Casio Breach Leaks 6.5K Employees, 1.9K Business Partners, and Over 90 Customers Data from October Ransomware Attack
- The security incident Casio acknowledged in October exposed the private data of thousands of employees and partners.
- The leaked information includes names, email addresses, phone numbers, and more.
- Investigations into the ransomware attack revealed the hackers exploited system flaws after gaining access via phishing emails.
Casio’s investigation into a ransomware attack that disrupted its operations and led to a significant data breach revealed the sensitive information of approximately 6,500 employees and 1,900 business partners.
Following a comprehensive forensic investigation, Casio revealed the extent of the breach and how the attackers infiltrated its systems. According to the company's report, the cybercriminals exploited flaws in systems associated with its overseas offices, using phishing emails to gain initial access to the network.
The attackers encrypted data on several servers and stole confidential corporate documents, employees’ personal information, and details from business partners.
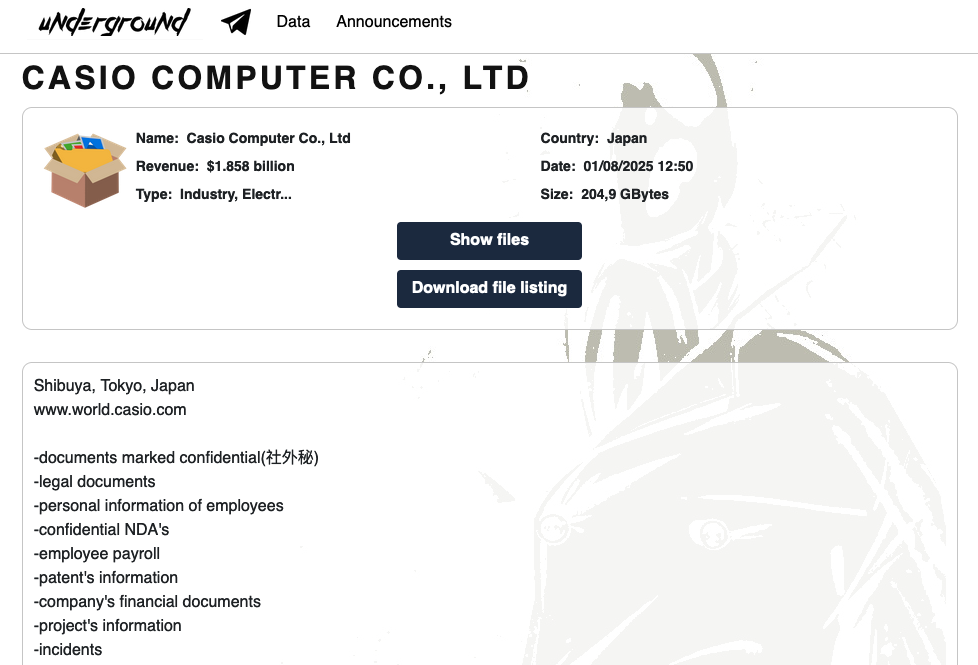
The 2024 breach impacted approximately 6,500 Casio employees in Japan and other regions, compromising varying combinations of names, email addresses, genders, dates of birth, and taxpayer IDs. The data of around 1,900 business partners was exposed, including names, company details, email addresses, phone numbers, and, in rare cases, ID cards.
Ninety-one customers who purchased products in Japan and required delivery or installation were also affected. The stolen data includes their names, phone numbers, addresses, dates of purchase, and product names.
The compromised files also included contracts, invoices, sales documents, meeting summaries, internal review materials, and data related to internal systems. Crucially, payment card information was not among the stolen data.
A ransomware group known as Underground has taken responsibility for the attack. However, Casio emphasized that there is no evidence of data theft from its core customer database or systems that process personal customer information.
The group claims to have exfiltrated over 200 GB of data, some of which they have reportedly made available for download on their Tor-based leak site. They issued threats to release additional files shortly after the breach became public. Casio has not disclosed whether it engaged with the attackers or paid any ransom.
Casio has stated that it has taken measures to address the vulnerabilities exploited in the attack and enhance its security posture to prevent future incidents. The company has also begun notifying affected stakeholders and coordinating its next steps.