The Buckeye Cyber-Espionage Group Used Equation Group Tools Prior to their Leak
- The Buckeye hackers were using Equation Group tools before the Shadow Brokers leak.
- The cyber-criminals were targeting organizations from around the globe at least a year prior to the disclosure.
- Someone continues to use and develop their tools to this day, but Buckeye disappeared in mid-2017.
An investigative report published by the Symantec Corporation researchers tries to shed light on the Buckeye cyber-espionage group and what their relation to the Equation Group is. This is important in helping us figure out who is behind global cyber-criminal operations, what the connection between the various groups is, and how the multiple pieces of information fit in the puzzle of unanswered questions. By better understanding what is going on, companies like Symantec can identify a complete set of indicators of compromise, and develop more effective protection tools.
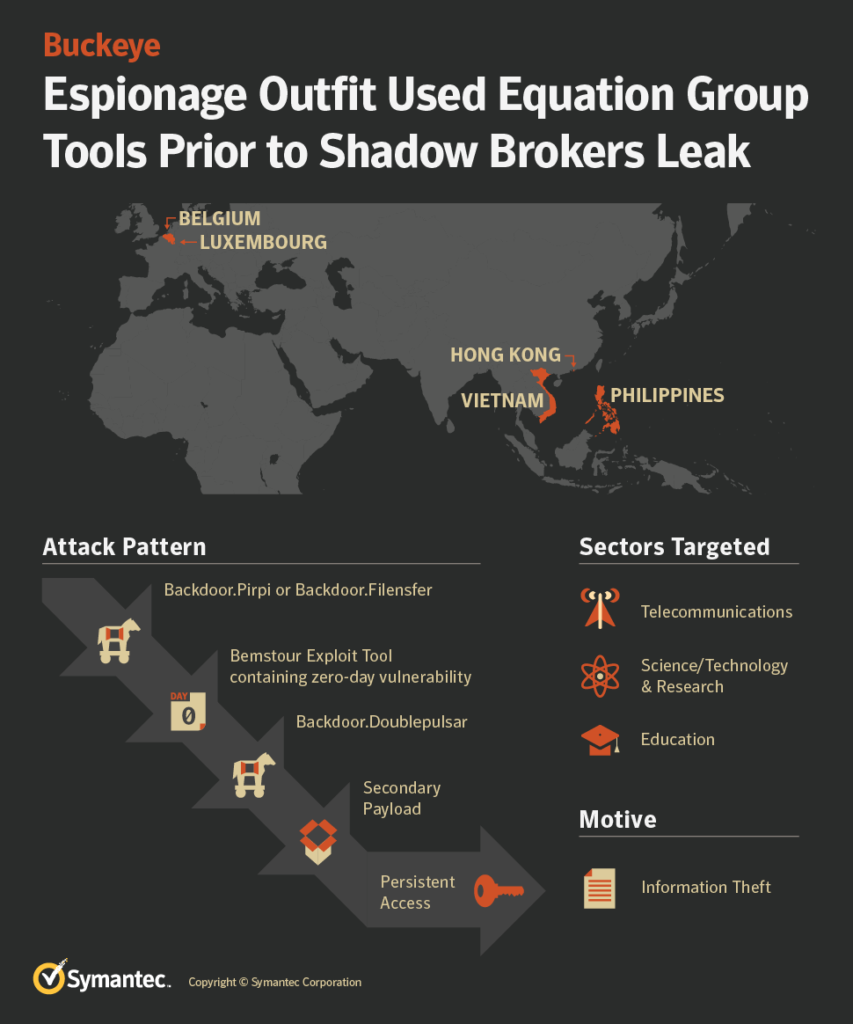
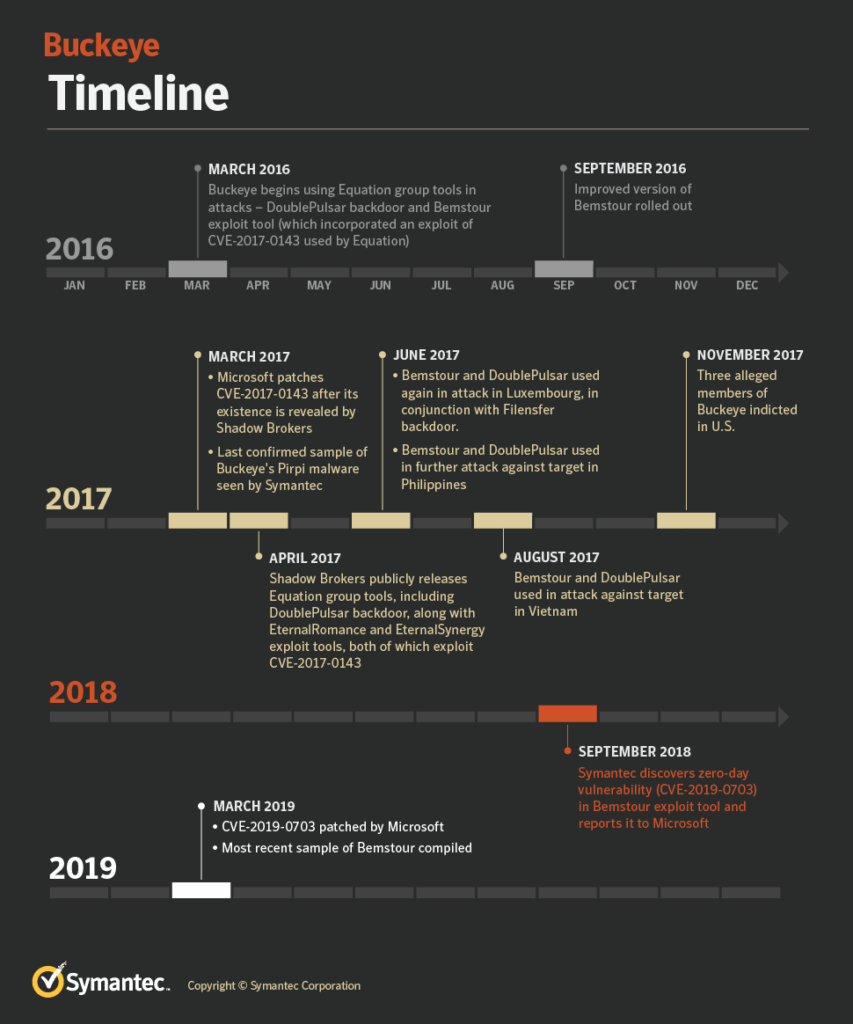
Following the 2017 “Shadow Brokers” leak of the tools used by the Equation Group, many cyber-criminals grabbed the kit and launched devastating attacks against various targets. The exploits that were disclosed back then caused great trouble around the globe, with the WannaCry outbreak being the best example of utilizing these tools, and more particularly the EternalBlue exploit. However, one of the malicious groups, Buckeye, was apparently using the Equation Group tools before 2017, starting from March 2016 when the particular team began using the DoublePulsar backdoor. This backdoor led to the exploitation of two zero-day Windows vulnerabilities that were patched in March 2017, and after the Shadow Brokers leak unveiled them.
image source: symantec.com
Buckeye had stopped their activities by mid-2017, however, their 2016 attacks including a target in Hong Kong and an educational institute in Belgium clearly showed that they somehow had access to the Equation Group exploits. Before seizing fire, Buckeye went on to also target organizations in Luxembourg, Philippines, and Vietnam during the summer of 2017. The development of their signature malware tools, Pirpi and Bemstour, continues by others, and so does the deployment against targets from around the world again.
image source: symantec.com
Symantec researchers assume that Buckeye could have obtained the Equation Group tools by capturing network traffic during observation of an attack, and by reverse-engineering the tools. This scenario is backed by the timing of the attacks and the order by which the features were added on the tools. Another possibility that is not as probable is for a rogue Equation Group member to leak the tools to Buckeye, or even having an unsecured malicious server being infiltrated by Buckeye members who stole the tools. Considering the level of expertise that characterizes the Equation Group, the scenario of the poorly protected server is very dubious.
Have any comments to make on the above? Feel free to leave them down below, or on our socials, on Facebook and Twitter.