Researchers Find Ten Year Old Vulnerability on Avaya Deskphone
- McAfee researchers have discovered a severe RCE flaw on Avaya’s H.323 firmware.
- The security flaw affects a wide range of IP deskphone devices, allowing audio exfiltration.
- The component that introduces the security risk is ten years old, coming with a known exploit.
Avaya is a California-based company who has been specializing in business communications since 2000. Their VoIP solutions cover 90% of Fortune 100 companies, so the presence of a vulnerability in their deskphones can affect large corporations and interrupt critical business processes. As McAfee researchers reveal, this is precisely the case with the Avaya 9600 series IP Deskphone, which reportedly carries a remote code execution (RCE) vulnerability that dates to ten years ago. The particular flaw allows the exfiltration of audio from the speaker of the targeted phone, and it only requires a laptop to be connected to the same network with the IP deskphone.
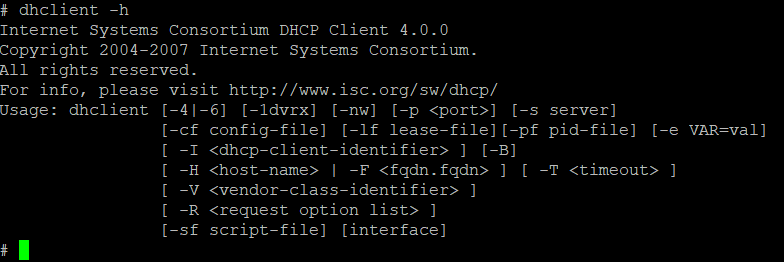
The researchers have demonstrated how exploitation works in the video below. The same method works for Avaya 9600 Series, J100 Series, and B189 products. Anyone using the H.323 firmware version 6.8.1 and earlier is vulnerable, however, the SIP versions aren’t affected by the flaw. Identified as CVE-2009-0692 and given a CVSS v2.0 score of 10.0 (highest), the particular RCE vulnerability became part of Avaya’s firmware ten years ago through an open-source component called “Dhclient” and then left unpatched for over a decade.
Avaya has published a fixing firmware update on June 25, following McAfee’s notification. It actually took Avaya two months to release a patched firmware image, which is acceptable considering the amount of testing that these devices have to undergo in order to ensure that they’re reliable for large enterprise deployment. Now, IT administrators are urged to replace the old firmware images with the latest version, as they are running a severe risk for corporate espionage. It is not known if anyone has taken advantage of the particular vulnerability yet, but with the importance of Fortune 100 operations, we can safely assume that someone must-have.
image source: securingtomorrow.mcafee.com
The researchers found the vulnerability by recovering system files and figuring out ways to interact with the system in a privileged fashion. Recovering all system binaries and configuration files is the first step to locating vulnerability points by using a debugger. Once the researchers managed to access the root shell of the device, they could run any code they wanted, tamper with the NAND flash, and modify the boot arguments of the Linux kernel that is used on the Avaya firmware. This is how the researchers figured out that the dhclient version was 4.0.0, which dates ten years back, and which has a publicly available exploit. As McAfee’s specialists point out, it would take a skilled attacker a couple of weeks, or even a few days to come up with the same results as they did.
Feel free to share your thoughts in the comments section down below. Alternatively, join the discussions on our socials, on Facebook and Twitter.