BitDefender Antivirus Free 2020 Vulnerable to Privilege Escalation Attacks
- SafeBreach discovers yet another privilege escalation vulnerability on a security product.
- The flaw has similar grounds and method of exploitation as with last week’s news about Trend Micro.
- The root cause is again the lack of control in the DLL loading path and the absence of certificate validation.
As reported by SafeBreach Labs and its security researcher, Peleg Hadar, the most recent free version of the BitDefender Antivirus was vulnerable to privilege escalation attacks until yesterday. The vulnerability which was given the identifier CVE-2019-15295 was discovered on July 17, confirmed by BitDefender on August 14, and patched on August 19. Thankfully, BitDefender Antivirus Free is auto-updating when a critical patch is available, so you’ll have to do nothing to fix the problem if you’re using the product.
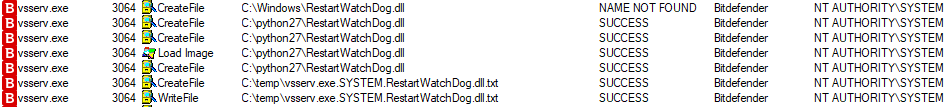
The intriguing part of this story is that the escalation flaw is very similar to the one that we saw last week with Trend Micro’s Password Manager. In the case of the BitDefender, we have the execution of the Windows service “NT AUTHORITY/SYSTEM” which enables the software to access the system with powerful permissions, which is the same basis as with Trend Micro’s product. Next, an attacker could use an unsigned arbitrary DLL and load it into multiple services to run as “NT AUTHORITY/SYSTEM”, leading to privilege escalation and high persistence exploitation scenarios. To make things even worse, whatever unsigned code is set to run is not passed through the CIG (Code Integrity Guard) mechanism.
SafeBreach demonstrated a proof of concept (PoC) code by using a Python script to write files onto the Access Control List (ACL) after fiddling with the non-admin writing permissions to the target directory as required. This same directory must be added onto the system’s PATH variable, in the same way, that the exploitation with Trend Micro password manager worked. The DLL that is decoyed is “ServiceInstance.dll”, which is parsed upon system boot without any digital certificate validation against the binary.
image source: https://safebreach.com
The free edition of the BitDefender Antivirus is very widely used, and it consistently scores high in reviews. People love it for being fully automated, simple to use, light on resource capturing, offering full web protection, and being mighty in detecting threats. That said, the number of people who ran the risk of privilege escalation lately was pretty large. Now, since a similar exploitation method worked for two top-rated security software tools coming from BitDefender and Trend Micro, would it be safe to assume that SafeBreach has more to unveil about other products that run as “NT AUTHORITY/SYSTEM”? We asked Peleg Hadar the exact same question, and he told us that there are actually many more vulnerabilities of this kind out there, but he can't reveal anything just yet as the vendors will need to roll out the fixing patches first. Stay tuned!
Have something to say on the above? Feel free to leave your comments down below, or discuss this topic with our socials community on Facebook and Twitter.