The “Bitcoin Twitter Hack” May Have Started With a Slack Compromise
- The Twitter hackers may have used a Slack workspace as a gateway into the platform’s internal admin panel
- Researchers have counted thousands of sensitive Slack credentials offered for purchase on the dark web.
- Twitter employees could have stored sensitive credentials on Slack, and rumors have it that this is what happened.
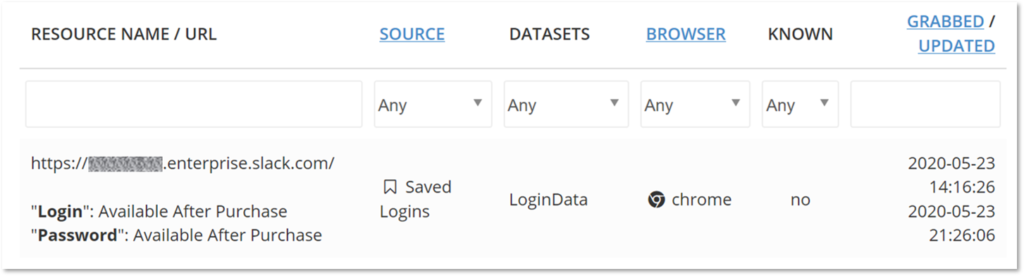
According to rising speculative theories, the actors behind the “Bitcoin Twitter hack” may have found their way into the social media company’s systems through Slack. At the end of last month, researchers at KELA noticed a rising wave of Slack credentials being offered for purchase on the dark web.
Upon further investigation, they’ve found that there were at least 17,000 Slack credentials sold in the ‘Genesis Store’ alone, priced between $0.5 and $300, depending on how valuable they were. While a connection with the recent Twitter hack isn’t based on concrete evidence, there are indications pointing to this scenario.
Related: Now-Fixed Slack Bug Allowed Automatic Account Takeovers
the Twitter hacker reportedly got access to Twitter’s admin panel by finding login credentials pinned inside a Twitter Slack channel. If that’s true then holy shit. https://t.co/Oek9SEjzHo pic.twitter.com/Z1496dok6G
— Tom Warren (@tomwarren) July 17, 2020
Reporters have been tweeting about this possibility for a few days now, so it is likely that the social media company’s internal investigation has yielded something along those lines.
For the hackers to be able to access the internal Twitter admin panel and manipulate the 2FA settings of user accounts, they either had to convince Twitter employees to work with them or compromise the admin accounts directly. The former assumption was prevalent during the first hours after the incident, but it may not have been the case after all.
Source: KELA
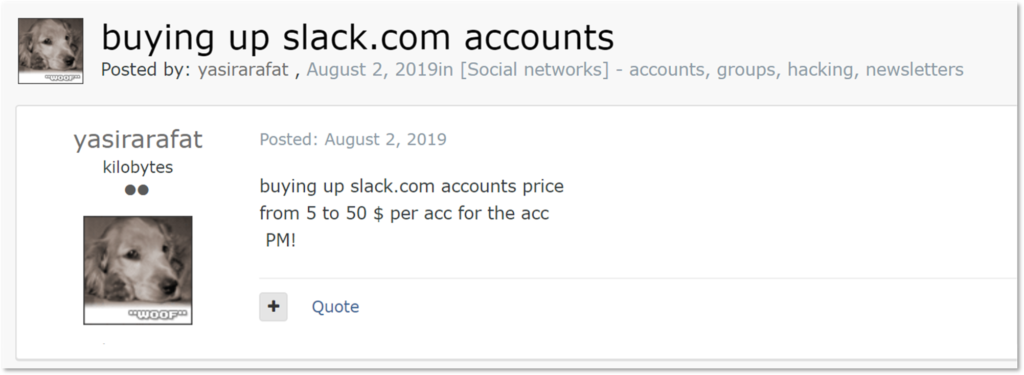
From what appears to be trending on dark web markets, Slack workspaces are a hot item to trade right now. KELA estimates that over 12,000 workspaces have been compromised, with many belonging to large companies and organizations that use Slack for communications.
Related: The Day After Twitter’s Massive and Embarrassing Bitcoin Hack
KELA found 4,368 entries that are limited to formatted email registration, meaning that only users owning addresses from specific domains would be allowed to join. If someone was to use these credentials to join a workspace, they would be able to look into the user’s drafts, personal items, saved notes, and more, oftentimes comprising credentials too.
Slack isn’t a password manager featuring an encrypted vault, but many feel comfortable utilizing it as such, just to keep everything in one place.
Source: KELA
Another potential method for actors to grab the credentials of the compromised user is to ask. When there’s nothing around to grab right away, the actors may reach out to the admin through a DM on Slack, and pretend that they somehow lost the password or they need a reset to a different email address.
Again, this working out is pretty high, because Slack creates a false sense of trust among the members of a workspace.