Businesses in China’s Main Sectors Targeted with Cobalt Strike Payloads
- A new malware campaign using Cobalt Strike targeted technology, finance, and healthcare companies in China.
- The employees were lured with seemingly official archive files holding “important” documents.
- Cobalt Strike implants allow persistent and stealthy access to the compromised system.
A sophisticated covert campaign deployed Cobalt Strike payloads likely delivered through phishing emails, targeting Chinese-speaking businesses across various sectors, including technology, finance, and healthcare has been reported by Securonix. The advanced attack, codenamed SLOW#TEMPEST, has not been attributed yet.
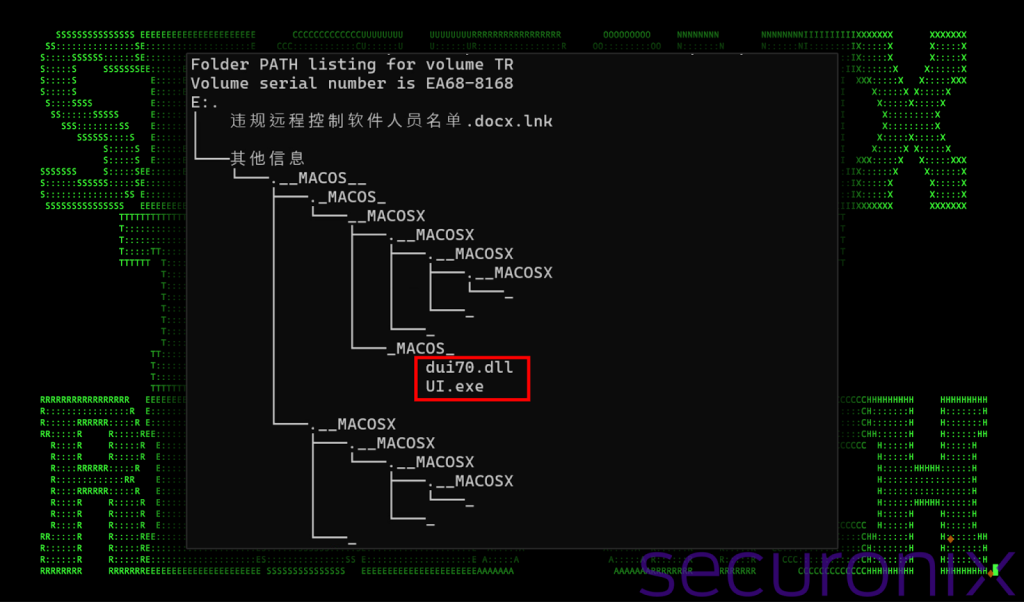
The sophisticated cyberattack targets Windows systems and employs advanced tactics, techniques, and procedures (TTPs) to infiltrate networks and maintain persistence. The attack debuts with a shortcut LNK file that looks like a DOCX file.
The Windows shortcut file is downloaded from a ZIP archive file, sometimes password protected, that security researchers suspect is disseminated via phishing emails.
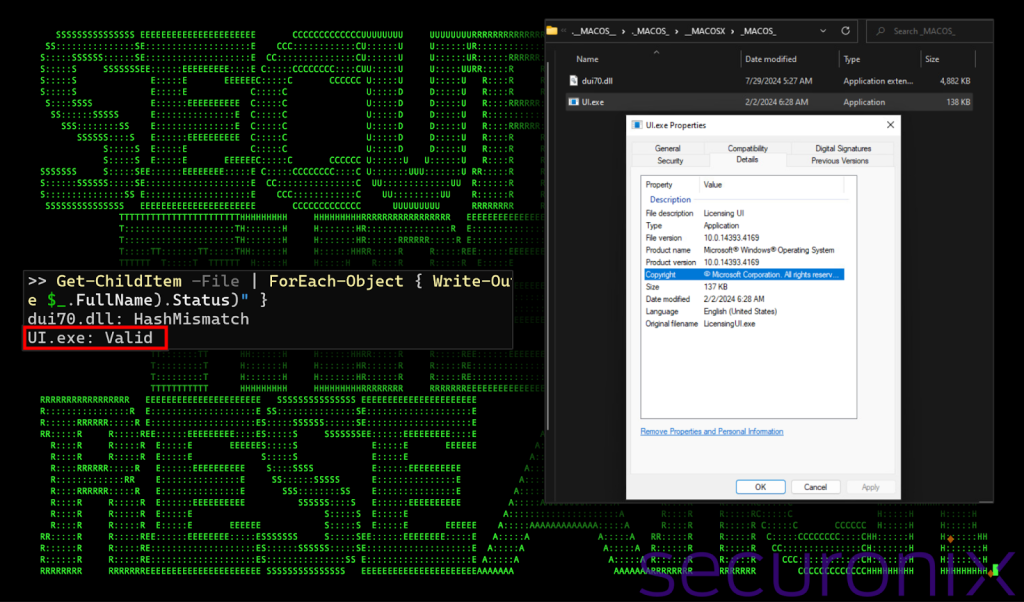
The UI.exe legitimate executable signed by Microsoft, renamed from LicensingUI.exe, displays the software licensing and activation user interface and imports several legitimate DLL files. This executable and a DLL appear in a directory structure mimicking “MACOS” metadata files.
However, same-name DLLs can be sideloaded upon the execution of the renamed UI.exe by the LNK file due to a DLL path traversal vulnerability. The DLL file is a Cobalt Strike implant that allows persistent and stealthy access to the compromised system and injects itself into the Windows binary “runonce.exe.”
Once the system is compromised, the attackers deploy the Cobalt Strike simulation tool used for penetration testing to execute reconnaissance, lateral movement via RDP (Remote Desktop Protocol), and privilege elevation.
The attackers enhance their stealth by elevating the privileges of the Guest user account, converting it into a high-risk backdoor by adding it to administrative groups.
Shenzhen Tencent Computer Systems Company Limited, a Chinese-owned entity, hosted all command and control (C2) infrastructure in China.
Cobalt Strike is a popular tool abused by threat actors for post-exploitation activities, such as lateral movement and data exfiltration. It allows an attacker to remotely access compromised systems and evade detection using advanced techniques like obfuscation and encryption.
However, a disruptive action led by the UK National Crime Agency and coordinated by Europol flagged 690 IP addresses associated with Cobalt Strike criminal activity to 129 online service providers in 27 countries.