China-Linked Hackers Target Drone Makers in Espionage Campaign
- Threat actor Tidrone was seen deploying malware via two backdoors on compromised systems.
- The victims are mainly drone manufacturers, whose sensitive data is then exfiltrated.
- They use a legitimate remote control tool and exploit enterprise resource planning software flaws.
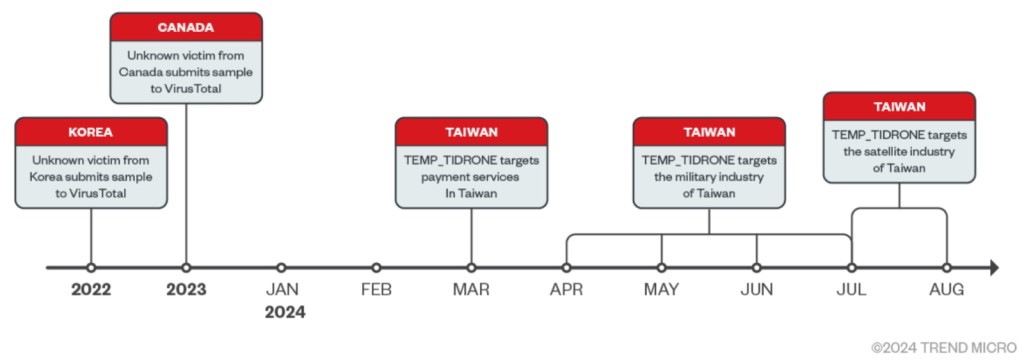
A threat actor identified as Tidrone, linked to Chinese espionage activities, has been targeting military and satellite industries in Taiwan, according to a report from Trend Micro. The group has primarily focused its attacks on drone manufacturers, leveraging vulnerabilities within enterprise resource planning (ERP) software and remote desktop access to infiltrate systems.
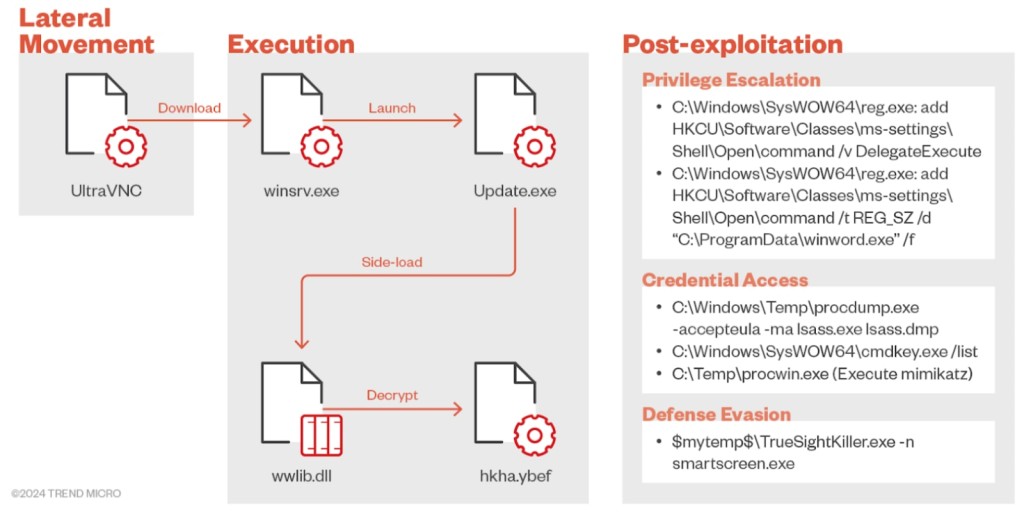
Tidrone has utilized sophisticated malware to bypass system protections and gather sensitive information. The malware is deployed using two backdoors, Cxclnt and Clntend, through the legitimate remote control tool UltraVNC.
The presence of the same ERP system across different victim environments suggests a possible supply chain attack vector.
The threat actor has been observed updating its deployment techniques, merging payloads, and modifying injection chains to include the svchost process. This sophisticated method involves loaders deploying backdoors directly into memory.
The focus on drone manufacturers and military-related industry chains indicates a strategic espionage motive, targeting sensitive data held by these entities.
Capable of collecting system and user information, the Cxclnt backdoor communicates with a command-and-control (C2) server, receives payloads, deletes traces, and sets persistence within the system.
Functioning as a remote shell, the Clntend backdoor can be injected into the current or svchost process, depending on the installation configuration.
The threat actor uses C&C server domains with misleading names, such as symantecsecuritycloud[.]com and microsoftsvc[.]com, to obscure their network infrastructure and hinder investigations.
Similarities between Tidrone's activities and known Chinese espionage operations were revealed in the report. The targeted attacks on military-related industries, particularly drone manufacturers, reinforce the suspicion of espionage motives, given the sensitive nature of the data involved.
In July, a China-linked threat actor called APT17 was seen targeting Italian companies and government entities with a variant of the 9002 RAT malware, aka Hydraq and McRAT. The RAT was distributed via an email campaign containing malicious URLs.