North Korean Hackers Target Cryptocurrency Users on LinkedIn with RustDoor Malware
- LinkedIn users continue to be targeted by North Korean hackers, this time in a new malware campaign.
- The threat actor focuses on cryptocurrency users and tries to persuade them to access malicious documents.
- The yet unnamed cybercriminals use fake job offers and bogus coding challenges as a lure.
A new wave of attacks orchestrated by North Korean threat actors targeting professionals on LinkedIn who use cryptocurrency was observed by cybersecurity experts Jamf Threat Labs in a recent advisory. The hackers were seen employing a relatively new malware named RustDoor.
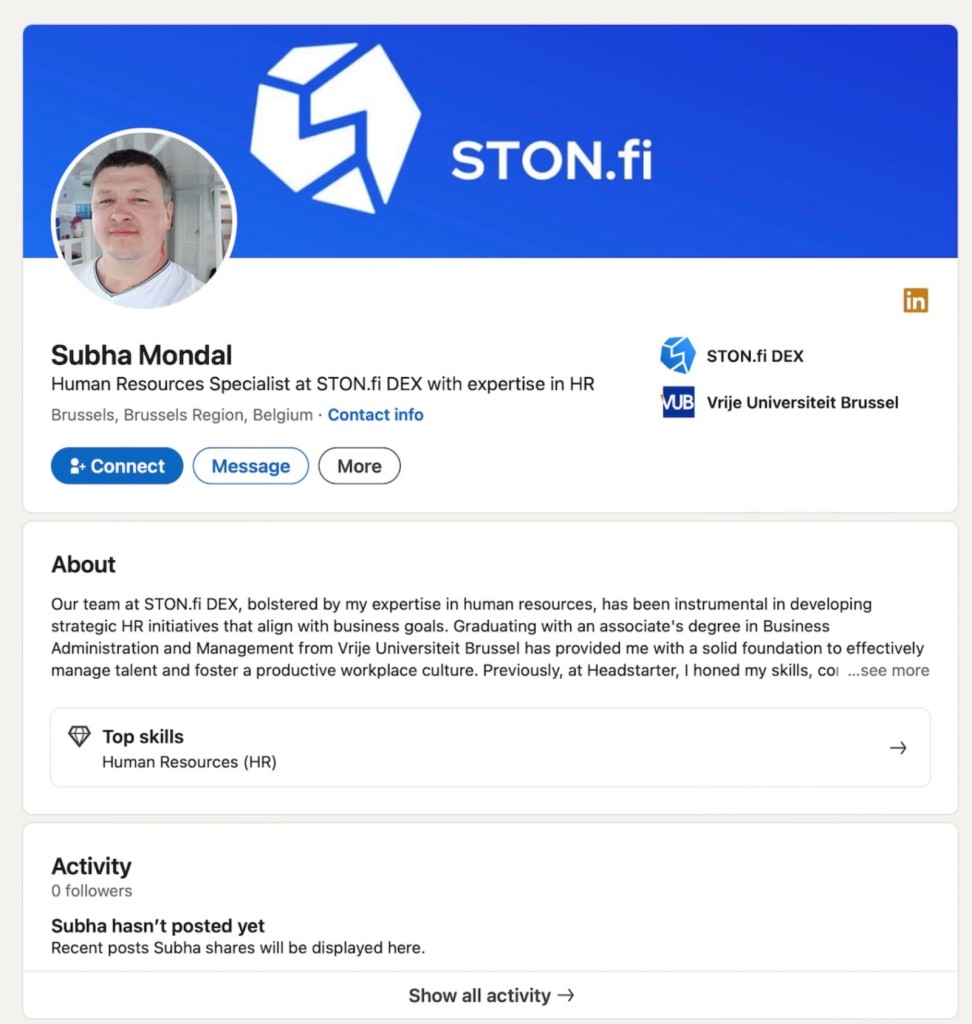
The attackers, masquerading as recruiters from legitimate decentralized cryptocurrency exchanges like STON.fi, engage potential victims through LinkedIn. Their strategy is to lure individuals into what appears to be genuine job offers or coding assignments.
This multi-layered campaign highlights the adversaries' intricate social engineering techniques, designed to infiltrate enterprise networks under the guise of professional opportunities.
RustDoor, a formidable macOS backdoor that disguises itself as an update for Microsoft Visual Studio and permits unauthorized access to sensitive data and critical systems, is delivered via booby-trapped Visual Studio projects, pretending to be coding challenges.
Upon execution, these projects deploy multiple payloads, namely "VisualStudioHelper" and "zsh_env," which maintain persistence by embedding themselves into system configurations.
Notably, the malware remains undetected by most anti-malware engines, complicating the detection process for targeted organizations.
Among the key indicators of compromise in these attacks are requests to execute unfamiliar code or download applications onto company devices. Such actions, masked as 'pre-employment tests' or debugging exercises, are critical red flags.
Additionally, attackers may seek to execute non-standard packages or scripts from repositories like Node.js and GitHub.
This attack is part of a larger series of attacks on LinkedIn. Threat actors affiliated with North Korea have been seen deploying the COVERTCATCH malware through deceptive job recruitment schemes, targeting developers in decentralized finance (DeFi) and the wider Web3 sector.
The U.S. Federal Bureau of Investigation (FBI) has highlighted the sophistication of these campaigns, emphasizing the need for heightened vigilance among decentralized finance (DeFi) and cryptocurrency businesses.