AWS Tools and Stolen Credentials Exploited by EC2 Grouper Hackers Targeting Cloud Environments
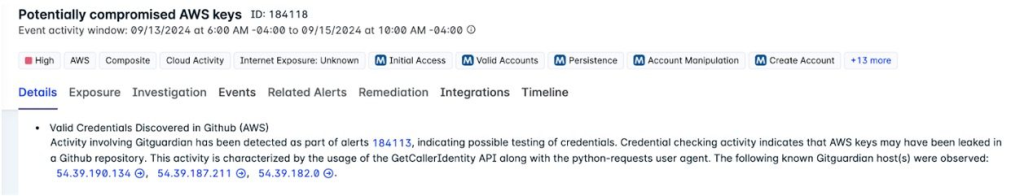
- The EC2 Grouper threat actor compromises credentials sourced from code repositories linked to valid AWS accounts.
- These are then combined with various AWS tools to attack cloud environments.
- Their end goal is most probably crypto mining, but security researchers do not have any proof yet.
A sophisticated hacker gang dubbed EC2 Grouper was observed abusing AWS tools and compromised credentials to target cloud environments, leveraging APIs for reconnaissance and operational setup within the cloud environment.
Over the past few years, this threat actor has been observed infiltrating dozens of customer infrastructures, making it one of the most active and closely monitored groups in the cybersecurity landscape.
According to Fortinet researchers, EC2 Grouper is distinguished by its consistent use of AWS-native tools, such as PowerShell, to execute its attacks. The group has developed identifiable patterns, including a unique user agent string and repetitive security group naming conventions.
Researchers noted naming conventions like “ec2group,” “ec2group1,” and up to variations such as “ec2group12345,” which are used to create multiple security groups.
The group primarily compromises credentials sourced from code repositories linked to valid AWS accounts. Common activities include calls to inventory EC2 instance types and identify available AWS regions, as well as resource configuration to enable remote access.
However, an anomaly was observed during these attacks – EC2 Grouper does not use necessary calls to configure inbound access to EC2 instances, raising questions about the group’s specific techniques and objectives.
Though their ultimate goals remain unclear, experts suggest resource hijacking—such as using compromised environments for cryptocurrency mining—may be a primary motive. The absence of any manual actions or tailored objectives within compromised environments further aligns with this hypothesis.
Recently, a significant Amazon Web Services (AWS) Cloud Development Kit (CDK) flaw was discovered that permitted full account takeovers under certain conditions.