Cyberattacks Against the Gaming Industry Rose by 340% During the Pandemic
- The number of cyberattacks against the gaming industry grew significantly last year, with actors targeting both players and companies.
- The main method used was SQL injection attacks, something that can be avoided with proper security.
- The only thing that went down was DDoS activity, although it went up in terms of severity.
The COVID-19 pandemic that has forced the global population to stay at home naturally fueled the gaming industry, and this didn’t go unnoticed or untapped by cybercrime actors. According to a report that Akamai shared with TechNadu prior to publication, the increase in attacks in 2020 compared to 2019 was 340%, and when compared to 2018, it was 415%. In fact, Akamai points out that the gaming industry saw the greatest malicious traffic increase than any other industry last year.
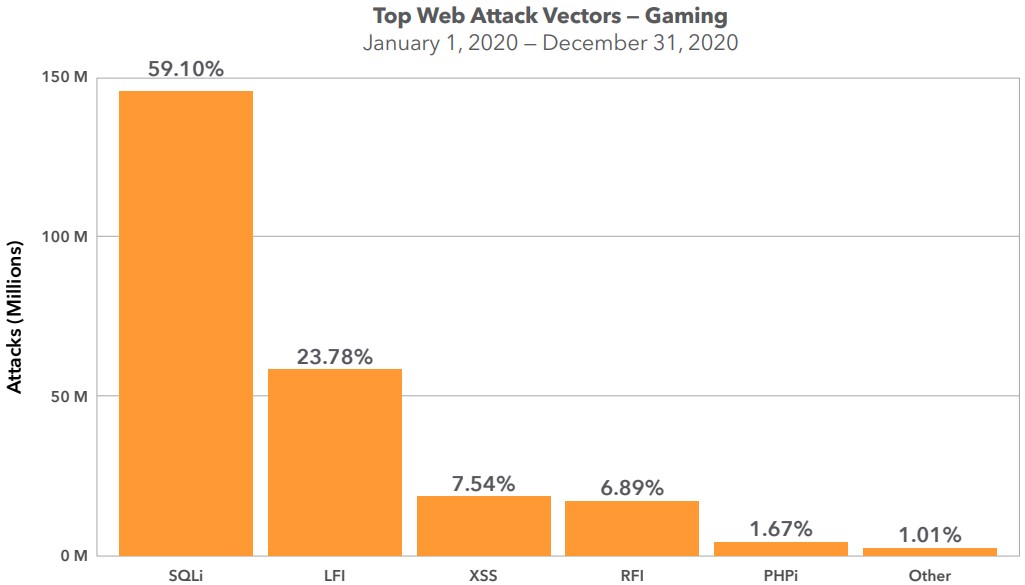
The cyber-intelligence company has gathered the data of 6.3 billion attacks, and roughly 4% of them concern the gaming industry, gamers, server infrastructure that hosts multiplayer games, etc. The most common method of attack was SQL injection, accounting for 59%, followed by LFI attacks at 24%, and XSS and RFI having smaller but still significant percentages.
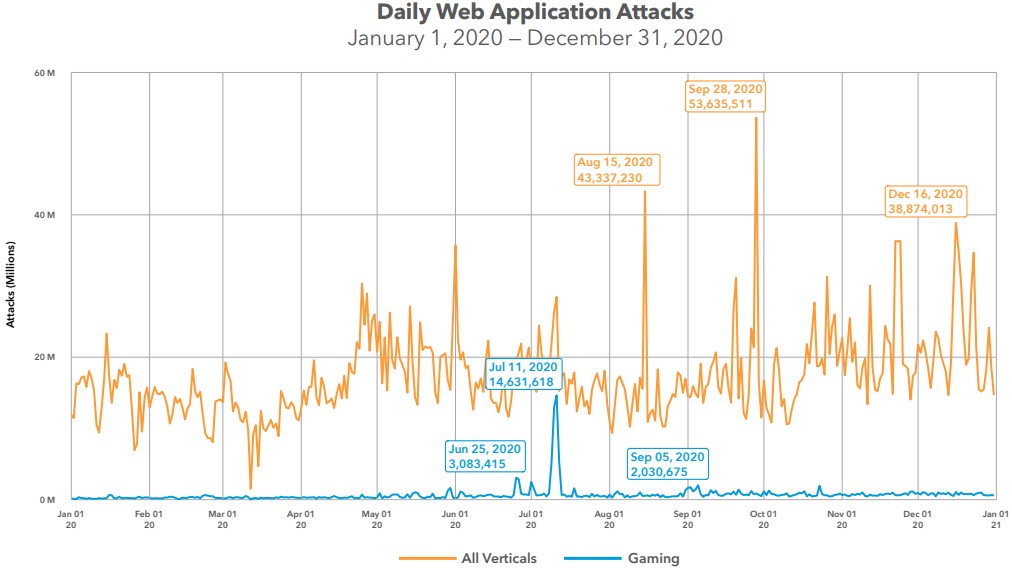
There’s a notable spike in June and July last year, which isn’t linked to the release of any highly-anticipated titles. Akamai explains that this is around the same time they observed automated SQLi and LFI tutorials circulating online, so the assumption is that many unsophisticated hackers joined in the exploit space.
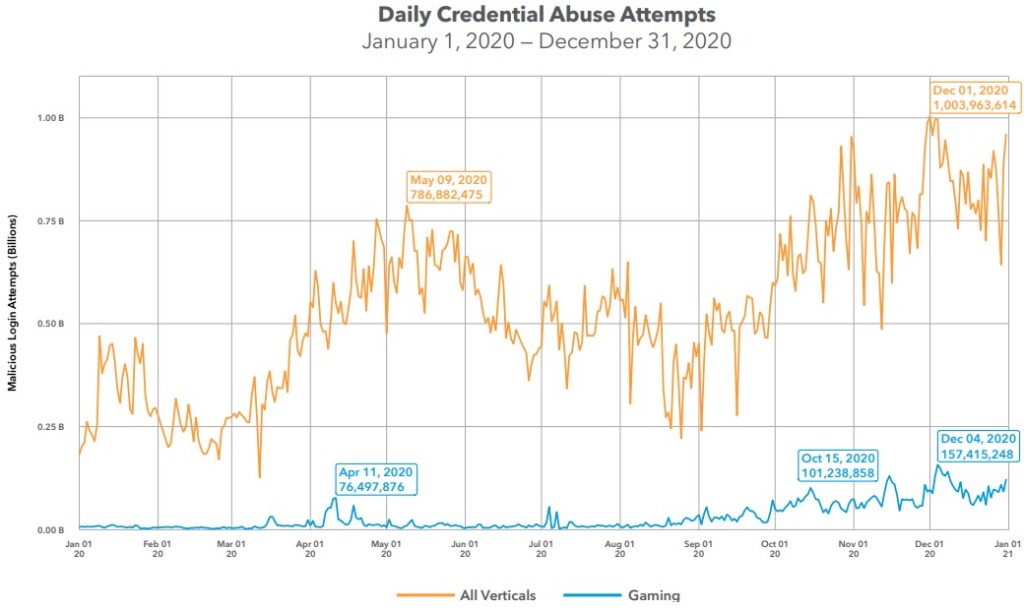
Another big problem for players and game companies, of course, is credential stuffing. Akamai’s tools logged almost eleven billion credential stuffing attacks in the gaming industry in 2020, which is an increase of 224% compared to the previous year. In this case, the December spike in activity is attributed to holiday-induced interest from buyers and hackers doing their best to satisfy demand.
Mobile gamers weren’t left alone either, as that market grew significantly last year, and cybercriminals wanted a piece of all those in-app purchases that rise to hundreds of billions. They mostly tried to set up fake “top-up” portals for popular game titles, stealing people’s money through fake purchases. Of course, stealing credentials and financial information was also included in the operations of some of these spoofed sites.
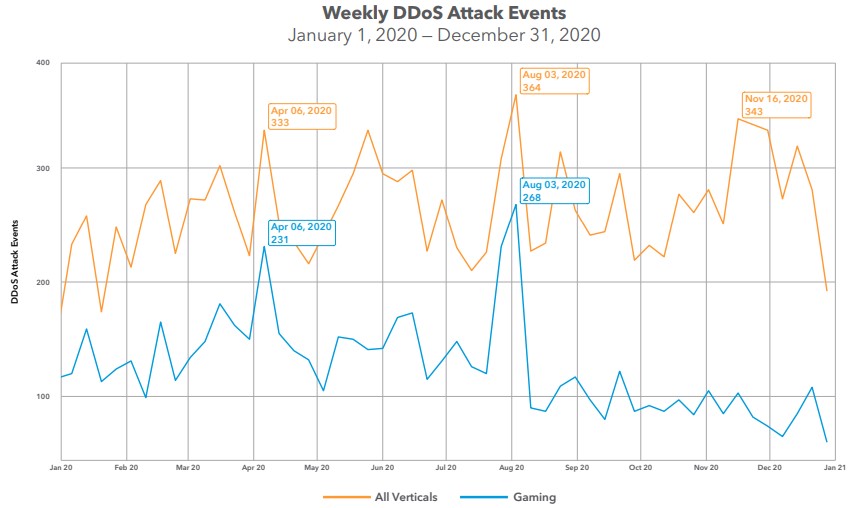
The DDoS attacks were the only aspect that went down in 2020, but that is not to say the problem was eliminated. The drop in activity was estimated to be around 20% compared to 2019 and 31% compared to 2018. The size of the attacks that took place in 2020, though, were formidable, with one mobile company suffering one that peaked at 412 Gbps, followed by a second at 392 Gbps a few days later.
The goal for DDoS actors is to extort the gaming companies and force them to pay a ransom to stop the attacks, as every hour of server downtime translates to massive revenue losses.
Last year’s situation may have caught many gaming companies by surprise, but there is no excuse for 2021. All firms need to up their game in what has to do with account protection, API security, MFA implementation, and anti-spoofing programs.