BendyBear Is a Next-Gen Shellcode Featuring Custom Cryptographic Routines
- Researchers have analyzed BendyBear’s 10,000 bytes of code piece by piece, finding much sophistication.
- The malware is a stage-0 tool that is serving as a stealthy fetcher of more dangerous payloads.
- The tool is deployed by the “BlackTech” group of hackers linked with the Chinese state.
Researchers of Unit42 (Palo Alto) have analyzed the BendyBear malware code to figure out how it works, what it can do, how versatile it is, and in what ways it attempts to hide itself or its activities from security solutions. The particular sample analyzed by the team of researchers is the same that was used in the 2020 attacks against the Taiwanese government and corporate entities, and which was shared by the country’s Ministry of Justice Investigation Bureau.
In August 2020, when these attacks took place, the fingers were pointed at the Chinese state. Indeed, the researchers now confirm that the particular malware is used by the “BlackTech” cyber-espionage group, which has been confirmed to have ties with China's government.
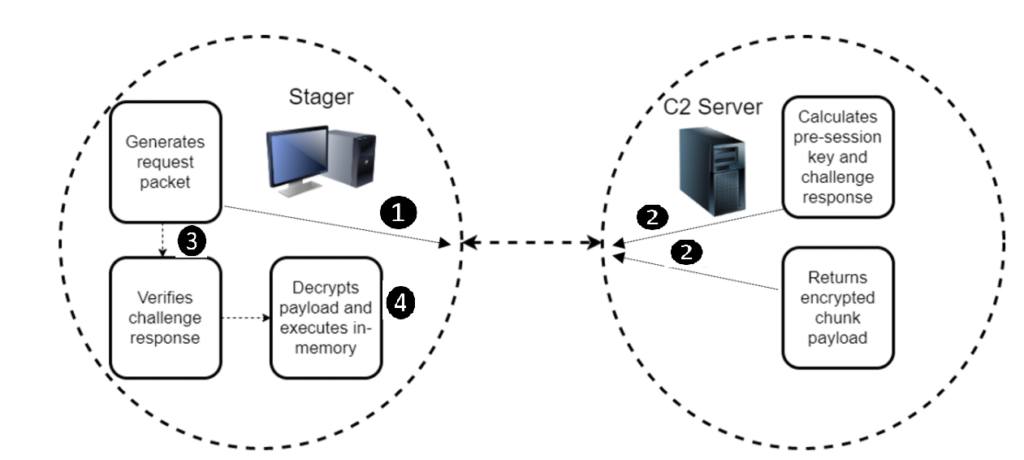
The x64 shellcode of the analyzed sample is a stage-zero malware meant to help the actors in the fetching and planting of a more robust payload from the C2. For a shellcode, the 10,000 bytes of BendyBear make it extraordinarily large, so here’s what it achieves through size and complexity:
- Transmits payloads in modified RC4-encrypted chunks. This hardens the encryption of the network communication, as a single RC4 key will not decrypt the entire payload.
- Attempts to remain hidden from cybersecurity analysis by explicitly checking its environment for signs of debugging.
- Leverages existing Windows registry key that is enabled by default in Windows 10 to store configuration data.
- Clears the host’s DNS cache every time it attempts to connect to its C2 server, thereby requiring that the host resolve the current IP address for the malicious C2 domain each time.
- Generates unique session keys for each connection to the C2 server.
- Obscures its connection protocol by connecting to the C2 server over a common port (443), thereby blending in with normal SSL network traffic.
- Employs polymorphic code, changing its runtime footprint during code execution to thwart memory analysis and evade signaturing.
- Encrypts or decrypts function blocks (code blocks) during runtime, as needed, to evade detection.
- Uses position independent code (PIC) to throw off static analysis tools.
In summary, BendyBear ensures that all functions and data transfer processes are taking place behind strong encryption, significantly lowering the chances of detection by network security solutions. Considering that the nasty piece of malware features sophisticated anti-analysis techniques like modified RC4 encryption, signature block verification, and polymorphic code, it actually appears smaller than expected, so it’s pretty lean and optimized.
Compared to the “WaterBear,” which was used previously by the same group of actors, BendyBear is lighter, features the additional encryption of XOR, and is naturally less dangerous on its own since it's a stage-0 malware. WaterBear is a stage-2 implant with many capabilities, including network traffic filtering, process hiding, and API hooking.