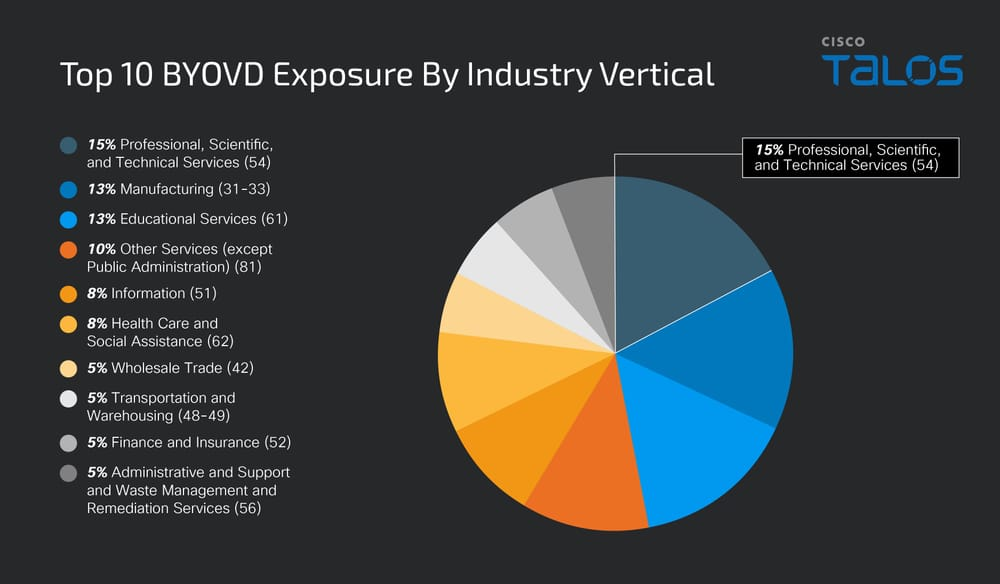
BlackByte Ransomware Group Exploits Authentication Bypass Vulnerability in VMware ESXi
- The BlackByte ransomware group is apparently intensifying its efforts, adding new elements to its usual operating style.
- Security experts observed the gang exploiting a VMware ESXi authentication bypass vulnerability shortly after its publication.
- The victim organization’s VPN was leveraged for initial access in one of the analyzed cases.
The BlackByte ransomware group started exploiting an authentication bypass vulnerability in VMware ESXi right after it was disclosed, the latest Cisco Talos Incident Response (Talos IR) report said. The threat actors were observed adding new tactics, techniques, and procedures (TTPs).
The BlackByte ransomware-as-a-service (RaaS) group continues to leverage the same TTPs, using vulnerable drivers to bypass security controls and deploying self-propagating ransomware with worm-like capabilities, known-good system binaries (LoLBins), and other legitimate commercial tools, but it recently strayed from this path.
Recently, hackers were seen exploiting the CVE-2024-37085 authentication bypass vulnerability in VMware ESXi. They used a victim’s authorized remote access tool instead of their usual commercial remote app, such as AnyDesk.
A new iteration of the BlackByte encryptor drops four vulnerable driver files as part of their usual Bring Your Own Vulnerable Driver (BYOVD) technique and uses victim Active Directory credentials to self-propagate.
A recent BlackByte ransomware attack gained initial access using valid credentials to access the victim organization’s VPN via an initial account with a basic naming convention and, reportedly, a weak password.
The VPN interface may have allowed a domain account to log in without multi-factor authentication (MFA) due to a specific Active Directory configuration. The initial access vector may have been brute-force authentication facilitated via internet scanning.
By compromising two Domain Admin-level accounts, one of which was used to access the organization’s VMware vCenter server, privilege escalation was possible. This account was used to create Active Directory domain objects for individual VMware ESXi hypervisors and create and add several other accounts to an Active Directory group called "ESX Admins."
Successful exploitation of CVE-2024-37085 grants members of a specific Active Directory group elevated privileges on an ESXi host: control over virtual machines (VMs), modification of the host server’s configuration, and access to system logs, diagnostics, and performance monitoring tools.
First observed in mid- to late-2021, BlackByte is believed to be an offshoot of the infamous Conti ransomware group. Over time, it has reengineered its ransomware binary with versions written in Go, .NET, C++, or a combination of these languages.
In 2021, cybersecurity company Trustware released a free decryptor for BlackByte on GitHub, which leveraged a design flaw in the ransomware’s encryption protocol to unlock stored files.