Calibration Fingerprinting Attack Ends All Notions of User Privacy in Smartphones
- Researchers proved that smartphones are vulnerable to sensor data fingerprinting attacks.
- While there are several mitigation methods that could be implemented, right now, all devices are exploitable.
- The fingerprinting of the devices can occur either through an application or via a website that runs JavaScript.
Researchers from the University of Cambridge have recently published a scientific paper that demonstrates the possibility of generating unique device fingerprint profiles by using smartphone sensors. In fact, not only is this possible, but it can yield highly reliable data without any way for the user to prevent it. By using specially crafted APIs, app developers can gain access to the accelerometer, magnetometer, and gyroscope sensors. This way, they can track a person even when he/she changes device, push targeted ads, etc. Knowing this, Apple and Google have placed some prevention mechanisms in their browsers and the API access permission framework, but still, sensors need to be used by apps.
from the paper
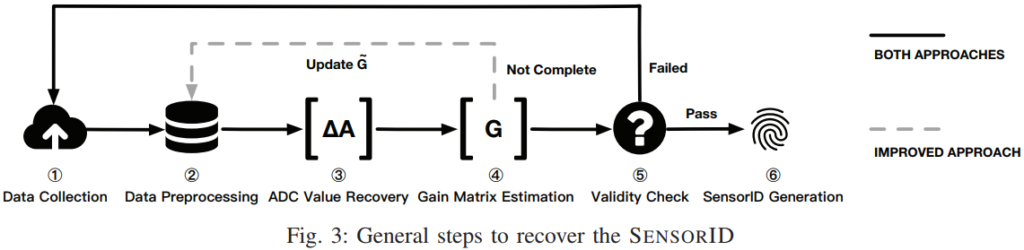
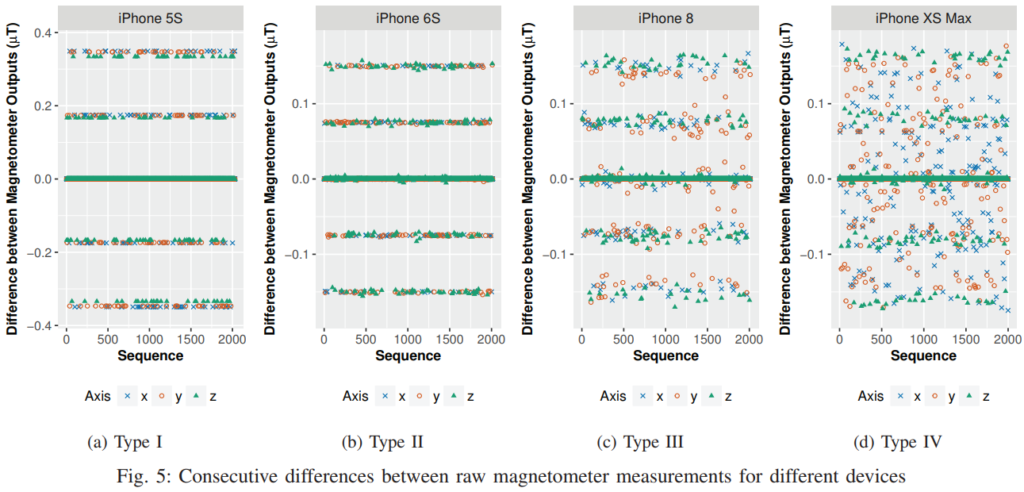
The researchers have followed the approach of inferring the factory calibration data of the device, based on the output of the sensors. Calling it “calibration fingerprinting attack”, they tested it in iPhone devices as well as Google Pixel 2 and 3. The process was conducted with the help of JavaScript data that runs when a user of these devices visits a website through their browser. In less than a second, the researchers were able to get a unique sensor ID profile for the 800 devices tested, while they deduced that factory reset doesn’t change the calibration of the sensors, so the method is considered reliable under all conditions and situations.
from the paper
As the researchers point out, iOS 9, 10, 11, and 12 are maintaining their factory calibration indefinitely, and all devices that have a gyroscope or magnetometer are vulnerable to calibration fingerprinting attacks. Now, whether you are using Safari, Chrome, Firefox, or Opera, it doesn’t matter for this process to work against you. Even privacy-enhanced browsers like the Brave will not be able to stop these attacks or filter the sensor data that leads to the generation of the unique ID. According to another recent study, 2.65% of Alexa’s top 100k websites are collecting device sensor data, with 100 of them exfiltrating it to remote servers.
All that said, the question is what can be done to remedy the problem? First, users could deny apps sensor data access permissions. Secondly, Apple and other smartphone manufacturers could stop calibrating their device sensors in future models, trading some of the sensors' accuracy for user privacy. Finally, the browsers could implement calibration value tampering techniques that would make it impossible for attackers to export a reliable gain matrix. As much as widely exploitable this problem may be right now, there have been no proven cases of exploitation in the wild yet, but no one can rule this possibility out. If you want to do something about it immediately, grab the mobile spin of Tor browser and disable JavaScript.
Have something to say on the above? Leave your comments down below, or on our socials, on Facebook and Twitter.