BreachForums Vendor Puts GitHub Usernames and Emails on Sale on the Dark Web
- A BreachForums vendor posted about a data sale of GitHub usernames on the marketplace
- They have over 4000 lines of data including original usernames and emails
- Clear Voice, the dark web user who posted about the data sale shared two files for purchase
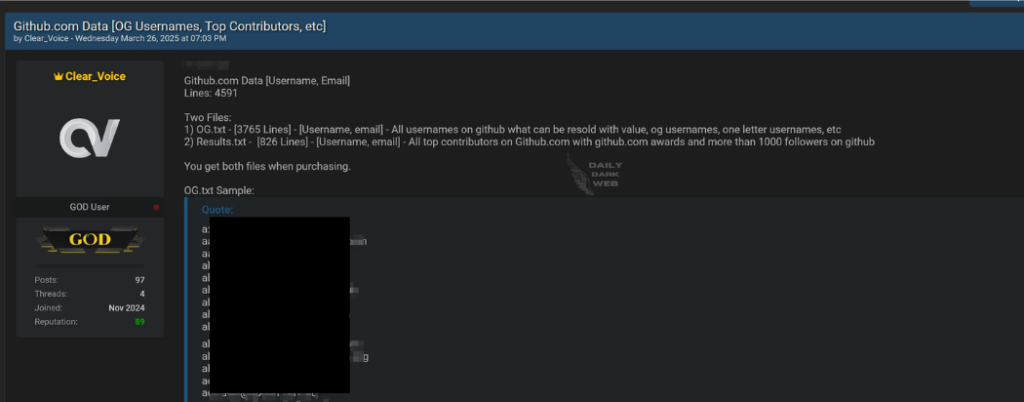
A dark web user, Clear Voice, posted about a sale allegedly of GitHub developers' data. On 26 March the user stated that they were looking for buyers for GitHub.com usernames.
The data with a total of 4591 lines in two files includes the following:
- 3765 lines with all GitHub usernames, emails, and 'one-letter' usernames
- 826 lines of information about top contributors on the proprietary developer platform
- Details of over 1000 followers
The legitimacy of the data purportedly from GitHub could not be verified at the time of posting. However, it could be the result of vulnerability exploitation in the past.
It is not unusual for cybercriminals and dark web vendors to exchange and further exploit stolen credentials on breach forums for financial fraud and phishing scams.
The compromise of GitHub Action was recently in the news for exposing critical CI/CD secrets across multiple repositories.
Continuous Integration/Continuous Deployment (CI/CD) access may expose sensitive data like passwords, API keys, npm tokens, etc. required during the building, testing, and other phases of software development.
It was a supply chain attack that originated from an earlier breach of the ‘reviewdog/action-setup@v1’ GitHub Action via the exploitation of a vulnerability. It was further reported that the primary target of the GitHub breaches was Coinbase, the U.S.-based cryptocurrency exchange.
The attack was launched by injecting malicious code into reviewdog/action-setup@v1 GitHub Action.
GitHub was also impacted in a credentials leak incident in January this year with Cyble reporting the same naming large enterprise security vendors. The incident exposed critical internal systems such as GitHub, Jira, and AWS.
Customer credentials targeting WordPress, Microsoft, and Okta were also exposed in the breach.