Cellebrite Zero-Day Exploit Used by Local Authorities to Unlock Serbian Activist’s Phone
- A zero-day exploit targeting Android USB kernel drivers identified in the wild was used against a Serbian activist.
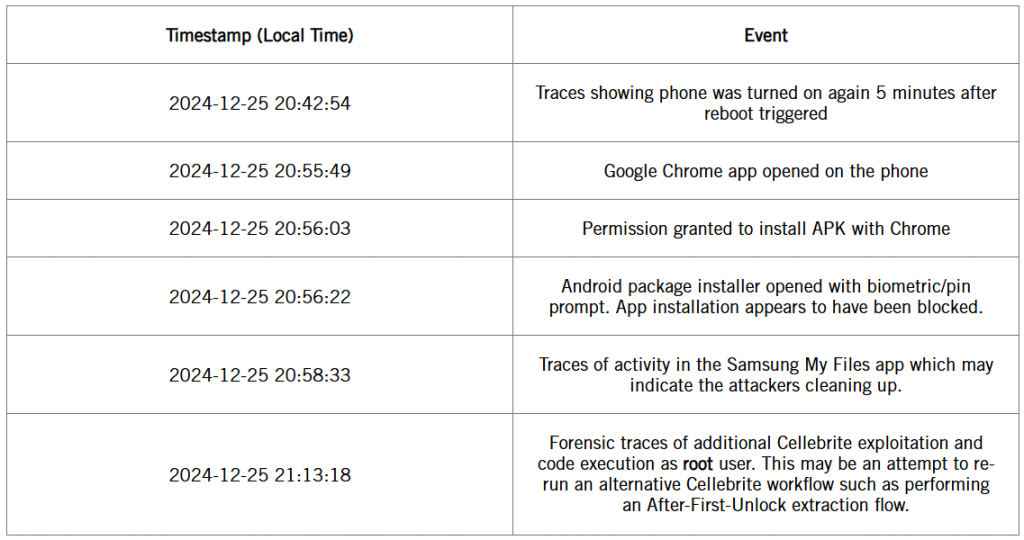
- Local authorities tried to sideload an Android APK after unlocking a student’s phone with Cellebrite.
- Patch updates are available for the flaw that can infiltrate any Android and Linux kernel driver via the phone's USB port.
A sophisticated Cellebrite zero-day exploit was used to breach the Android phone of a Serbian student activist. This latest finding highlights the continued misuse of digital forensic tools to suppress civil society despite previous calls for reforms.
The exploit leveraged vulnerabilities in core Linux USB kernel drivers, which could potentially affect over a billion Android devices.
This abuse, involving Cellebrite’s advanced mobile extraction tools, enabled security officers to access the activist’s personal device without consent or legal approval. The logs show the authorities unlocked the device via privileged root access to the phone.
Following technical evidence shared by Amnesty with Google in late 2024, the tech giant identified three zero-day vulnerabilities—CVE-2024-53104, CVE-2024-53197, and CVE-2024-50302.
Google has since patched two vulnerabilities in the February 2025 Android Security Bulletin, with the third fix added to the Linux kernel pipeline.
Cellebrite, known for its advanced mobile forensic technologies, has faced significant scrutiny since Amnesty’s earlier investigation. The company announced a suspension of product usage by its Serbian customers following the initial December 2024 report.
Google’s Threat Analysis Group was pivotal in addressing these vulnerabilities, alongside Amnesty’s Security Lab and other advocacy organizations like the Balkan Investigative and Reporting Network (BIRN) and the SHARE Foundation.
The incident follows the release of Amnesty’s 2024 report, A Digital Prison, which previously documented similar cases.
This case is similar to previous cases when Serbian authorities planted NoviSpy spyware on a detained journalist’s phone after using Cellebrite to unlock it.
Citizen Lab criticized the availability of such tools and advised at-risk individuals—including protesters and journalists—to strongly consider switching to more secure devices.