Auditors Report Nothing Changed in America’s Cybersecurity on the Federal Level
- DHS investigators return with their bi-yearly cybersecurity report, and give an overall “C-”.
- Most agencies and departments are still plagued by the same problems they had two years ago.
- The problem remains the lack of a central authority that is responsible for federal cybersecurity.
Two years back, the report of a sub-committee of investigators of the U.S. Homeland Security and Government Affairs was ringing the bells of warning to government agencies, raising very worrying issues around their security stance against even the most basic threats. Two years after that report gained much publicity, the same auditors returned with a 2021 report showing nothing changed. America’s data is still at risk, and reporting about it doesn’t seem to make any difference in providing an incentive to fix the underlying issues.
In summary, the tests conducted in 10 Federal Government Departments in the U.S. revealed the existence of 450 critical-risk vulnerabilities and 736 high-risk outstanding flaws. In 60% of the sample accounts tested, employees who left the agencies had their accounts remain active for extended periods of time. Also, thousands of IT devices used in the departments were not even registered or part of their official records.
At least seven agencies were determined to operate unsupported legacy systems, which carry a mind-boggling amount of unpatched vulnerabilities. Finally, data encryption, multi-factor authentication, and limiting user access to information and systems were inconsistently followed or not implemented at all.
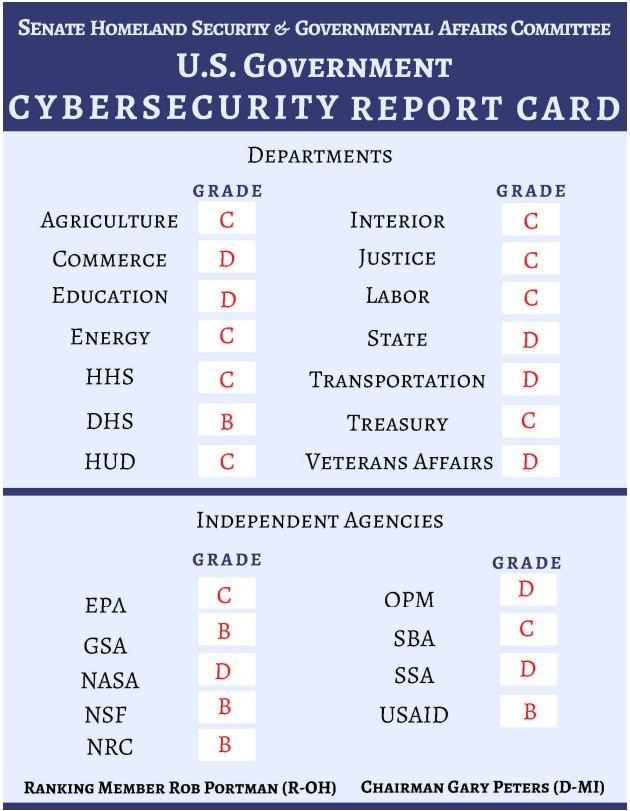
The grades given to the departments are shown in the image below. The only one from the federal government that scored a “B” was the Department of Homeland Security, whereas independent agencies did a little bit better in general. The overall score of a “C-”, which is a disheartening result after all these years of investigations, findings, and recommendations.
According to the report, the main problem seems to be the absence of a unified cybersecurity strategy plan to combat the current situation. There’s no single point of accountability for federal cybersecurity, so nobody is burdened with the responsibility to develop and implement strengthening plans. Additionally, the report points out that CISA needs to assume a more central role as the operational lead for federal cybersecurity, and Congress should update the ‘Federal Information Security Modernization Act of 2014’ to reflect the current situation.
Whether or not the efforts and incentives of the Biden administration will have any measurable effects is to be seen in the next report by the DHS, which is expected in 2022. The problems are definitely neither few nor simple to address in a short time, but at least getting those Windows 7 systems finally upgraded to 10 would be a step forward for starters.