Chinese Data-Scraping Startup Leaked Its 408 GB Database Online
- A social media data scraping company has exposed millions of users along with several account details.
- The platforms affected are Facebook, Instagram, and LinkedIn, while there are even details not seen publicly there.
- This creates a scamming, spamming, and account-takeover opportunity for malicious actors.
A Chinese data-scraping social media management firm named Socialaarks has exposed over 200 million users of Instagram, Facebook, and LinkedIn, as its entire 408 GB of data leaked online. The security incident resulted from a “typical” ElasticSearch server misconfiguration, which was set to public access without password protection.
As the contained data wasn’t encrypted, anyone with a web browser could access them. The instance was discovered by researcher Anurag Sen and the cybersecurity team at Safety Detectives.
Socialarks was scrapping public profiles from various platforms since 2014 when it came into existence. This data collection aimed to help in brand building, marketing, social customer management, etc.
The exposed set doesn’t contain only public data but also things that are hidden from public view or aren’t even provided to the platforms upon the creation of an account. Finding them bundled together and with linkage pointers between different platforms is great for scammers, spammers, and account hackers.
In detail, the researchers have found the following in the exposed server:
- 11,651,162 Instagram user profiles
- 66,117,839 LinkedIn user profiles
- 81,551,567 Facebook user profiles
A further 55,300,000 Facebook profiles were also discovered, but that set was promptly deleted a few hours after the team discovered the server. So, this subset deserves a special categorization as it may have evaded hacker access.
As for the individual profile entries, these included the following details:
- Full name
- Phone numbers
- Email addresses
- Profile link
- Username
- Profile picture
- Profile description
- Average comment count
- Number of followers and following count
- Country of location
- Specific locality in some cases
- Frequently used hashtags
- Messenger ID
- Country of location
- Like, Follow and Rating count
- Job profile including job title and seniority level
- Company name and revenue margin
- Domain name
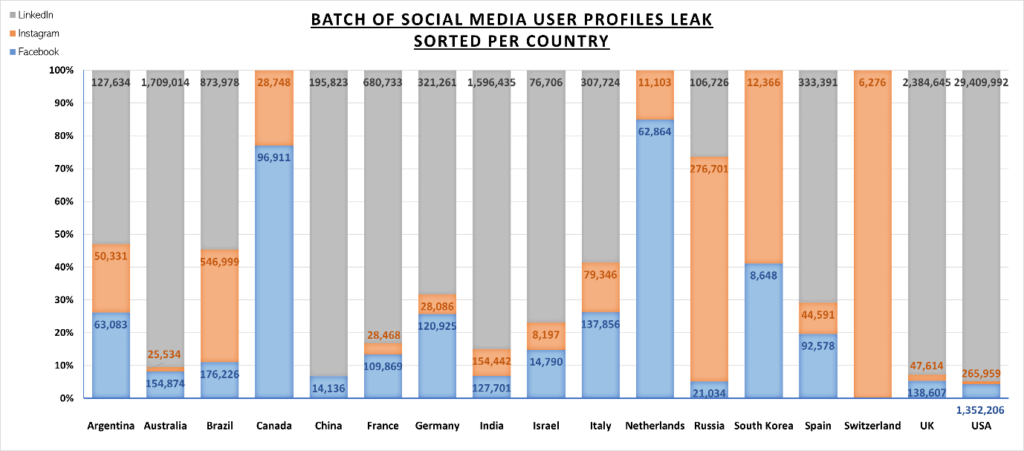
Clearly, not all of the entries are populated with all of the above, as some are platform-specific. Also, there are users from quite a few countries in the dataset, with the majority being from the United States, the UK, India, Italy, Brazil, Australia, and Russia.
Finally, the leak includes high-profile celebrities and social media influencers (on Instagram) with a particularly high number of followers, so for these people having their details leaked the chances of finding hacker trouble are way higher.
From now on, beware of scamming attempts, messages informing you that you need to take action with your accounts, and even malware distribution campaigns. The chances of this data not being exfiltrated by malicious actors are already slim, so treat the aforementioned information as compromised.