Chinese APT ‘SharpPanda’ Developed Custom Backdoor to Spy on Asian Governments
- Chinese hackers use a novel custom-made backdoor to spy on other Asian governments.
- The actors appear very sophisticated, using numerous obfuscation and anti-analysis techniques.
- All signs point to this being a state-supported APT group doing cyber espionage as a daily job.
A Chinese APT group dubbed ‘SharpPanda’ has spent the last couple of years developing and refining a custom backdoor that enabled it to conduct sophisticated cyber espionage spying against governments in the Southeast Asian region. This has been discovered only now by Check Point researchers, who were able to identify the activity, mapped the full infection chain, and uncovered the entire set of tricks deployed by SharpPanda.
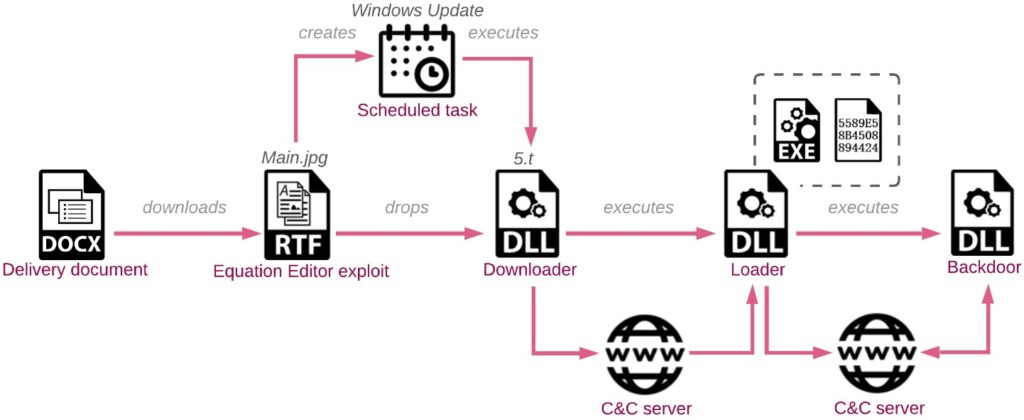
It all starts with the arrival of an email that claims to come from another ministry of the target government. The laced DOCX documents use a remote template function to pull a template from the document using a remote server that the actors control. All that is needed for the threat to unfold is the opening of the file, and an RTF file is fetched. These files contain embedded objects that exploit vulnerabilities in the Equation Editor on MS Word.
The final payload and the custom backdoor, in this case, is a DLL file that carries the name “VictoryDll_x86.dll”. This is an entirely custom-made backdoor that has the following capabilities:
- Delete/Create/Rename/Read/Write Files and get files attributes
- Get processes and services information
- Get screenshots
- Pipe Read/Write – run commands through cmd.exe
- Create/Terminate Process
- Get TCP/UDP tables
- Get CDROM drives data
- Get registry keys info
- Get titles of all top-level windows
- Get victim’s computer information – computer name, user name, gateway address, adapter data, Windows version (major/minor version and build number), and type of user
- Shutdown the PC
On the aspect of obfuscation and anti-analysis, the actors have implemented RC4 encryption on the RTF payload, anti-sandboxing techniques on the downloader, base64 encoding on the data packets that come and go, and XOR 32-bit on the loader. Moreover, the loader hides its main functionality and evades detection by dynamically resolving API calls, which is a known and effective method.
In terms of attribution, the RTF exploit noticed in this campaign has been linked with other Chinese APT groups. Also, the C2 servers appeared to be active during working hours in China, between 01:00 and 08:00 UTC. When the Labor Day holiday was on, between May 1 and May 5, no payload was served by the C2, even during working hours. And finally, some early test versions of the backdoor were uploaded to VirusTotal from China.