Confucius APT Is Exploiting the “Pegasus” Spyware Worries to Trick Pakistanis
- Indian actor Confucius was spotted using “Pegasus” lures to trick Pakistanis into opening laced documents.
- The spear-phishing email campaign uses addresses that are made to appear as if they belong to the Pakistan government.
- The end result is an infection with a NET DLL info-stealer that grabs images and documents from the user’s folders.
The pro-India actor known as ‘Confucius’ has been noticed using lures relevant to the “Pegasus” Israeli spyware tool, spreading malicious documents through spear-phishing email campaigns. The actors' goal appears to be to compromise Pakistani people who are linked with ideas and groups thought to be of high risk for India's national security. As such, the spoofed origin used for distributing the emails is generally nationalistic, impersonating the Pakistani Armed Forces or even the government.
The relevant report comes from Trend Micro, who sampled quite a few emails distributed by the ‘Confucius’ APT from the following email addresses. All emails were sent via a Pakistan-based ExpressVPN server in order to not raise any alarms and achieve better distribution rates.
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
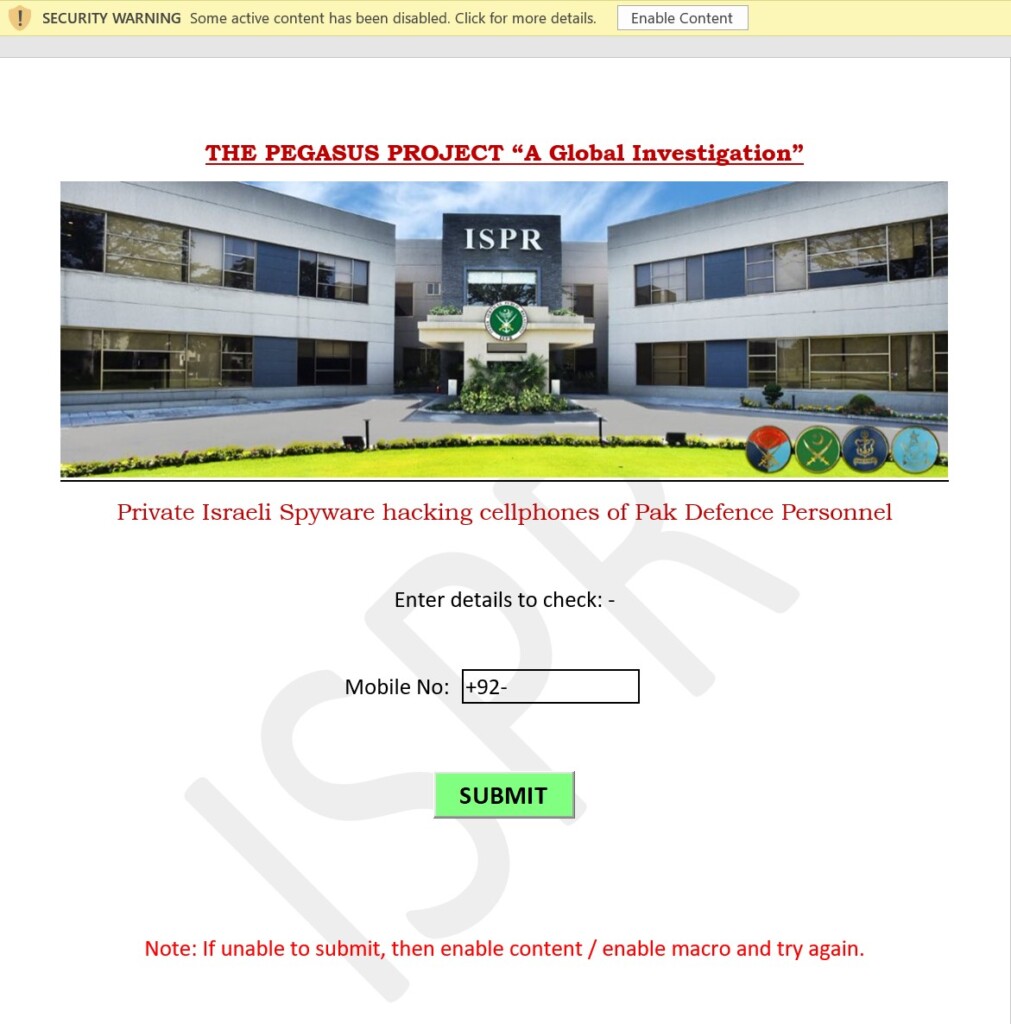
The email content is something that would trigger the interest of the recipient, like, for example, the Pegasus spyware and how it can infect phones through click-less and totally stealthy attacks. If the victim clicks on the link hoping to read the document containing the details, they end up seeing a document that attempts to trick them into enabling content to let the malicious macros run loose on their system.
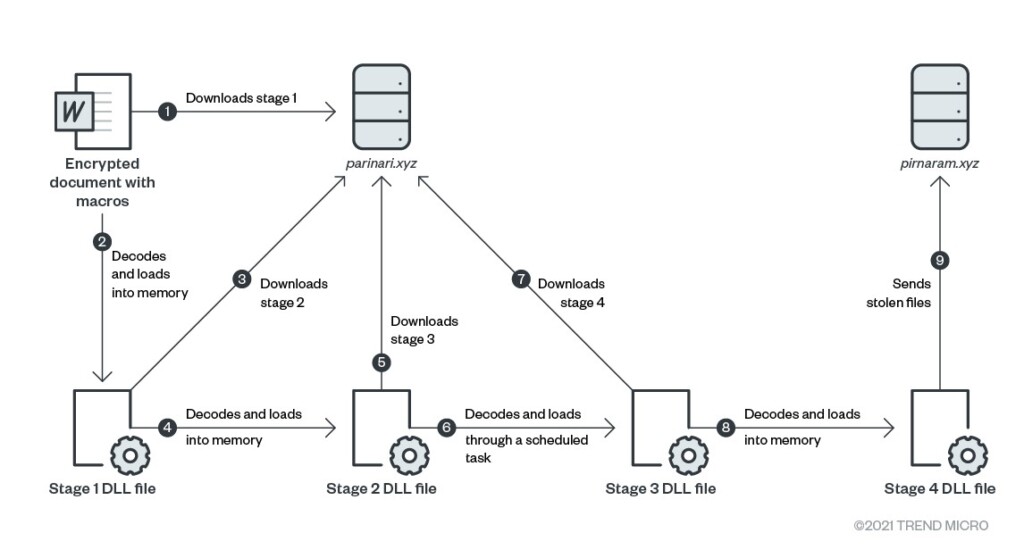
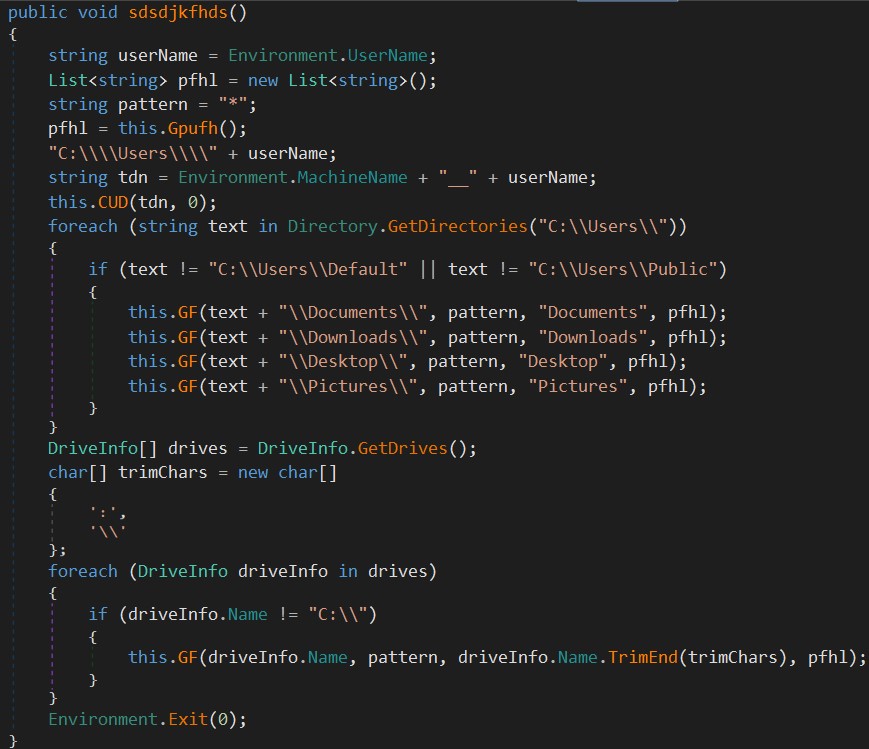
If the victim reaches this unfortunate step, a series of DLL files are decoded and loaded into memory, and eventually, a file-stealer is dropped onto the victim’s machine. That final payload is also a NET DLL, which is designed to steal a wide range of document and media files from the folders “Documents,” “Downloads,” “Desktop,” and “Pictures” of every user who has an account on the Windows system.
Everything is sent to the C2, currently on “pirnaram[.]xyz”. The exfiltration of the data isn’t done through PHP scripts but via FTP server instead, providing better stealthiness to the operation.
In February, the Lookout Threat Intelligence team discovered two new Android spyware samples that appeared to belong to ‘Confucius,’ namely the “Hornbill” and “SunBird”. These two were again spoofing popular Pakistani apps like the ‘Kashmir News’ and ‘Quran Majeed,’ aiming to steal information from the compromised smartphones. It is clear that the particular actor is insisting on the same targeting habits but constantly updates the scope and methods.