“Cicada” APT10 Targeting Japanese Organizations for Over a Year Now
- Japanese entities are being under attack by the Chinese APT group “Cicada” since October 2019.
- The actors are using a wide range of tools and methods that enable them to remain well-hidden.
- There’s strong evidence pointing to these particular hackers, like DLL-side-loading and certain obfuscation techniques.
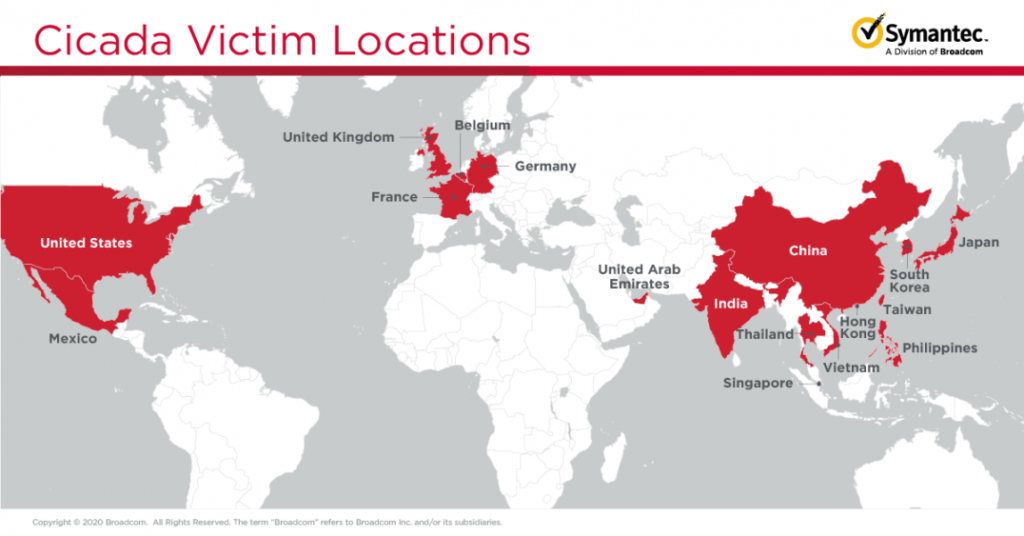
There’s mounting evidence that the threat actors behind a campaign that has been active since October 2019 are “Cicada” (APT10), otherwise known as “Stone Panda” and “Cloud Hopper.” The campaign focuses on cyber-espionage, targeting Japanese companies and organizations in 17 countries worldwide, where they are operating offices.
The victims are engaged in a large variety of industry sectors like pharma, electronics, engineering, clothing, and automotive. Government entities are also included in the target list, so there’s a wide scope of information collection.
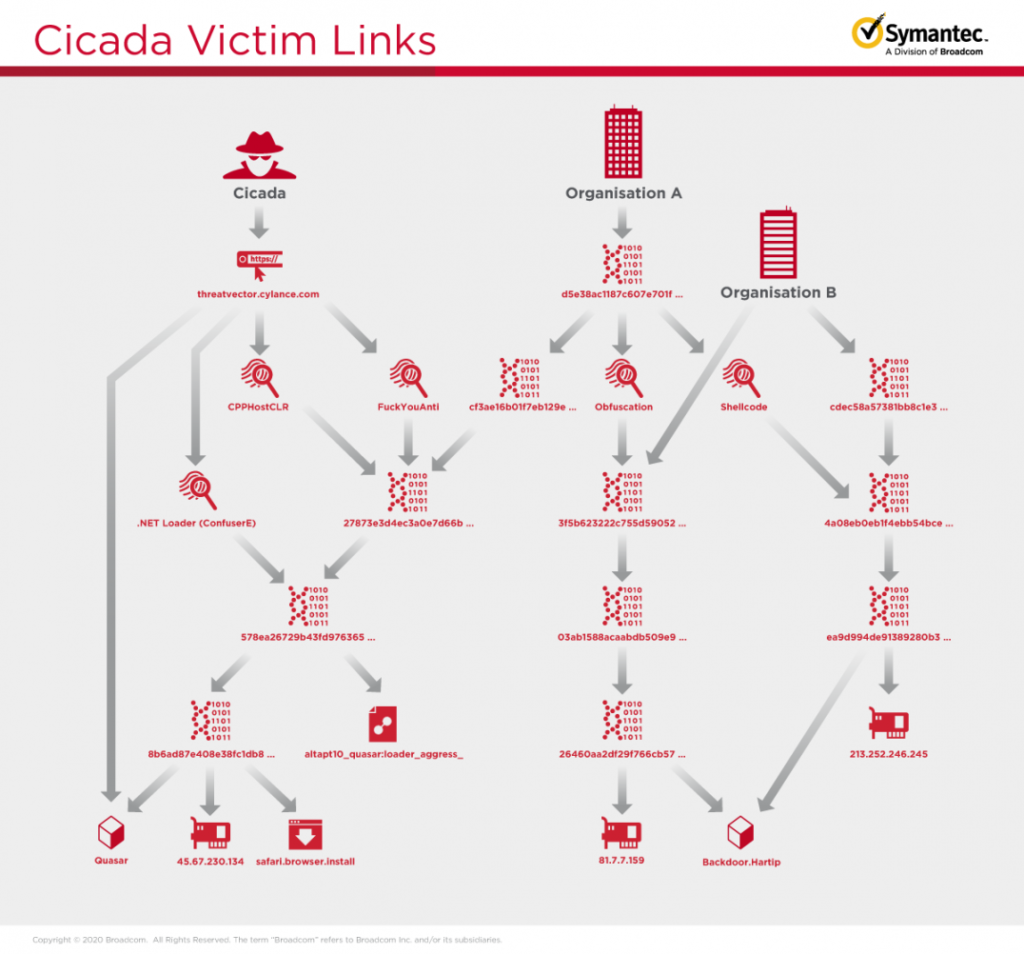
The report and attribution come from Symantec researchers, who have enough evidence to point the finger at Cicada with “medium” confidence. The analysts have found similar obfuscation techniques, shellcode, and loader DLLs that have been associated with Cicada in past campaigns, so there’s a definite association here.
The tactics involve network reconnaissance as the first step, credential theft for deeper network access and lateral movement, and RAR archiving and even data encryption before exfiltration to the C2.
As for the tools used by Cicada, there’s a rich collection involving the following stuff:
- Certutil – Decode information, download files, install browser certificates
- Adfind – Perform Active Directory queries
- Csvde – Extract Active Directory files and data
- Ntdsutil – Credential dumping
- WMIExec – Remote command execution and lateral movement
- PowerShell – Code execution
DDL side-loading, which is a trademark of Cicada, is embroidered in all stages of the attack, with the actors replacing legitimate libraries with their own, custom, malicious versions. This is useful in avoiding detection and executing code with the privileges held by the hijacked processes started by legitimate software tools.
As the Symantec researchers report, Cicada deploys a tool capable of exploiting CVE-2020-1472, a vulnerability that was patched on August 11, 2020. This is the open door that enables the hackers to spoof a domain controller account and steal the credentials that allow them to take over the domain and compromise all Active Directory services.
To protect systems against custom backdoors like Cicada’s, one has to apply fixing updates like the CVE-2020-1472, use endpoint protection solutions, network monitoring tools, and a strictly set firewall. Actors like Cicada are extremely sophisticated and hard to even detect, let alone stop. The particular hacking group has been around since at least 2009 and is believed to be backed by the Chinese state.