Citrix Admits Hackers Were Inside its Systems for Five Months
- Citrix is circulating a warning to affected employees and contractors who had their data compromised last year.
- The software vendor now admits that hackers had intermittent access to its network for five months.
- The company is gradually losing the trust of its high-profile customers, as one grave incident follows another.
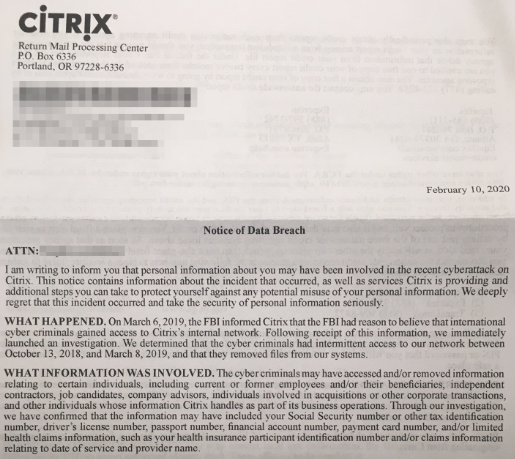
Citrix has acknowledged that intruders managed to break into its networks and maintain access for five months, between October 13, 2018, and March 8, 2019. Some of the data the hackers stole during that period include personal and financial information of Citrix employees, interns, job candidates, and contractors. The actors managed to enter the corporate network by probing the personnel accounts for weak passwords, a technique otherwise known as "password spraying." This method is an attack using low-volume attempts that consist of trying out a few common passwords instead of brute-forcing. It’s preferable because it minimizes the chances of lock-outs while making the attack stealthier.
Back in March 2019, Citrix announced an internal network breach, after the FBI tipped them on targeted activity coming from international cyber-criminals. The American software company discovered that the attackers gained limited access to its network and that they managed to steal private documents. However, the internal investigation was only beginning, so their IT department couldn’t determine how long their systems remained vulnerable, and what the attackers had been exfiltrating exactly. This has now been determined to “five months,” which is pretty extensive. Counting backward from the event, we step upon another piece of news presenting a suspicious password reset to ShareFile users that Citrix Systems imposed back in December 2018. However, this may or may not be related to the security breach.
The sensitive data now determined to have been compromised includes the following:
- Social Security Number (SSN)
- Tax ID
- Driver’s License
- Passport Number
- Bank Account Number
- Payment Card Number
- Health Claims Data
- Health Insurance ID
- Dates of Health Service Provision
Citrix sent the following letter to all of the affected individuals a couple of days ago, and these people are now called to take precautionary measures against bank fraud and identity theft actors.
Source: Krebs on Security
Things haven’t been going smoothly for the software giant lately. Its VPN products, which are used by many Fortune 100 companies, were found to be vulnerable to flaws that were almost immediately exploited by Iranian hackers (among others). A few months back, Positive Technologies discovered the highly critical CVE-2019-19781 vulnerability, which placed some 80,000 companies in 158 countries that used “NetScaler ADC” and “Gateway” at great risk of falling victims to remote access, data theft, lateral infiltration, phishing, and DoS attacks.