Critical Security Vulnerabilities Found in Zyxel USG FLEX H Series Firewalls Could Compromise Systems
- Security researchers have uncovered vulnerabilities in Zyxel’s USG FLEX H Series firewalls.
- The vulnerabilities hinge on improper file handling and relaxed permissions, allowing unauthorized system control.
- These could allow local privilege escalation and potentially compromise entire systems.
Newly discovered USG FLEX H Series firewalls flaws centered around Zyxel’s Linux-based operating system (uOS) that could leave enterprise networks exposed have been assigned the identifier CVE-2025-1731.
The USG FLEX H Series firewalls, known for their high performance and advanced features for enterprise and high-speed networks, are vulnerable due to misconfigured permissions and improper privilege management, HN Security said in a recent report.
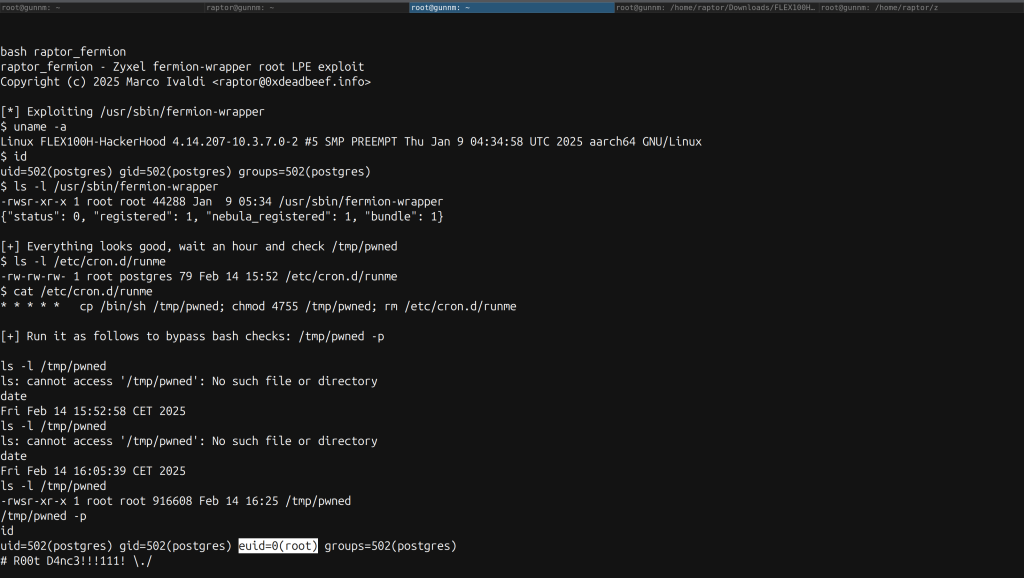
The primary vulnerability stems from the misuse of a setuid root binary distributed with the system. When executed with the argument register-status, the binary follows symbolic links in the /tmp directory, allowing attackers to create or overwrite files and escalate privileges from a low-privileged user to root.
The /tmp directory lacks the "sticky bit" permission, which enables attackers to replace files even if they are owned by other users, including system-level accounts. This oversight significantly simplifies exploitation by removing critical safeguards.
The proof-of-concept exploit aims to show how attackers could leverage these vulnerabilities to achieve local privilege escalation. It involves creating symbolic links in the /tmp directory, enabling unwarranted file overwrites and eventual control of critical system components.
The lack of the sticky bit further exacerbates the risks by making all files in /tmp vulnerable to replacement or tampering.
The researchers tested and verified the vulnerabilities on Zyxel USG FLEX 100H (Firmware Version 1.31[ABXF.0]) and Zyxel USG FLEX 200H (Firmware Version 1.31[ABWV.0]), but other Zyxel products or earlier firmware versions may also be affected.
Zyxel has acknowledged the vulnerabilities and released a firmware update, Version 1.32, to address the identified issues.
However, a key point of contention arose between the researchers and Zyxel over assigning separate CVE IDs for the local privilege escalation vulnerability, as the company chose to group the issues under CVE-2025-1731, arguing they originate from common root causes.
Additionally, Zyxel did not consider the lack of the sticky bit on the /tmp directory a security vulnerability, labeling it an implementation flaw. They have requested further evidence to demonstrate how this issue could result in a denial-of-service (DoS) attack.