BlackSuit Ransomware Group Claims the KADOKAWA Cyberattack
- KADOKAWA Corporation announced its servers were breached earlier this month, affecting Niconico and related services.
- The BlackSuit ransomware group claimed the cyberattack and is asking for ransom by the end of the month.
- The company did not comment on whether they intend to make the payment before the deadline expires.
Japanese publisher KADOKAWA says the June 8 cyberattack, including ransomware, crippled multiple websites of the KADOKAWA Group, targeting popular video-sharing platform Niconico and related services, affecting manufacturing, distribution, and Web services and merchandise businesses. On June 27, the BlackSuit ransomware gang claimed this attack.
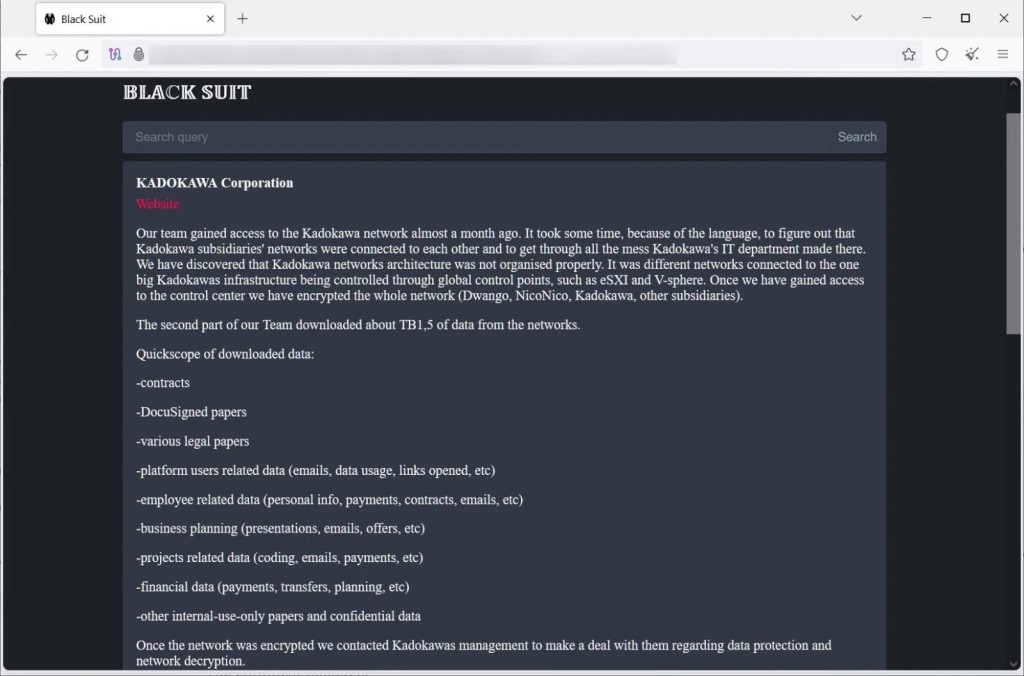
The treat actor expects a ransom to be paid by July 1 to refrain from leaking the alleged data trove they own. They say they obtained it by breaching the company’s systems a month ago, even mentioning that the “KADOKAWA network architecture was not organized properly.”
The hacker group published a sample of the stolen information on their leak site, boasting about 1.5TB of data, including financial data, contracts, business plans, private legal documents, and user and employee details from Dwango, Niconico, KADOKAWA, and other subsidiaries.
As KADOKAWA Corporation continues its investigation, KADOKAWA Group’s data center remains largely affected, with many servers still down. The company is issuing an apology to its readers, users, writers, creators, business partners, shareholders, investors, and stakeholders.
The BlackSuit ransomware gang is also suspected to be behind a recent data breach impacting retail technology and software provider CDK Global. The huge security incident caused significant disruption to nearly 15,000 car dealerships in the U.S., and the cybercriminals demanded tens of millions of dollars in ransom.
BlackSuit is a suspected rebrand of the Royal ransomware operation, which is believed to be the successor of the Conti cybercrime group of Russian and Eastern European threat actors. Earlier this month, BlackSuit allegedly published hundreds of sensitive police files stolen from the Kansas Police Department after the KCKPD refused to pay ransom.