China Telecom Reroutes European Mobile Traffic for Two Hours
- A BGP hijacking incident highlights an old and unresolved problem once again.
- The routing leak lasted for about two hours, which is way longer than a usual couple of minutes.
- China Telecom is once again on the spotlight for this, but no one can prove they did it on purpose.
If you live in Switzerland, France, or Holland, there’s a chance that your internet mobile traffic data was rerouted for about two hours on June 6, passing through China Telecom, the state-owned ISP (Internet Service Provider). The incident occurred after a Swiss data center owned and operated by Safe Host accidentally leaked over 70000 routes from its internal table to the Chinese ISP, so the latter was able to perform a BGP (Border Gateway Protocol) hijacking. This type of hijacking concerns the takeover of IP addresses through the corruption of the routing tables, and it can happen either accidentally or deliberately.
To put BGP hijacking simply, your traffic may get to travel beyond its intended scope, following a path to another ISP through an accidental or purposeful redirection, enabling eavesdropping or traffic analysis by that ISP (in the case that it was done intentionally). In the case of China Telecom, the company has been accused of trying to reroute foreign network traffic multiple times before. For example, take a look at this ThousandEyes report from November 2018, and this study from the Tel Aviv University that focuses on the same subject.
https://twitter.com/OdyX_/status/1136615027123916800
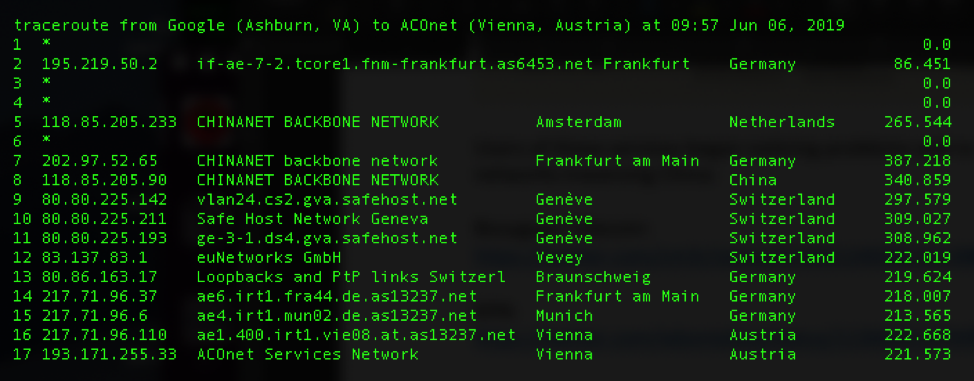
Back into the most recent incident, Oracle Internet Analysis did some monitoring on what was going on at the time of the rerouting and figured out that the most impacted ISPs were Swisscom, KPN, Bouygues Telecom, and Numericable-SFR. The most notable characteristic of this incident was that it lasted for a full two hours instead of a typical couple of minutes. During that time, users noticed slow internet speeds and even a complete inability to connect to specific servers. The following image shows Oracle’s traceroute measurements that were also sucked in the routing leak.
image source: blog.apnic.net
Oracle’s Director of Internet Analysis was reluctant to accuse China Telecom of deliberate BGP hijacking. As he said, there’s no way to tell if this was an intentional incident or just a human error. However, the event shows that China Telecom is yet to implement essential routing safeguards that prevent the propagation of routing leaks, in a day and age when other major international carriers have placed all of the necessary detection, remediation, and prevention measures. As long as there’s a big ISP out there not caring about preventing BGP route leaks, the rest are obliged to act even more responsibly and with greater care.
Is China Telecom not complying with the basic BGP route leak protection guidelines on purpose, or are they simply negligent? Let us know what you think in the comments down below, or on our socials, on Facebook and Twitter.