Phishing Campaign Stole Coinbase Users One-Time Passwords
- Hackers are starting to use smarter techniques, and we can see that in phishing scams targeting Coinbase users' OTP.
- The actors set up a fake Italian-language website and managed to seal 870 Coinbase user login details.
- SMS-based OTP theft is becoming increasingly common in cryptocurrency markets.
A cybersecurity firm discovered a recent phishing campaign targeting Coinbase that tried to steal one-time passwords (OTP) from users in a more innovative way. The hackers used brute forcing to determine which email addresses were in the website's database, targeted the existing ones, and directed them to a spoofed site to collect other details.
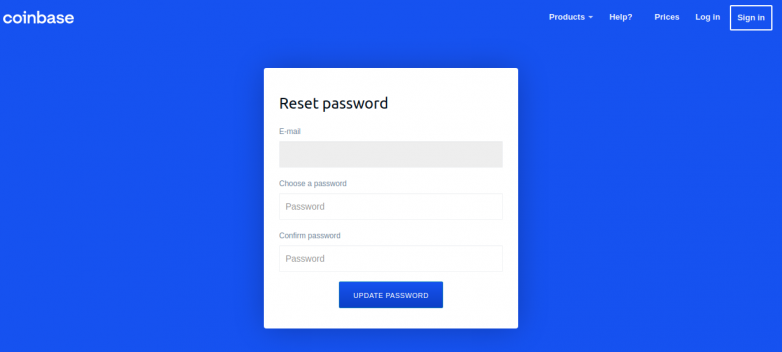
Since the site’s default language is Italian, the defunct phishing domain "coinbase.com.password-reset[.]com" attempted hacking into Coinbase's Italian user database. The hackers used 2.5 million Italian users' email addresses to discover which among them had pre-existing Coinbase accounts. The attempt here was to have emails bounce off the Coinbase user registry. In doing so, the emails with registered Coinbase accounts would show up, and the hackers could then target them with phishing emails.
As per Alex Holden, the founder of Hold Security, based out of Milwaukee, Wisconsin, this cybersecurity attack succeeded fairly well. Holden’s team managed to recover a majority of these usernames and passwords and found that almost all the emails ended with the domain name “.it”. The scammers tried bouncing hundreds of thousands of emails off Coinbase's registry every day, going for 216,000 emails on October 10.
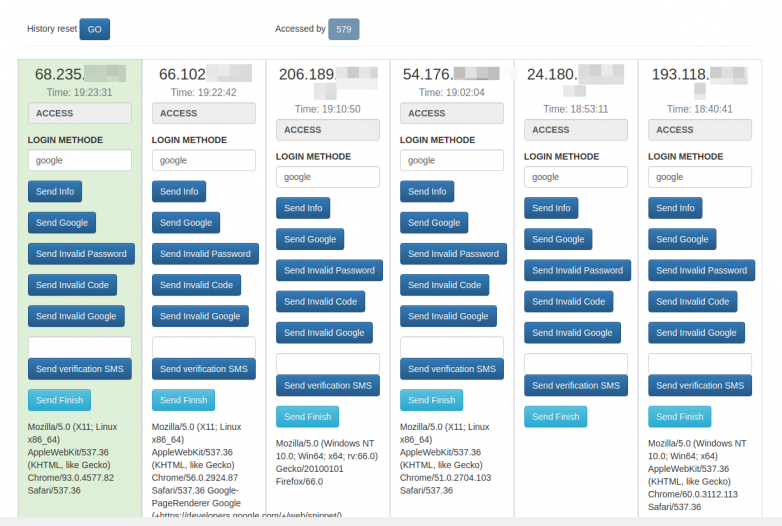
While researching the suspect domain, Holden’s team also got a look at some shoddily hidden file systems, including the admin page. The phishing attacks launched by the scammers got them as many as 870 login credential sets before the spoofed website went offline. As Holden explains it, this admin panel was synced in with a phishing page they used for extracting user login details.
After discovering Coinbase users’ emails by using them to create new accounts, the scammers would include the rejected ones in the phishing email campaign. When the soon-to-be victim would arrive on the page, the admin page made a ‘ding’ to notify the hacker at the other end. Once the victim entered their credentials, the phishers manually pushed a button that prompted the page to seek more info from the victim.
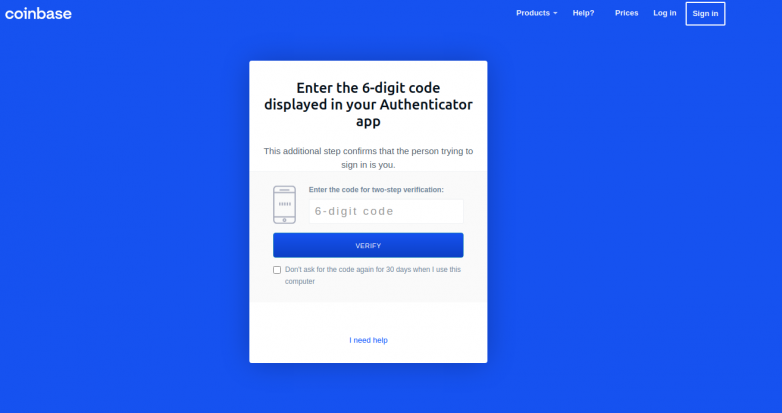
This is where they asked for one-time passwords the victims had received via their mobile apps. The page’s “Send Info” button would also ask the victim for other information like name, date of birth, and street address. The hackers could launch an SMS-based attack that asks the victim to text back their Coinbase login OTP using this data. So far, there is no official statement by Coinbase on these findings.
Coinbase is the world's second-largest cryptocurrency trading platform, having 68 million users across 100 countries, and since OTPs serve as a crucial security element essential for verifying the identity of the person logging, it makes sense to be in phishers' crosshairs. Even though the company has a robust security system based on machine learning models, combines cutting-edge bot detection and abuse prevention, and has dedicated Threat Intelligence and Trust & Safety teams that monitor new cyberattack techniques, preventing OTP-based low-tech phishing scams is very challenging.
In September 2021, Coinbase declared malicious actors successfully stole cryptocurrency from 6,000 customers using the SMS multi-factor authentication feature’s vulnerabilities to perpetrate these cyberattacks. Of course, there are many other attempts on other domains when it comes to stealing access to crypto accounts.