Custom 404 Pages Are Used by Crooks to Steal Microsoft Credentials
- Phishing actors are using custom 404 webpages on Microsoft Azure to steal Microsoft accounts.
- From a practical perspective, they only register a single domain and add many fake 404 pages.
- Careful visitors would notice a couple of clear signs of fraud, but many still wouldn’t.
As reported by Quickheal, there’s a new trend that wants phishing actors creating custom “404 Not Found” error webpages to trick their visitors into entering their Microsoft login credentials. It sounds a bit counter-intuitive, but the truth is that the very fact that the method is so uncommon makes it effective. Moreover, the way that these actors are using the 404 errors makes it especially hard for their victims to suspect that something shady is going on.
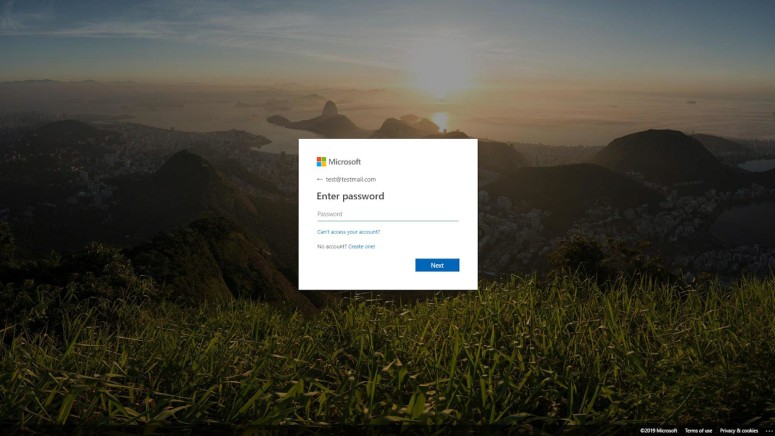
404 error webpages can be configured to show anything to the visitor, and in the case of these campaigns, they are designed to look like the real Microsoft account sign-in pages, asking people to enter their credentials. The actors are randomizing the domains that are using for their campaigns exponentially and can have virtually unlimited phishing URLs on a single domain. Every time a potential victim is browsing on the actors’ domain and tries to visit a non-existent webpage, they will be served with the phishing page.
These most recent campaigns are possible thanks to the support for custom 404 pages that are provided by Microsoft Azure Blob Storage. Actors are using this solution for their malicious purposes, and at the same time, they are targeting Microsoft Azure Directory, Office 365, Skype, and Outlook accounts. Their SSL certificates will be signed by Microsoft, and the only thing indicating that things aren’t what they seem to be is the fact that the cookies notification which should be at the top of the page is missing, as are the “sign-in options”.
The 404 Not Found page tells you that you’ve hit a broken or dead link – except when it doesn’t. Phishers are using malicious custom 404 pages to serve phishing sites. A phishing campaign targeting Microsoft uses such technique, giving phishers virtually unlimited phishing URLs.
— Microsoft Threat Intelligence (@MsftSecIntel) August 13, 2019
While this was nailed down by the Microsoft Security Intelligence team recently, it doesn’t mean that Azure is the only service that offers the ability to customize 404 errors, nor that this feature will now be retracted because it is getting abused. Other “exploitable” services include Amazon, Weebly, Squarespace, and a lot more, so people should have their eyes open and be very careful when they are asked to enter their credentials. Watch out for URLs that don’t make sense, consider how you ended up at that page in the first place, check for the lock icon and the “https” on your browser, use a password manager that won’t be fooled into filling your credentials on webpages that it shouldn’t, and use an up to date AV tool with web protection.
Do you have anything to report about campaigns of this type? Feel free to share the details with us in the comments section down below, or on our socials, on Facebook and Twitter.