Clover Sites Was Leaking Customer Data For At Least Seven Months
- Clover Sites failed to secure two client-exposing databases after they received twenty notifications.
- The admins falsely believed that they had already secured them a while back.
- Customers of the platform had their real names, addresses, and four credit card number digits exposed.
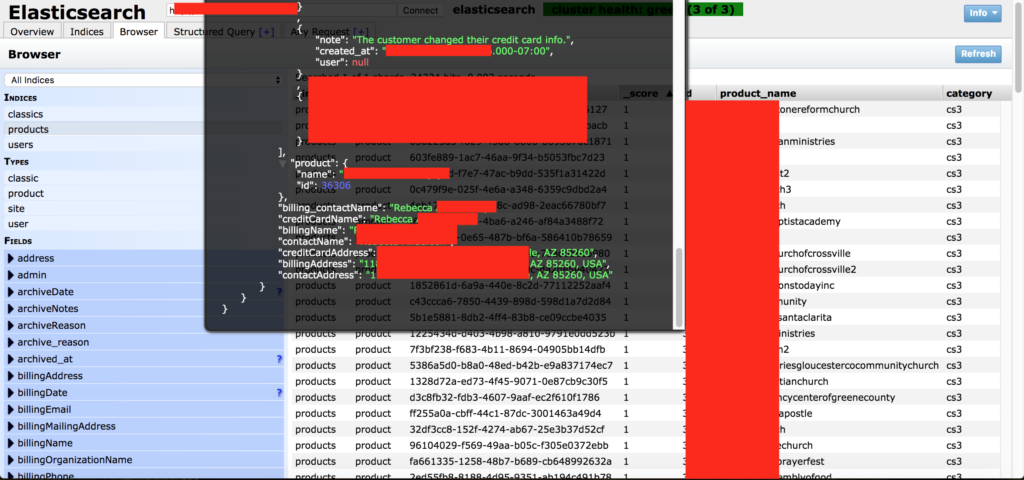
Researcher Jeremiah Fowler of Security Discovery comes with a staggering revelation about Clover Sites. The church website creator service has left two databases exposed to the public, and non-password protected. The two databases contained the same dataset, which consisted of the detailed records of 65800 clients of the service. The data that was exposed includes customer names, IP addresses, email addresses, the last four digits of their credit card numbers, internal calls, help requests, and many other details about present and past accounts. All of this information was stored in plaintext, so there was no encryption to make the data harder to exploit.
As religious websites are usually combined with donation platforms, the billing information of the people who supported these entities was exposed. The researcher noticed the two instances on May 22, 2019, and reported it to Clover Sites immediately. After 24 hours passed and no answer was received, he decided to call them by phone. The person who answered told J. Fowler that they already knew about the problem, as fellow researcher Bob Diachenko had already notified them a month ago. This confused the researcher, as the claims about the matter having been already resolved couldn’t be valid.
Source: Security Discovery
Upon further inspection of the available data as well as a meeting with B. Diachenko, Fowler figured that the previous incident report was indeed addressed by Clover Sites. This could only mean that the new discovery corresponds to a separate incident. In October, and after the researcher couldn't convince Clover Sites of what was going on, he contacted Ministry Brands LLC, the owner of Clover Sites. They quickly confirmed that there was a problem with the two databases and finally secured them. This makes up for a total exposure period of at least seven months, which increases the chances of having fallen into the wrong hands to the level of certainty.
The researcher sent Clover Sites about 20 notifications, and they disregarded them all, thinking that they had already dealt with the reported problem. But how was the reporter able to access the data and provide them with actual details if the databases were secured? The irresponsibility of the Clover Sites IT team in this case really beggars belief. If you are one of the thousands who have had the four last digits of their credit card exposed, you should beware of potential phishing scammers who may try to get the missing digits from you. They have your name, email address, IP, and real name, so they can set up pretty believable scams.
Do you find Clover Site’s client data management justified given the possibility of them having been confused by multiple reports? Let us know what you think in the comments section down below, or on our socials, on Facebook and Twitter.