Critical Infrastructure on the Line Due to Industrial VPN Flaws
- Researchers discovered three critical flaws affecting industrial VPN and access system tools.
- The vulnerabilities enable malicious actors to carry out remote code execution attacks.
- Patches have been made available since a couple of weeks ago, but so are the PoC exploits.
Researchers at Claroty have discovered a set of remote code execution vulnerabilities that affect VPN tools used in industrial settings. Those would include water and electric utility services, waste management plants, the oil & gas industry, and generally the highly-critical sector that is crucial to society’s well-being.
These plants use ICS (Industrial Control Systems), PLCs (Programmable Logic Controllers), and IO (Input/Output) devices that generally make up their SCADA, and VPNs are meant to help carry out remote operation adjustments and system monitoring securely. Unfortunately, the existence of flaws in these VPN tools enables remote access and exploitation, with the consequences being potentially catastrophic.
Related: Report Claims Hacking Critical US Infrastructure Would Be Fairly Easy
Source: Claroty
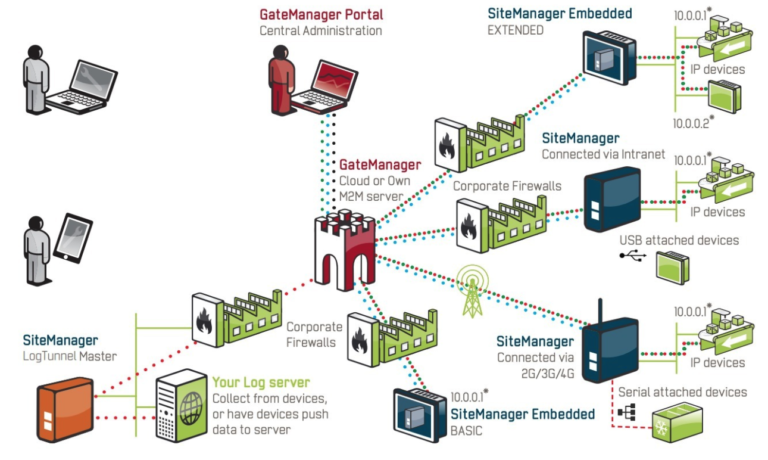
Starting with “CVE-2020-14500”, this is a critical vulnerability affecting the ‘Secomea GateManager’ remote access server. Improper handling of the HTTP request header allows an attacker to engage in remote code execution without authenticating on the network.
Not only does this flaw enable actors to gain access to a company’s internal network, but it would also allow them to decrypt all network traffic that passes through the VPN. Secomea was informed of this in May 2020 and released a fixing patch on July 16, 2020.
Source: Claroty
The second critical discovery is “CVE-2020-14511,” which affects the ‘Moxa EDR-G902/3’ industrial VPN server. The flaw could allow a specially crafted HTTP request to trigger a stack-based overflow that again results in remote code execution without the need to authenticate. Claroty researchers found this flaw in April 2020, and Moxa fixed it with a patch in June 2020.
The third vulnerability is “CVE-2020-14498,” which affects ‘HMS Networks eWon.’ This is a VPN device that connects with the ‘eCatcher’ client, enabling remote operators to access the industrial systems and make subtle adjustments. Unfortunately, the existence of the stack-buffer overflow bug opens the door to using a specially crafted malicious HTML element, leading to remote code execution with admin privileges. Claroty informed HMS Networks of the issue in May 2020, and the vendor released a fixing patch on July 14, 2020.
Source: Claroty
All in all, the patches have been available for two weeks now, so system administrators are urged to apply the updates as soon as possible. COVID-19 has pushed employees out of industrial plants to work from home, but this trend has increased hackers’ interest.
Critical industrial infrastructure should remain secure under all circumstances, especially now that several “proof of concept” methods for exploiting the above flaws are available online, and more details are to be presented in the upcoming 2020 DEF CON.