Canadian Tax Phishing Is in Season and Old Kits Are Being Refreshed
- Phishing actors are getting reactivated, and Canadian phishing kits are circulating again.
- The kits remain largely unchanged, trying to steal people’s bank details and credentials.
- The actors are trying to convince people to enter responses to security questions, CVVs, and PINs.
The Canadian government has decided to move the tax-filing deadlines for their citizens, as well as to lift any late-submission penalties. The reason for this move is the COVID-19 pandemic, and this is actually something that is happening in many countries right now. In response, the tax phishing actors who have been waiting to act back in April have just started to activate, as the new dates were set between June 1, 2020, and August 31, 2020. That said, Canadian citizens, especially those who expect tax returns and refunds, are advised to be extra careful with email communication.
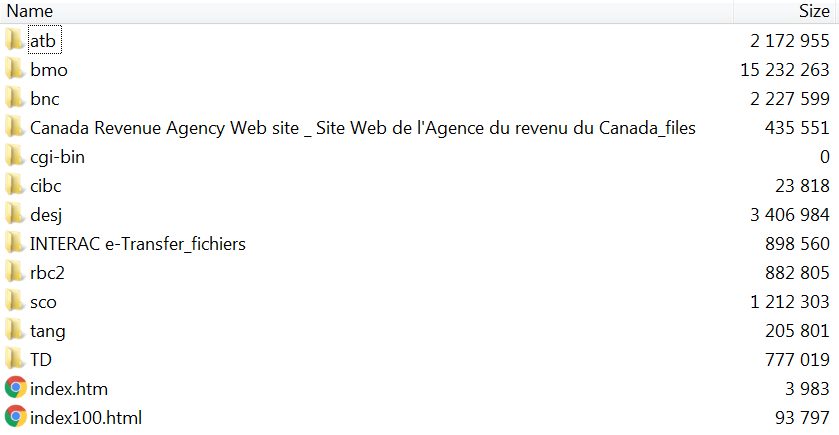
According to a report by Cyren researchers, the phishing actors are using an old phish kit that has been somewhat refreshed, and which was purpose-built for Canada. The kit was first spotted being circulated in 2018, but since most of the affiliate banks that receive tax refunds in the country remain the same, it still does the trick without the need for a lot of modification work. The package that contains the kit is named “covid.zip,” and it contains various useful (for the actors) files like the index.htm shown below.
Source: Cyren Blog
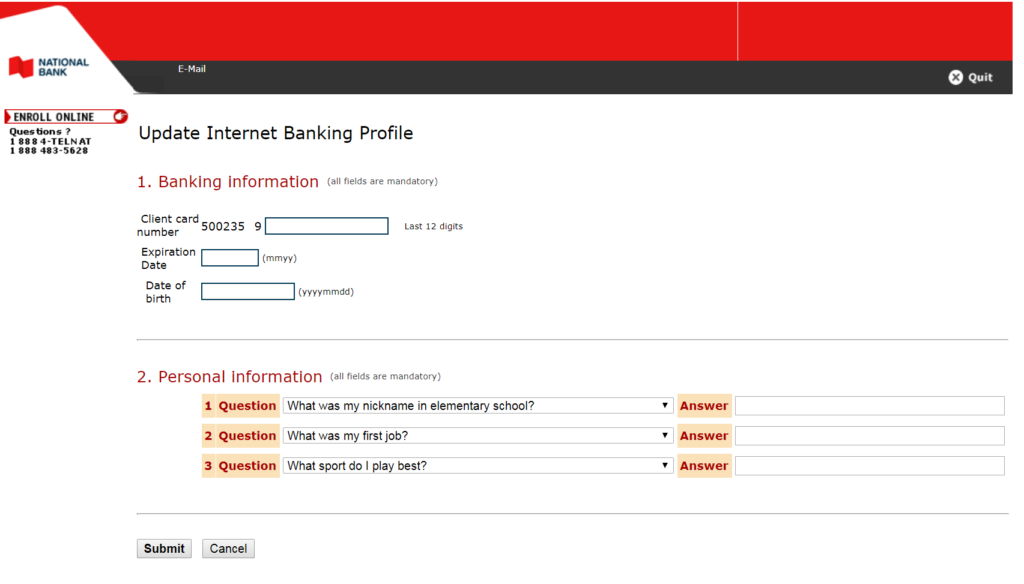
The goal of the phishing actors is to trick the email recipients into entering their bank account details. Supposedly, the targets are requested to do that to “update their bank details” in order to be ready for the reception of the tax return. If the victims don’t find the timing, or even the very request suspicious, they may end up entering their card CVV, ATM PIN, and even the answers to their security questions. This information is never requested at any other point than the registration, while the ATM PIN is a strictly personal piece of data that no one but the owner should know.
Source: Cyren Blog
If clicking an email URL or embedded button in the message leads you to any of the following domains, you are getting phished.
- hxxp://whizkidtoys.com/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/atb/login.aspx
- hxxp://jevn.in/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/cibc/index.php
- hxxps://nombolepome.com/df/vraitax%202/vraitax/tax/96322/tax/taxb/bmo/index.php
- hxxp://zeuohed.com/wp/tax/taxb/bnc/National%20Bank%20Online.html
- hxxp://jevn.in/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/cibc/index.php
- hxxps://avdeeff.ca/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/desj/index2.php
- hxxp://shopoliverz.ch/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/rbc2
- hxxp://astrologicalshop.com/canda/vraitax%20(2)/vraitax/tax/96322/tax/taxb/sco/indx.php
- hxxp://occurator.com/wl/tax/tax/taxb/td
If you want to ensure that your bank has an active status on your account and that you don’t need to do anything like updating your information, visit your bank’s website directly. There, the only thing you’ll need to enter is your username, password, and maybe also answer a security question. If you have already fallen victim to these attacks, contact your bank immediately, reset your credentials, set up new security questions, and activate two-factor authentication if available. Remember, similar highly-targeted campaigns are set up in other countries, too, so the danger is not limited to Canada.