Cryptocurrency Miner Hidden In Fake Adobe Flash Updater Discovered
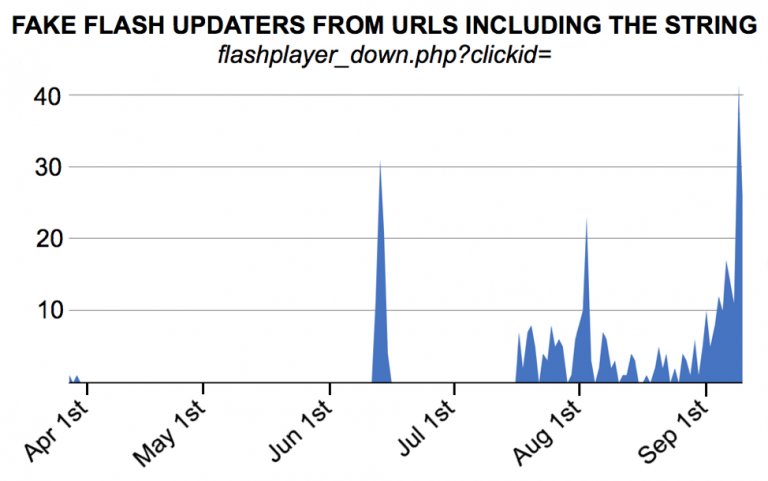
- According to Palo Alto Networks, the security firm has found 113 instances of a cryptocurrency miner in August.
- The cryptocurrency miner is built into a fake Flash updater which looks exactly like the official variant.
- The update comes with the XMRig miner built incapable of mining cryptocurrency on victims’ systems.
Despite the cryptocurrency craze dying down a little compared to last year’s boom, cybercriminals are still at large trying to mine cryptocurrency on other people’s systems. There have been a large number of reports of cryptocurrency miners being deployed onto apps and the latest miner to be discovered is the XMRig malware.
The XMRig malware was discovered by Palo Alto Networks, and it seems like the miner is built into a fake Flash updater. The user interface of the malicious program looks exactly like the official Flash updater from Adobe, making it difficult for users to differentiate it from the official version. Since the malware also updates a victim’s system to the latest version of Adobe Flash, it makes things even less suspicious.
Image Courtesy of Palo Alto
Palo Alto Networks was searching for fake flash updates and found 113 instances of malware that meet the search criteria. Tests were run by the security firm on Windows 7 Service Pack 1, and the OS correctly identifies it has an app from an unknown publisher. It is quite possible that users have downloaded the malware despite the warnings due to how legitimate the app looks.
It is not just cybercriminals who gave into the crypto craze since last year, even popular services like Starbucks and The Pirate Bay were caught deploying cryptocurrency miners on their websites to make extra money. Platforms have become very vigilant about these miners, and Apple has officially put a ban on them on the tech giant’s iOS platform, but they continue to be popular on platforms like Windows. If you ever see a suspicious app and get a warning about it being from an unknown publisher, it is recommended that you do not proceed with the download and do a thorough scan first.
What do you think about the cryptocurrency miner built into the fake Flash updater? Let us know in the comments below. Also, don’t forget to follow us on Facebook and Twitter. Thanks!