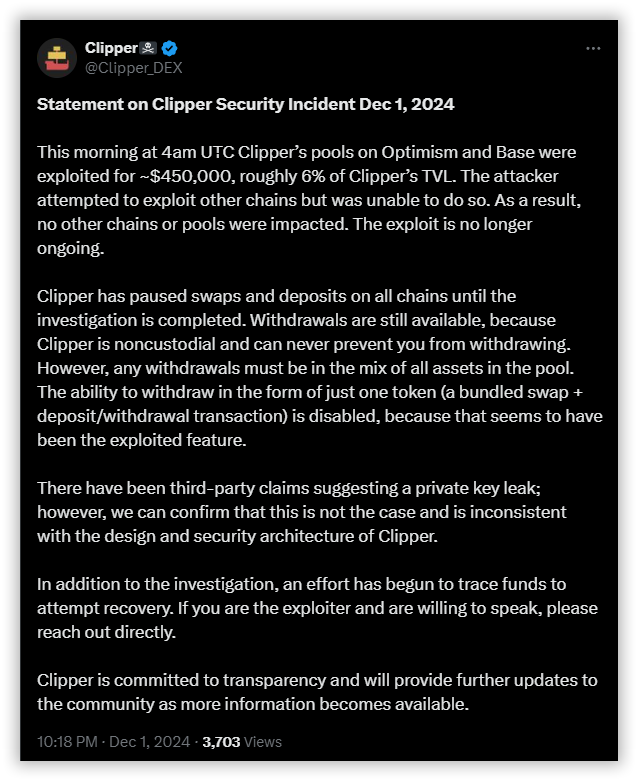
Clipper DEX Exploit Targets Withdrawal Functionality, Resulting in $450K Loss
- A cyberattack targeting Clipper DEX affected withdrawals and led to a loss of approximately $450,000.
- The attack occurred due to a flaw in its withdrawal process rather than a breach of private key security.
- The breach specifically impacted Clipper's pools on the Optimism and Base networks.
Decentralized exchange (DEX) Clipper has fallen victim to a sophisticated cyberattack, resulting in an estimated loss of $450,000. The exploit targeted the platform’s withdrawal functionality, compromising approximately 6% of its total value locked (TVL).
While initial speculation pointed to a private key leak, Clipper has clarified that the attack stemmed from a vulnerability in its withdrawal process rather than a breach in private key security.
The breach specifically impacted Clipper's pools on the Optimism and Base networks. Attempts to exploit other chains proved unsuccessful, according to Clipper's official statement. The attacker leveraged a vulnerability in the platform's bundled swap-and-withdraw feature to withdraw more funds than they had initially deposited by manipulating how the system processed transactions.
Leveraging the exchange’s API, the attacker manipulated withdrawal functions, gaining access to more tokens than their deposits would typically allow. One notably suspicious transaction involved a direct call to Clipper’s deposit and withdrawal functions, which ultimately enabled the exploit.
To mitigate further damage, Clipper acted swiftly, pausing all swaps and deposits across its platform while allowing restricted withdrawals. Users were required to withdraw a balanced mix of all assets rather than single-asset withdrawals to minimize the impact of the vulnerability.
Clipper has reassured users that its underlying architecture remains secure and that funds within unaffected pools are not at risk.
The company emphasized that no other pools or chains were impacted beyond those on Optimism and Base, and the exploit has been contained. Furthermore, Clipper confirmed that all current funds are secure in the system, with no threat to users' holdings in unaffected pools.
Clipper has also extended an unusual yet notable call to action to the attacker, stating, “If you are the exploiter and are willing to speak, please reach out directly.” This appeal, while unorthodox, demonstrates the platform's intent to explore all potential avenues for resolution.
To ensure the vulnerability does not persist, Clipper has outlined immediate measures to fortify its platform. Trading and deposits across all chains have been temporarily suspended, with additional safeguards implemented to prevent similar exploits in the future.
This incident comes as a stark reminder of the growing sophistication of cyber threats in the DeFi space. Last month, Lazarus APT employed fake DeFi games to abuse a Google Chrome zero-day vulnerability via social media ads, spear-phishing, and LinkedIn to lure in high-value individuals in cryptocurrency.