Chinese Hacking Group “APT41” Is Using a New Speculoos Backdoor
- APT41 is still exploiting CVE-2019-19781, but this time, they’re using a new Speculoos backdoor.
- The attackers have developed the new malware specifically for BSD systems used in certain organizations.
- The backdoor enables them to drop more payloads, conduct MITM attacks, or steal user credentials.
The Chinese cyber-espionage group “APT41” has been very active since the beginning of the year, exploiting several vulnerabilities to target companies and organizations in several countries. According to a report compiled by Unit 42 researchers, the actors keep on using CVE-2019-19781, which was exploited in at least another three instances, retrieving a novel Speculoos backdoor over FTP. As for the targets of this latest activity, the researchers report a manufacturer in Austria, a higher education institute and a state government entity in the United States, and also a university in Colombia.
It looks like APT41 have specifically developed this backdoor to target Citrix network appliances and FreeBSD systems. BSD (Berkeley Software Distribution) is a type of Unix operating system that sees limited use on the server market, so malware that was specifically created for it isn’t a common sight. This is indicative of the sophistication and the narrow targeting of APT41. Speculoos is a backdoor compiled with GCC 4.2.1 and has the form of an ELF executable. It communicates with alibaba.zzux[.]com (resolving to 119.28.139[.]120) over TCP/443. The backdoor also has a backup C2, which is 119.28.139[.]20.
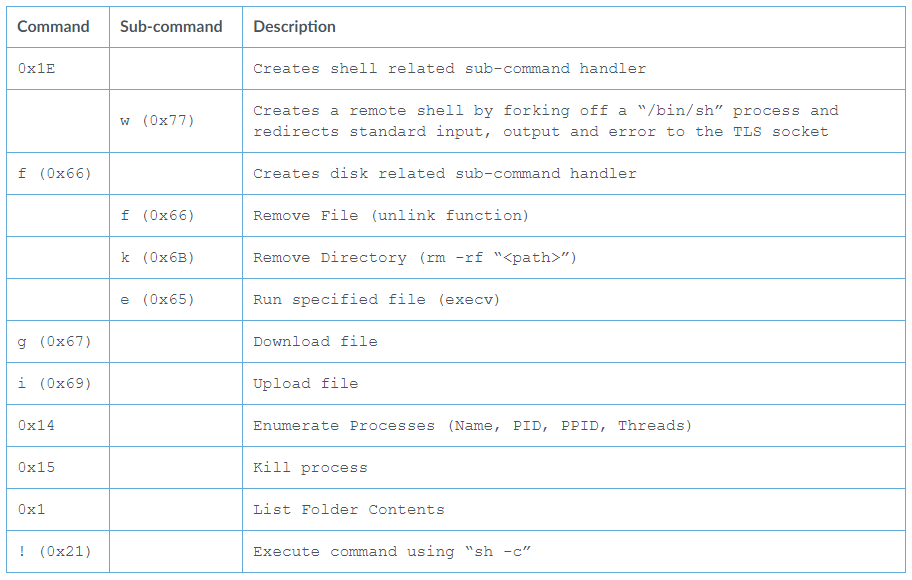
Speculoos begins its activity by performing a system enumeration and sending the generated fingerprint back to the C2 server. Then, it enters a command-reception loop and waits for the C2 to order what to do next. The following table shows all the commands that are supported by Speculoos right now. Unit42 researchers had the chance to sample two Speculoos variants, which were identical in operation, so they are confident that their report faithfully covers the current capabilities of APT41’s new toy.
Source: Unit42
At this time, the new Speculoos backdoor is used for lateral movement in corporate networks, as the target devices have access to a large number of systems. APT41 created this custom malware to find a way inside these networks, so while it looks like a far too specific and intricate work, it really is worth the effort. In addition to lateral movement, Speculoos enables the attackers to modify network traffic, which would open the door to additional payload injection, man-in-the-middle attacks, or user redirection to spoofed phishing pages. To make matters worse, detecting a Speculoos infection on Citrix appliances is pretty hard and quite unlikely, as most black-box solutions out there don’t interact with them and don’t inspect their activities.