Bitcoin Scam Campaign Tricks People into Running Ransomware
- A tool that is supposedly a Bitcoin miner is actually a payload retriever.
- The payloads can be a Trojan or ransomware and are running on the background.
- Victims are promised Bitcoin and Etherium for using the tool and promoting it.
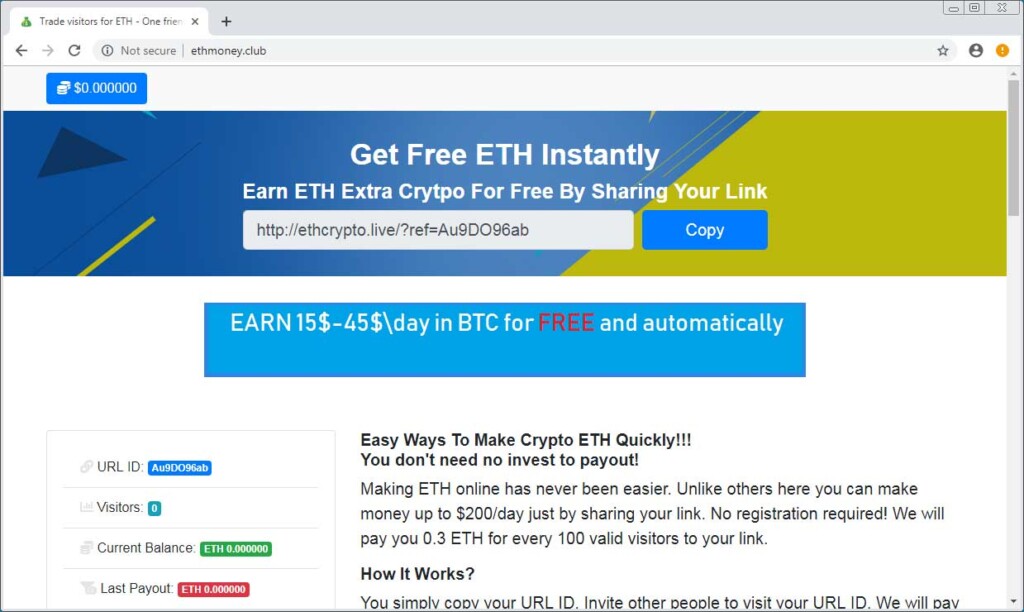
According to a report by a security researcher nicknamed “Frost” on Twitter, there’s a new type of scam campaigns that are tricking credulous people into running ransomware and Trojans on their system, thinking that they are about to bite a piece of the Bitcoin pie. The campaigns circulate the promise of the user winning from $5 to $45 worth in Bitcoins every day, by running the provided “Bitcoin Collector” application. This utility though is not even remotely related to cryptocurrency mining, as its only job is to install ransomware and password-stealing Trojans on the victim’s system.
image source: bleepingcomputer.com
Even the part of promoting the fake utility involves a promise for winning money in cryptocurrencies, with those that refer 1000 others to the promotional site earning 3 Etherium. The equivalent in USD is $750, so many would go to great lengths to achieve the referral target.
The “Bitcoin Collector” tries to convince people that they have gotten the real deal by providing a VirusTotal link that shows no warnings about any risky detections. Upon the running of the “BotCollector.exe” executable, which is contained in the downloaded ZIP archive, the utility starts its pretending “mining”, while malware is launched in the background, without giving the user any indication about it of course.
image source: bleepingcomputer.com
BleepingComputer has analyzed various samples of the Bitcoin Collector program and figured out that the payload that runs upon the clicking of the “Start” button is not a standard choice, but depends on the currently running campaign. Sometimes it’s ransomware, others it’s a password-stealing Trojan, and others it’s empty with no payload assigned to it.
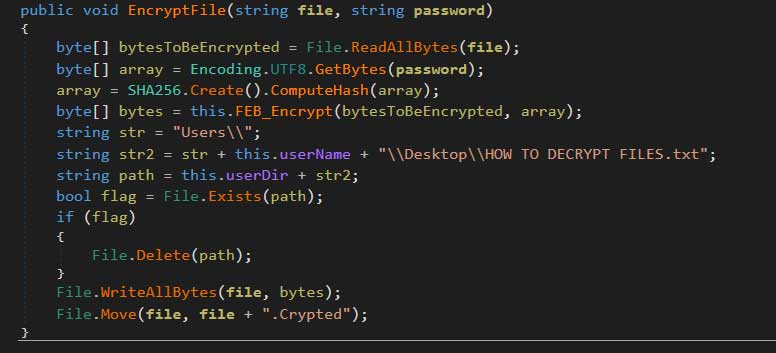
If you are unlucky enough to get the “ransomware edition”, your files will be encrypted and get the ".Crypted" extension, asking you to contact the attacker at “[email protected]” in the next 48 hours. Those who don’t are warned that their files will be irreversibly deleted, and are even advised that reinstalling the OS won’t change anything. No matter the claims made by the ransom actors, there’s a decryptor for this case as the ransomware is basically just a “HiddenTear” variant.
image source: bleepingcomputer.com
If you get the “Trojan iteration”, you are basically getting the Baldr tool that connects to a malicious C&C server and sends whatever passwords and login credentials it can catch from your online activity. Baldr is also capable of stealing files from your computer, retrieving your browser history, or even capturing screenshots and sending them to its masters.
Have something to share on the above? Let us know of your opinion in the comments down below, and also on our socials, on Facebook and Twitter.