Cybercriminal Group UAC-0173 Targets Ukrainian Notaries with DCRAT and XWORM Stealer
- The UAC-0173 hacker gang delivers advanced malware to Ukrainian notaries via phishing emails.
- The emails impersonate the Ministry of Justice of Ukraine and contain download links for malicious executables.
- After gaining remote access, the cybercriminals deploy RATs and infostealers.
The organized cybercriminal group UAC-0173 has reportedly been conducting targeted cyberattacks on notaries in Ukraine, seeking to gain covert remote access to their computers and make unauthorized changes to state registers for monetary gain.
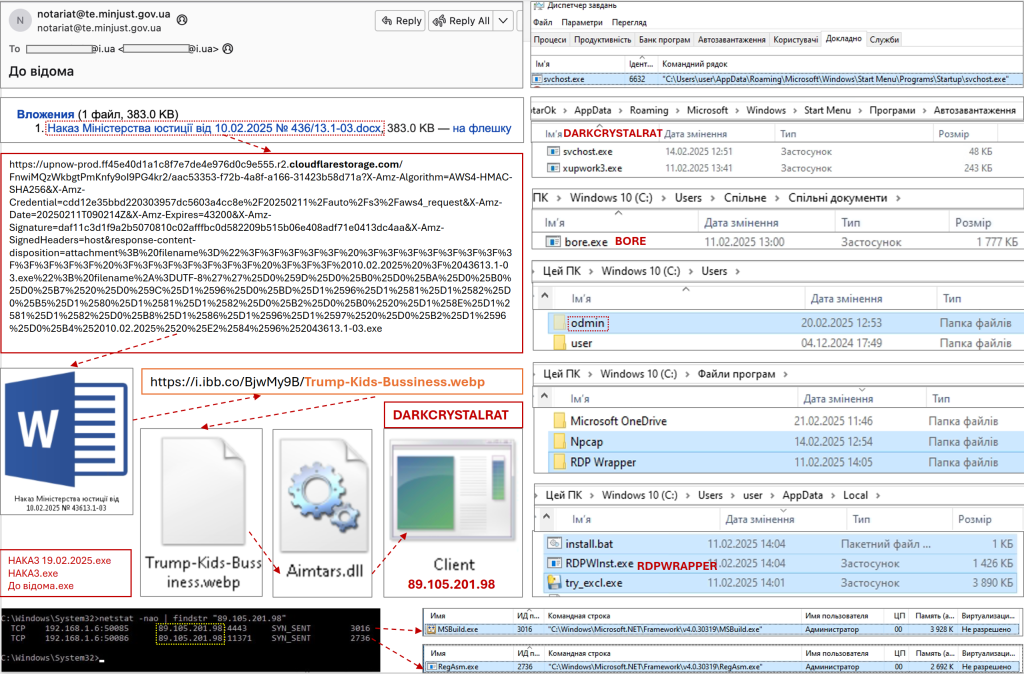
CERT-UA (Governmental Computer Emergency Response Team of Ukraine) said the threat actor became active starting mid-January 2025. On February 11, 2025, CERT-UA uncovered malicious email activities allegedly sent on behalf of the Ministry of Justice of Ukraine.
These emails contained links to download executable files, such as "HAKA3.exe" and "Order of the Ministry of Justice of February 10, 2025, No. 43613.1-03.exe."
Launching these files infects victims' computers with DarkCrystal RAT (DCRAT), a Remote Access Trojan (RAT) also used by The Russian military cyber-espionage group Sandworm (UAC-0113, APT44).
Once the initial access is obtained, attackers use additional tools like RDPWRAPPER to enable multiple remote desktop sessions and the BORE utility to establish external connections via RDP (Remote Desktop Protocol).
They also deploy programs like NMAP for network scanning, the FIDDLER proxy/sniffer to capture authentication data, and the XWORM stealer to harvest credentials from keystrokes and clipboards, deepening their access and exploiting compromised systems further.
The attackers have also weaponized already compromised systems to send more phishing emails. For this task, they employ the SENDEMAIL console utility, further expanding their malicious reach.
CERT-UA, in collaboration with the Cybersecurity Commission of the Notary Chamber of Ukraine (NPU), acted swiftly to contain the threat.
Affected computers in six Ukrainian regions were promptly identified, and several malicious plans were thwarted, even during the final stages of unauthorized notarial actions. Steps were taken to provide notaries with updated computer security configurations to reduce potential vulnerabilities.
CERT-UA emphasized that the continued demand for services to unlawfully modify state registers motivates cybercriminals to persist in their attacks.