BlueKeep Exploit Gets More Reliable with BSOD Problem Fix
- BlueKeep exploit is getting more reliable with a fix that bypasses the Meltdown CPU flaw mitigation.
- Actors have been deploying the original Metasploit code in the wild until now, trying to mine Monero.
- The fix will push more malicious groups to that direction, as the pool of victims remains large.
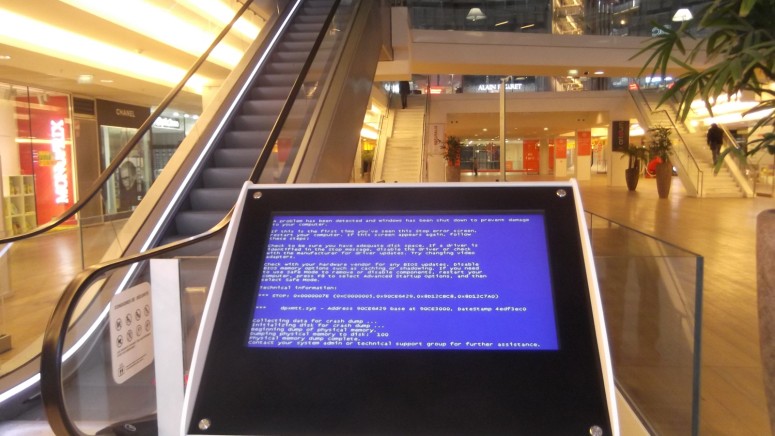
Back in September, we informed you of the first working exploit for the BlueKeep vulnerability (CVE-2019-0708), which targeted 64-bit Windows 7 and Windows 2008 R2. The exploit was developed by Metasploit, after a RiskSense security researcher donated a proof-of-concept code to the penetration testing company. The exploit wasn’t exactly staggering, so an attacker wouldn’t be able to reliably launch attacks that would spread a malicious worm to the hundreds of thousands of vulnerable systems. Last week, we saw the first BlueKeep exploit getting spotted in the wild, with researchers reporting that their honeypots fell into BSOD (Blue Screen of Death).
BSOD is admittedly a problematic state, but it doesn’t enable the attacker to gain access to the compromised system. In this case, the purpose was to drop a Monero miner. This means that the BlueKeep exploit that was used in the wild is based on the Metasploit code, and thus it isn’t very reliable. This is also why the attackers didn’t try to distribute the exploit very aggressively, and neither have they automated their vulnerable system scanning and infection mechanisms. According to ZDNet, however, all of this is about to change soon.
Metasploit and other notable researchers have figured out that the reason why the honeypots were BSODing was that the exploit didn’t work on systems that had received Microsoft’s patch for the Meltdown CPU flaw. Knowing this, the researchers have created a new BlueKeep exploit payload that bypasses the KVA Shadow mitigation (Meltdown), lifting the need to hook the system call. This won’t turn the exploit into a weapon of mass destruction, but it will definitely make it more threatening. Having a more reliable exploit in the hands of actors automatically means a greater incentive to launch attacks against vulnerable systems.
So, how many Windows 7 and Server 2008 are still vulnerable to this flaw in the Microsoft Remote Desktop Protocol service? In July, Binary Edge reported 890k IP addresses that were still vulnerable. This number has inevitably dropped since then, but experts believe it isn’t below 300k. After all this time, these systems will most probably not be patched, ever. For them, the only way to protect against the rising threats is to disable the RDP services, block port 3389, and enable Network Level Authentication (NLA).
Do you see BlueKeep exploits becoming a real problem, or do you think that the situation is already deflating? Let us know what you think in the comments down below, or on our socials, on Facebook and Twitter.