Cloudflare Handled a DDoS Attack That Spiked at 17.2 Million Requests per Second
- Cloudflare has successfully detected and mitigated the largest attack it has ever recorded.
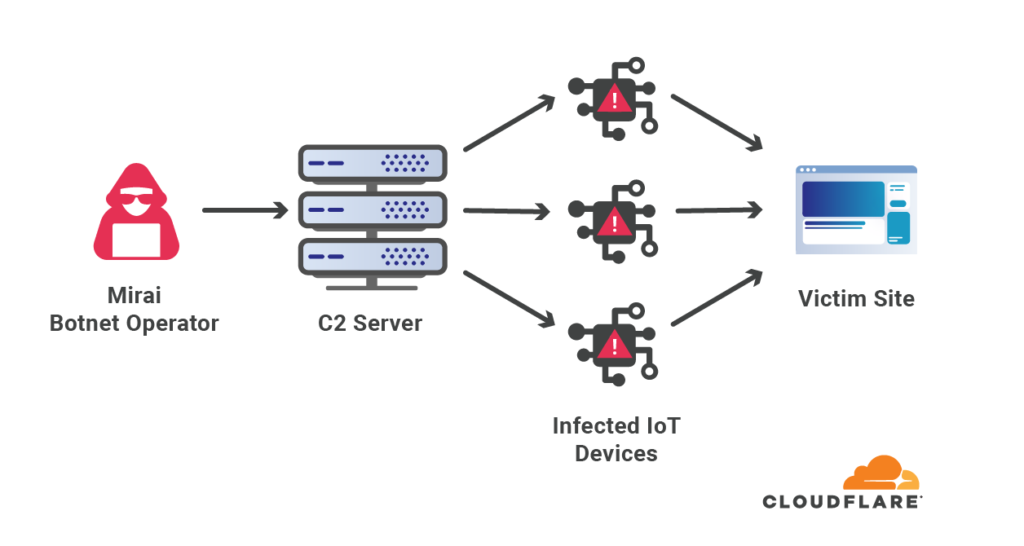
- The internet giant says the attack originates from a global botnet network, possibly Mirai.
- For now, these DDoS attacks come in short bursts, but upgrades could change this soon.
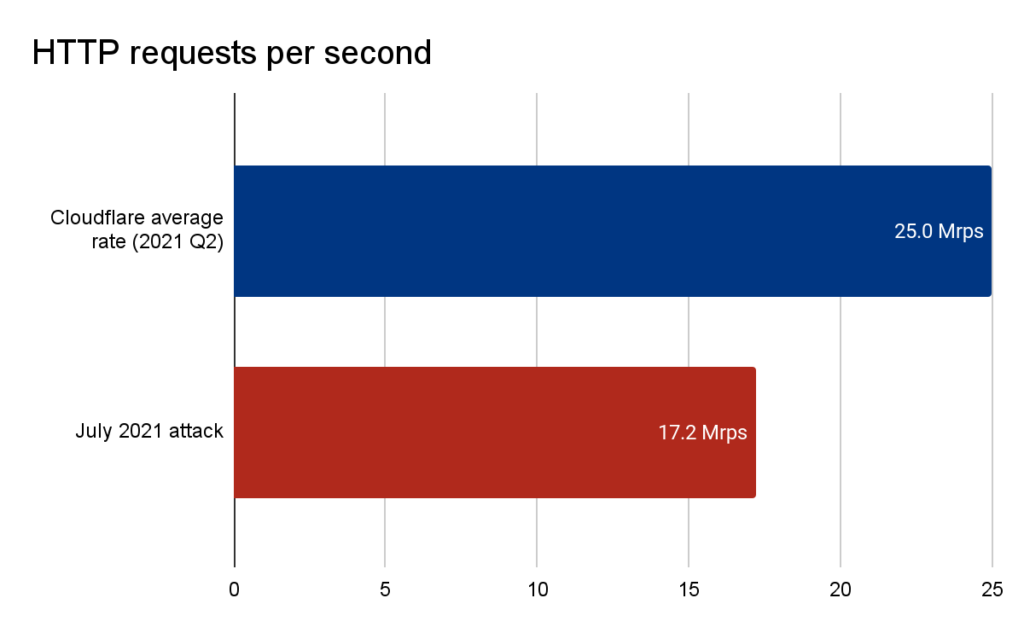
Cloudflare has posted a piece on its blog to share the details of an incident that had them handle a 17.2M RPS (requests per second) DDoS attack. To put this into perspective and make it easier to appreciate, Cloudflare has been serving an average of 25 million HTTP requests per second in Q2 2021, so this DDoS attack reached 68% of the firm’s handles as legitimate traffic volume.
Being an expert in DDoS mitigation, Cloudflare managed to handle this massive attack successfully - without its clients suffering any latency or other performance impacts. Once the attack was detected, Cloudflare’s systems automatically generated a real-time signature used to isolate the incoming malicious traffic from the rest and then push them to a dropping channel. As the company details in the post, there was no manual intervention from its personnel in this case.
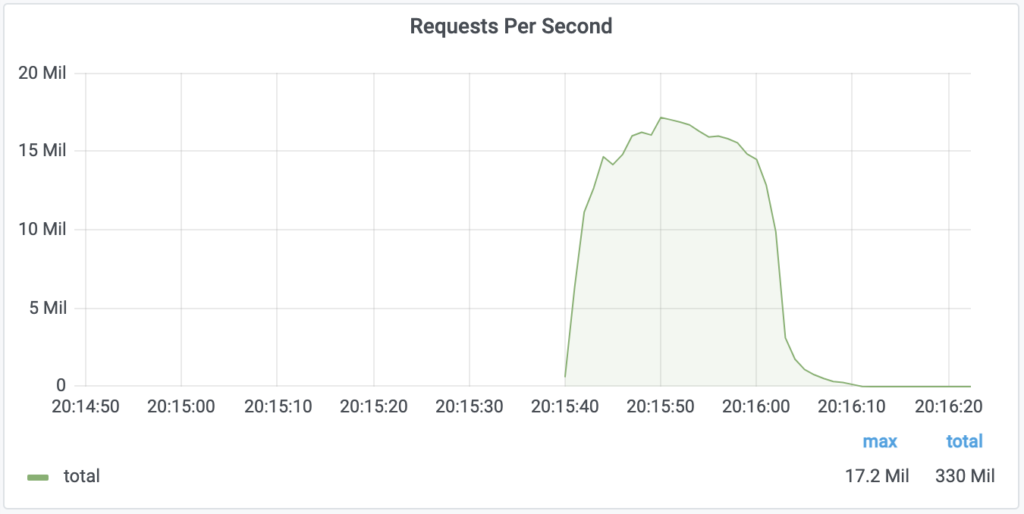
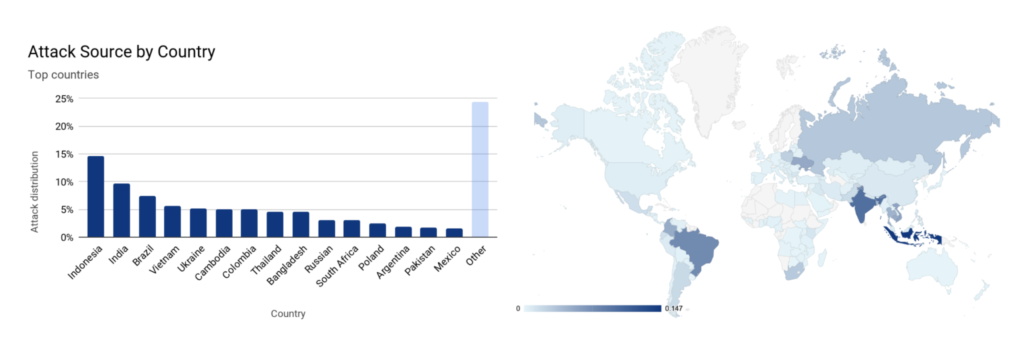
The attack came from a botnet that bombarded a particular Cloudflare customer in the financial industry and lasted for about 25 seconds. The traffic originated from over 20,000 bots spread across 125 countries, mostly from Indonesia, India, and Brazil. This is an indication that the actors may have exploited the presence of malware inside IoT devices, like the Mirai, for example.
What is notable in this case is the size of the attack, which for Cloudflare was the latest they have mitigated. More worryingly, the firm mentions that they have seen the specific botnet getting active at least twice in the past couple of weeks, with its previous target being a hosting provider. That attack peaked at 8 million RPS, so it wasn’t as voluminous.
Tyler Shields, CMO at JupiterOne, tells us:
While the attacks are currently limited to short bursts, the actors may upgrade their botnet capabilities and deliver more sustained levels of malicious traffic. In general, there’s an increase in the number of attacks launched by Mirai and other botnets, recording a rise of 185% this month and 88% in July 2021.