Critical Zero-Day Vulnerability in Bubble.io Exposes User Data Across Major Enterprises to Risk
- A Bubble.io vulnerability was found in its use of Elasticsearch and cryptographic mechanisms.
- The flaw allows executing arbitrary requests, exfiltrating entire databases, and enumerating and profiling customer subdomains.
- What’s more, it also permits attacking other Bubble.io-hosted clients due to shared infrastructure.
A critical zero-day vulnerability in Bubble.io, the no-code platform for AI-based app development and publishing, exposes high-profile clients to serious data security risks. Despite security researchers’ repeated attempts to alert Bubble, the concerns remain unaddressed.
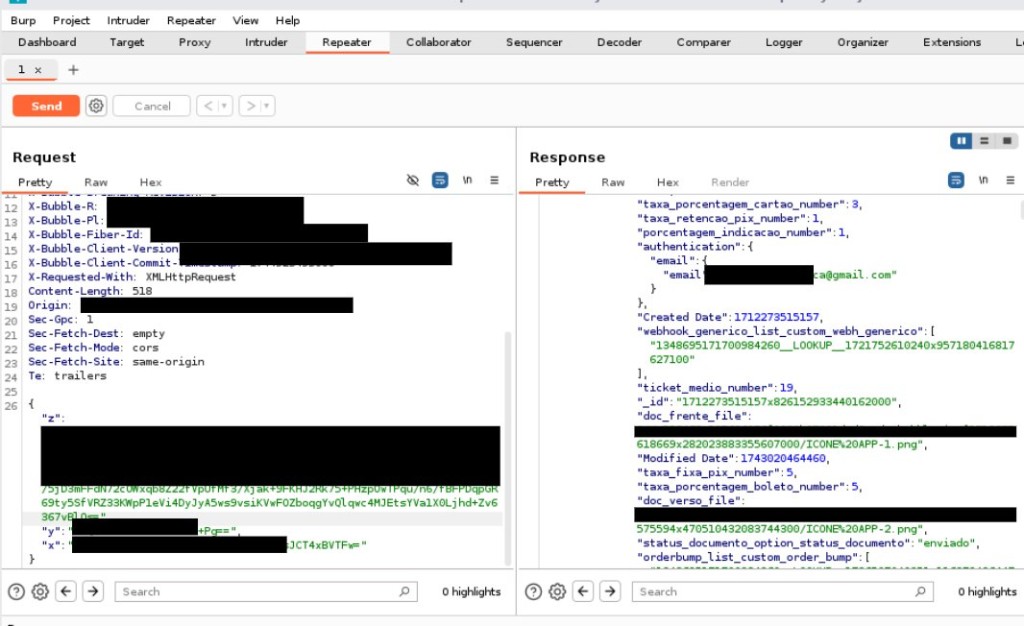
The vulnerability was detailed in a research repository on GitHub and reveals significant flaws in Bubble.io’s integration with Elasticsearch, a popular database search engine.
Popular enterprises relying on Bubble.io for app development, including Danone, SeaGate, Unity, Shopify, Paramount Pictures, HubSpot, Amazon, PWC, Yamaha, and L'Oreal, are now vulnerable to data breaches caused by these exploits.
By reverse-engineering Bubble.io’s JavaScript code and inspecting HTTP headers, the researchers discovered the exploitation vector, granting attackers the ability to execute arbitrary queries against the Elasticsearch database.
The exploit leverages the following issues in Bubble.io’s platform:
- Fixed Cryptographic Keys: The platform uses non-rotating Initialization Vectors (IVs), shared across all clients, allowing attackers to craft arbitrary payloads for Elastic queries.
- Encryption Workflow in Frontend: Encryption is handled in the front-end, where weak cryptographic practices are exposed to attackers.
- Lack of Timestamp Validation: The flaw includes the absence of proper timestamp verification in the payload.
- Subdomain Enumeration: Fuzzing the *.bubbleapps.io domain allows attackers to enumerate customer subdomains.
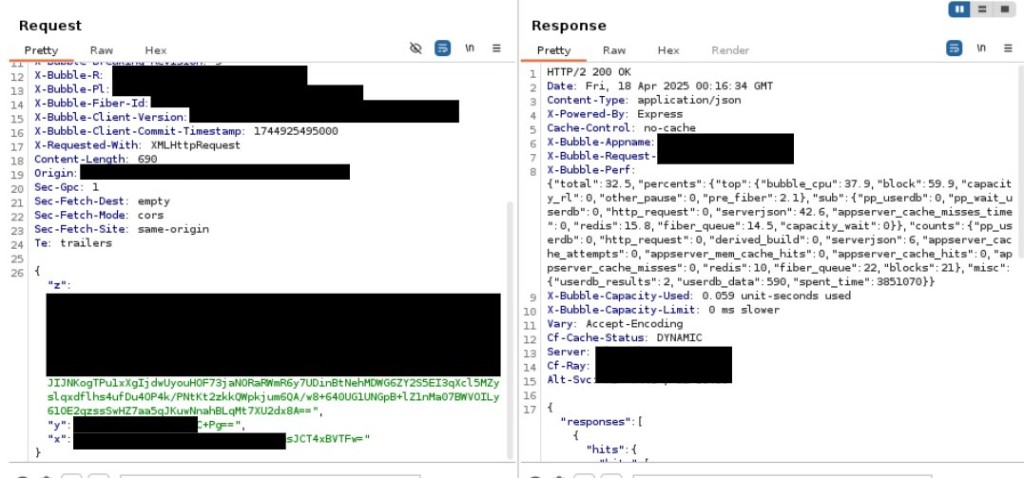
- Response Header Exposure: Even if targets are misidentified, the platform’s X-BUBBLEAPP-NAME response header reveals the correct target domain.
The above issues provide attackers with the ability to execute arbitrary requests, bypassing the platform’s access restrictions, and dump and exfiltrate entire databases, including custom-defined tables.
They can also attack other Bubble.io-hosted clients due to shared infrastructure and enumerate and profile customer subdomains to identify high-value targets.
Researchers Lucca and Pedro publicly disclosed these vulnerabilities only after Bubble.io ignored their private disclosures. Following months of silence, the researchers presented their findings through talks, a proof-of-concept (PoC) script, and an in-depth research paper.
The disclosed material demonstrates how attackers can exploit these flaws to obtain sensitive customer or company data.