Unknown Cyberattackers Bricked Over 600,000 US Routers in October 2023
- Black Lotus Labs’ cybersecurity experts recently discovered that a cyberattack destroyed a large number of routers in the US last year.
- The threat actors targeted devices belonging to a single internet service provider in the US telecommunications sector.
- The research says a commodity RAT was the primary payload responsible for the event.
An unidentified hacking group orchestrated a colossal cyberattack on a telecommunications company in the U.S. last year, decimating hundreds of thousands of Internet routers belonging to a single Internet Service Provider (ISP). This alarming incident was uncovered by Lumen Technologie’s Black Lotus Labs security analysts, who detected the attack in recent months.
The attack took offline more than 600,000 small office/home office (SOHO) routers. The Black Lotus Labs investigation revealed that the incident took place over a 72-hour period between October 25 and 27, when 49% of all modems from the impacted ISP’s autonomous system number (ASN) were suddenly removed – which was backed by public scan data repository Censys for ActionTec.
The affected modems were Sagemcom and ActionTec models, but no exploits were listed for the two models when searching for exploits in OpenCVE for ActionTec.
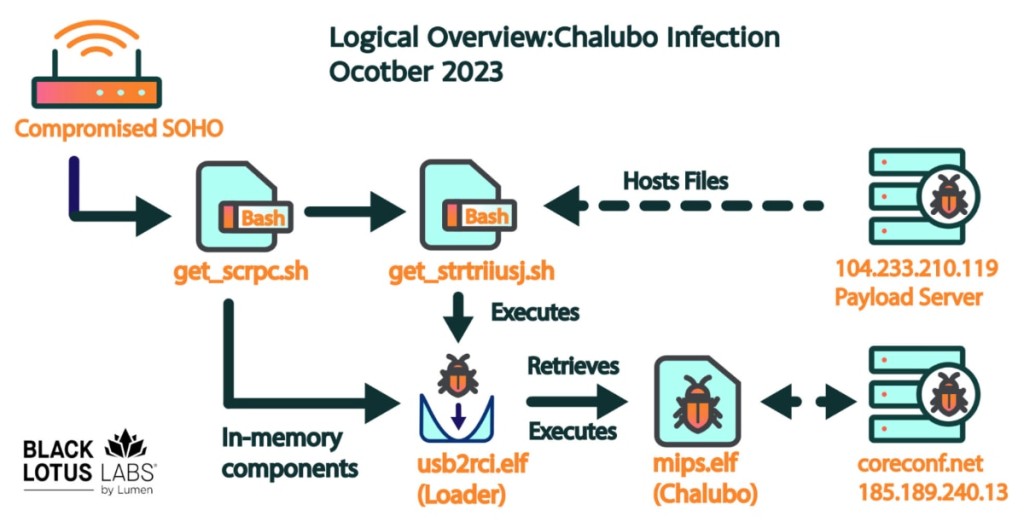
The cyberattack left the infected devices permanently inoperable and in need of a hardware-based replacement. The published report shows the primary payload responsible for the event was a commodity remote access trojan (RAT) identified as Chalubo, which first came to light in 2018.
Black Lotus Labs said the Chalubo malware family was highly active in November 2023 and remained so into early 2024. The researchers suspect the threat actors chose a commodity malware family to obfuscate attribution instead of a custom-developed toolkit and that the malicious firmware update was intended to cause an outage.
Chalubo has payloads designed for all major SOHO/IoT kernels and pre-built functionality to perform DDoS attacks. The RAT, which was not written specifically for destructive actions, was used as IoT malware that expertly hides its activity.
Chalubo can execute any Lua script sent to the bot, encrypt all communications with the command and control (C2) server, remove all files from the disk, and change the process name to a random creation of the same length as the original process name already present on the device.
A sizeable portion of this ISP’s service area covers rural or underserved communities, where recovery from any supply chain disruption takes longer. Residents may have lost access to emergency services, critical information from remote crop monitoring, and health care records.
Black Lotus Labs researchers said this kind of attack had only happened once before, when AcidRain was used as a precursor to an active military invasion.