Cl0p Ransomware Intends to Reveal Over 60 Victims of Cleo Cyberattack
- The Cl0p ransomware gang announced intentions to publish a list of more than 60 organizations that were impacted by the Cleo security incident.
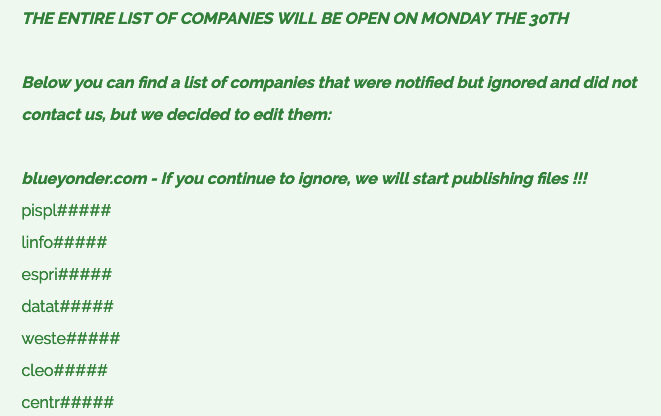
- Only Blue Yonder was previously named as the first affected company in this matter.
- For now, the threat actor only revealed partial names, threatening to go public with alleged full names unless the ransom is paid.
The Cl0p ransomware group has announced plans to name over 60 organizations hacked through vulnerabilities in file transfer products developed by enterprise software provider Cleo. Their Tor-based leak site provided victims with access to confidential chats and proof of stolen data.
The group took credit for these attacks in mid-December, claiming at the time to have targeted a significant number of victims. The recent announcement signals an escalation in their ransom demands.
To date, Cl0p has publicly named one victim, Blue Yonder, a supply chain management software provider that supplies technology for businesses, including Starbucks and major grocery chains.
The group has also published partial names of more than 60 other organizations, threatening to reveal their full identities on December 30 if ransom demands are not met. Cl0p claims these companies have ignored previous communication attempts and are being given a "final chance."
Termite, a lesser-known ransomware group, has also claimed responsibility for the Blue Yonder attack, intensifying speculation about a connection between Termite and Cl0p.
The Cleo-associated breaches exploit two critical vulnerabilities—CVE-2024-50623 and CVE-2024-55956—identified in the Harmony, VLTrader, and LexiCom file transfer tools. Patched versions (5.8.0.24) of the software address these flaws, but prior to these updates, attackers had been exploiting at least CVE-2024-55956 as a zero-day since December 3.
Cleo serves over 4,000 enterprises and has hundreds of internet-facing instances of their tools globally, potentially expanding the attack surface for other malicious actors.
Cl0p’s activity in the Cleo breach echoes the group’s MOVEit campaign earlier in 2023. In that campaign, they exploited a zero-day vulnerability in the MOVEit file transfer solution to steal sensitive data from thousands of organizations worldwide.