Cloudflare Report Notes Largest 5.6 Tbps Mirai DDoS Attack
- The Cloudflare global trends report said Mirai attacks accounted for 6% of all network layer DDoS attacks.
- A Mirai-variant botnet executed a volumetric assault via 13,000 IoT devices in October.
- Memcached-based and BitTorrent DDoS attacks saw a significant surge of approximately 300%.
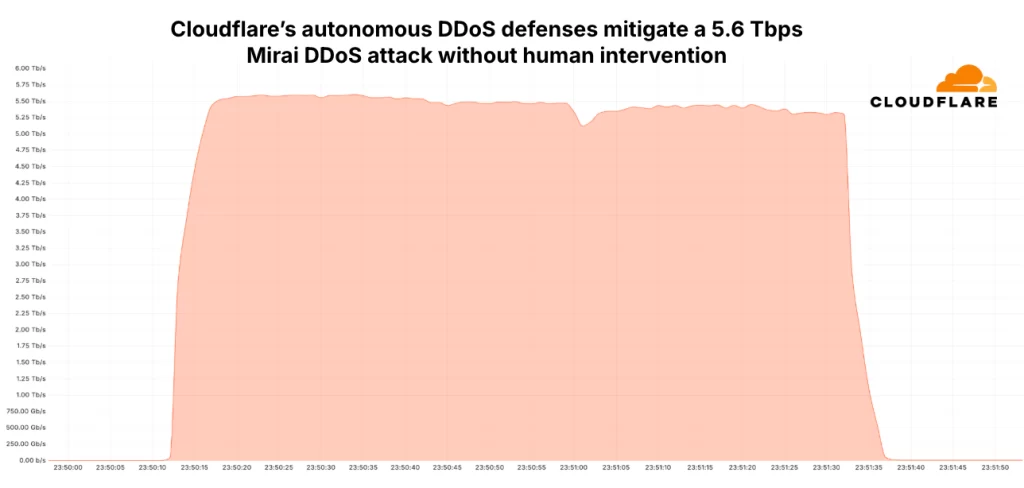
Web infrastructure and security company Cloudflare disclosed on Tuesday that it detected and successfully mitigated a massive 5.6 Terabit per second (Tbps) distributed denial-of-service (DDoS) attack, setting a new record for the largest reported DDoS assault to date.
The attack, which took place on October 29, 2024, targeted an unnamed internet service provider (ISP) located in Eastern Asia. The activity was attributed to a Mirai-variant botnet, leveraging over 13,000 Internet of Things (IoT) devices to execute the volumetric assault.
“The attack lasted only 80 seconds and originated from over 13,000 IoT devices,” the Cloudflare report said. Despite its brevity, the attack harnessed an average unique source IP address count of 5,500 per second, with each source contributing approximately 1 Gbps.
This 5.6 Tbps attack surpasses the previous record-breaking DDoS assault, also reported by Cloudflare earlier in October 2024, which peaked at 3.8 Tbps.
Cloudflare highlighted in its 2024 statistics that it mitigated approximately 21.3 million DDoS attacks throughout the year, marking a 53% surge compared to 2023. Notably, attacks exceeding 1 Tbps saw an alarming growth of 1,885% quarter-over-quarter, emphasizing the escalating scale and frequency of such threats.
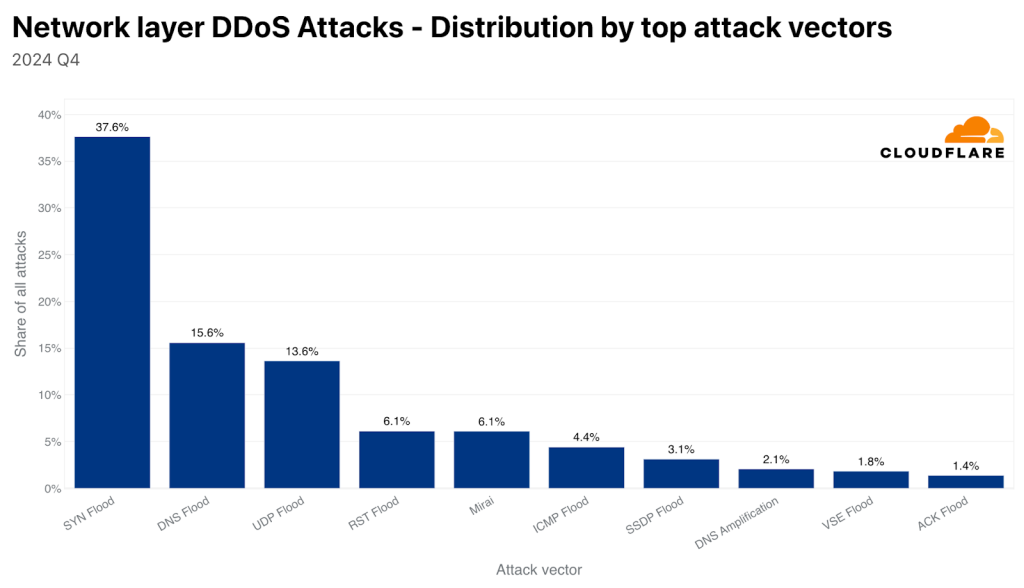
During Q4 2024 alone, Cloudflare blocked an estimated 6.9 million DDoS attacks. Among these, the majority (72.6%) were launched via known DDoS botnets. Furthermore, Layer 3/Layer 4 (network layer) attack tactics were dominated by SYN floods (38%), DNS floods (16%), and UDP floods (14%).
Memcached-based DDoS attacks surged by 314% quarter-over-quarter, and BitTorrent DDoS attacks and ransom DDoS incidents increased by 304% and 78%, respectively. Approximately 72% of HTTP-layer DDoS attacks and 91% of network-layer DDoS assaults concluded in under ten minutes.
The largest sources of DDoS activity were traced to Indonesia, Hong Kong, Singapore, Ukraine, and Argentina, while the most targeted nations were China, the Philippines, Taiwan, Hong Kong, and Germany. Telecommunications, internet services, marketing, IT, and gambling industries were the primary sectors under attack.
The Mirai botnet and its variants continue to pose significant cybersecurity threats. Originally uncovered in 2016, Mirai exploits security flaws and weak credentials in IoT devices to recruit them into botnets for DDoS attacks. These devices range from webcams to smart home products, which often lack robust security protocols.
Cybersecurity firms Qualys and Trend Micro corroborated that Mirai offshoots are actively leveraging known vulnerabilities in IoT devices. According to Qualys, a Mirai botnet variant dubbed Murdoc Botnet is part of a new large-scale campaign that exploits security flaws in AVTECH IP cameras and Huawei HG532 routers.