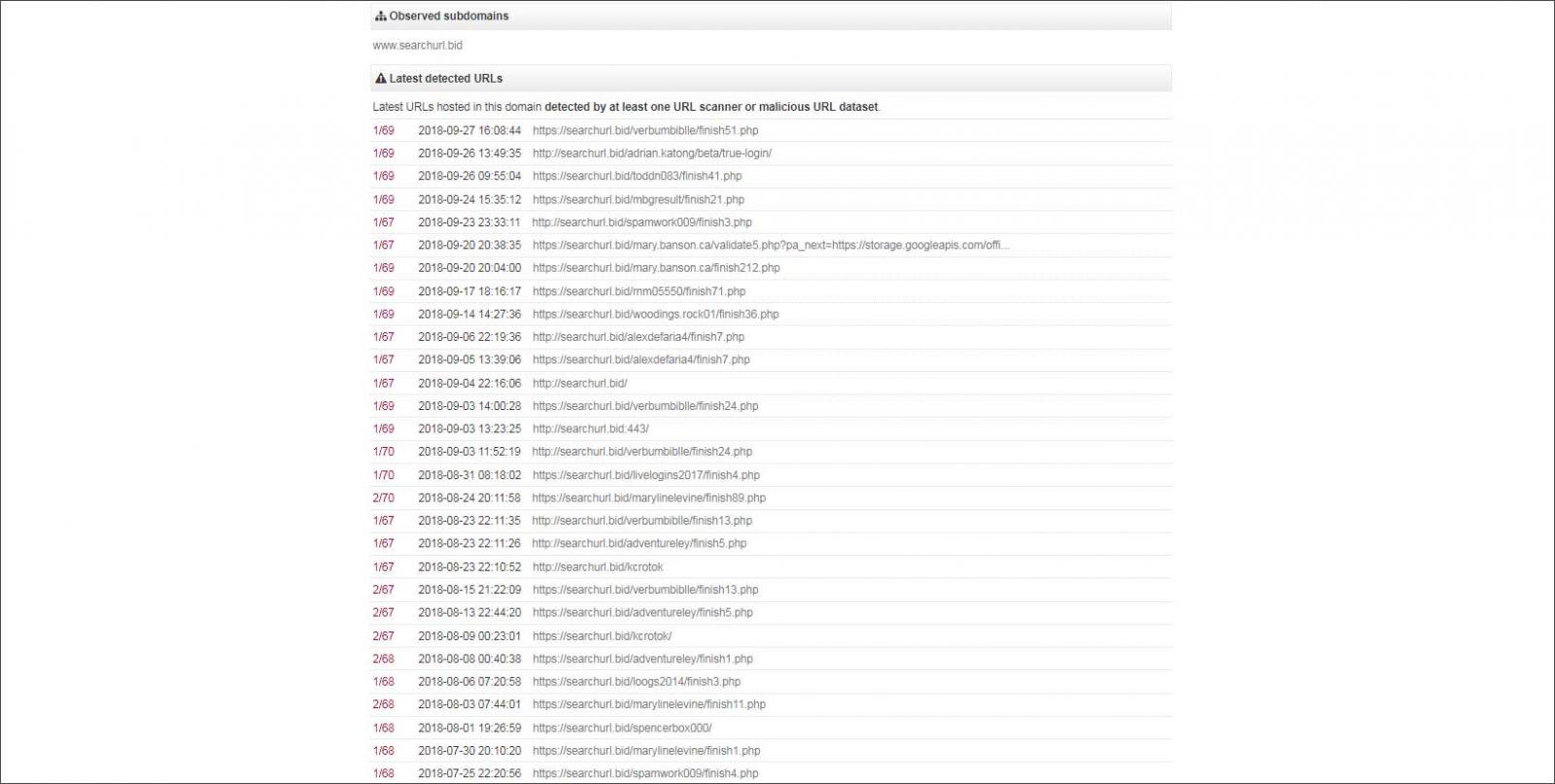
According to bleeping computer, the pages scanned were being operated by attackers from searchurl.bid. There are a large number of phishing URLs related to the website, and a number of form submission pages redirect to the platform.
The attackers have been involved with a large number of online phishing schemes this year. Even though most of the URLs do not look legitimate, many internet users are careless about their data and rush into putting their personal data into websites. The findings come right after Cloudflare and Google partnered to offer a new anti-censorship app that takes advantage of both Google and Cloudflare’s DNS servers to prevent DNS manipulation.
What do you think about the phishing attacks taking advantage of Cloudflare’s platform? Let us know in the comments below. And, make sure to follow us on Facebook and Twitter for the latest updates. Thanks!