Comcast Exposed Passwordless Development Database of 478 GB Online
- A security researcher has discovered an accessible Comcast development database holding sensitive data.
- The exposed information includes network blueprints, logs, credentials, pathways, and more.
- Comcast was quick to secure the leaking instance, but this may not be enough.
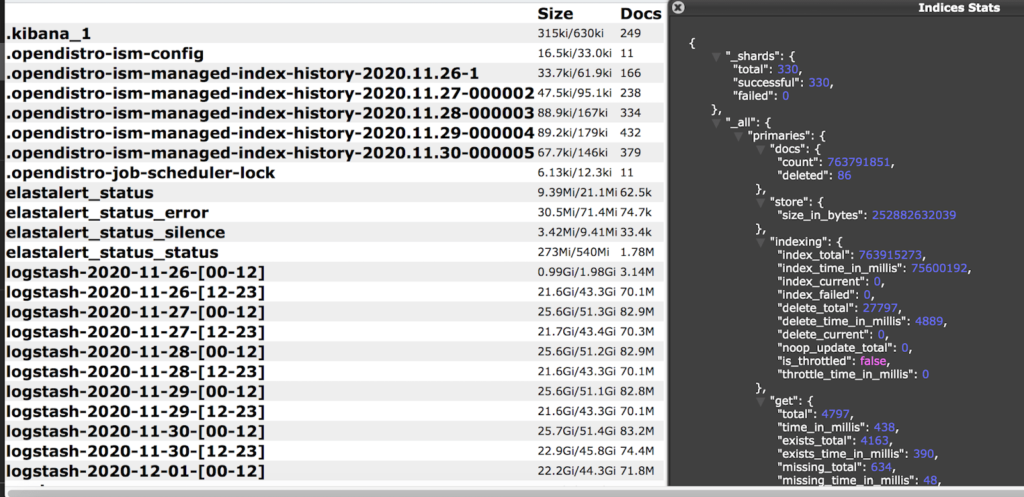
Comcast, the American telecommunications giant, has exposed 1.5 billion records of a total size of about 478 GB online after they misconfigured a development database to be accessible without a password. The discovery of the database is the work of security researcher Jeremiah Fowler, who responsibly reported the finding to Comcast and received an immediate response from them.
Although the action to restrict access to the data was completed in about an hour, it is possible that malicious actors were able to access and download sensitive details before the data was secured.
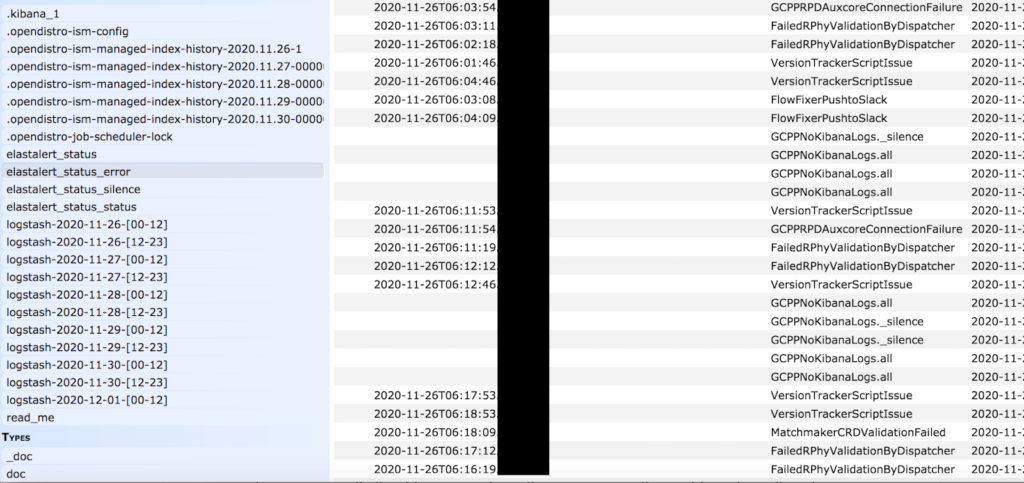
The database contained internal development and testing data, and so sensitive internal network systems, configuration settings, IP addresses, logs, ports, pathways, storage info, and various stuff that could be used for deeper network infiltration was irreversibly exposed. Additionally, the researcher saw the email addresses and hashed passwords of Comcast’s development team, job scheduling records, cluster names, device names, internal rules, node names, and a blueprint of the network's entire structure.
There is no indication that the particular database held any client details, so we can confidently say that this incident should raise no concerns to Comcast customers. However, if hackers were to use the exposed details against the internet giant, they could access a wider set of data, move laterally, and create a very troublesome situation for the firm and its clients.
We’re not saying that this is the case here, but excluding that possibility would be naive. Also, if it wasn’t for Fowler, Comcast may not have realized this incident in time, and hackers would have the margin to move around its network unobstructed.
Comcast has had a pretty damaging security incident last March, exposing approximately 200,000 subscribers of the ‘Xfinity’ service by listing them on an online catalog. These customers were actually paying an extra $5.5 per month specifically for keeping their contact details undisclosed to the public, so the blunder was huge. In 2018, a similar incident exposed the SSNs and home addresses of 26.5 million Xfinity customers.
Of course, as long as humans are involved in configurations, dealing with errors that expose data is inevitable. The size of Comcast, though, makes these errors very damaging, potentially affecting a large number of subscribers and corporate clients. That’s why these companies should follow certain security checklists, have additional teams perform double-checks, and do everything possible to minimize exposure risks.
Update February 4, 2021 - A Comcast spokesperson has reached out and shared the following statement with us: