Attackers Use Variation of Old ‘Hello Pervert’ Email Spoofing Technique in Sextortion Scams
- A new wave of email scams relies on a new variation of the classic “Hello pervert” technique.
- Attackers claim to have breached the recipient’s email and ask for a ransom for allegedly stolen compromising materials.
- The email is designed to spark fear and panic, pushing victims to act impulsively without verifying the claims.
Cybercriminals are once again leveraging sextortion scams to extort victims, this time employing email spoofing techniques in an attempt to create panic and elicit payments. These scams are a new variation of “Hello pervert” emails.
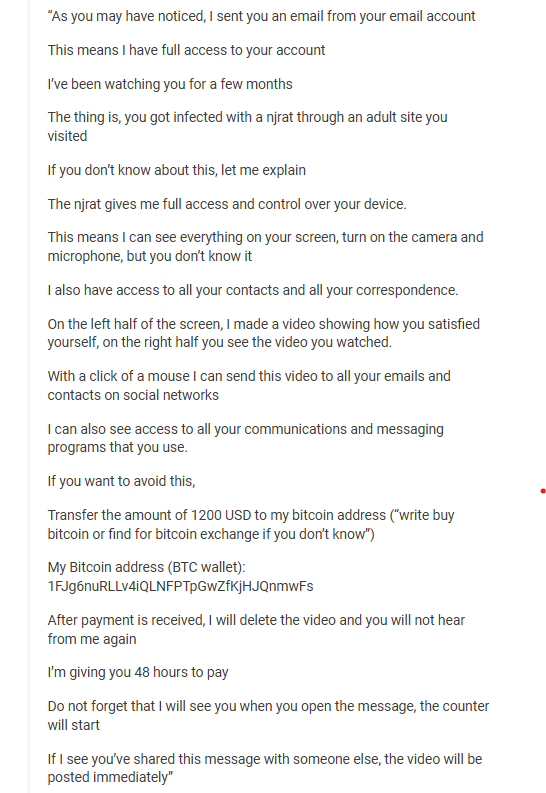
The emails falsely claim that the victim’s device has been hacked via a remote access trojan (RAT) and threaten to expose compromising recorded footage, according to a report from Malwarebytes Labs.
The scam begins with spoofed emails that appear to be sent from the recipient’s own account, tricking victims into believing their email or device has been compromised.
The email typically claims the attacker has used a malware infection, such as njRAT, to gain unauthorized access to the victim’s device, allegedly allowing them to activate cameras, capture screen recordings, and steal contact lists.
Victims are told this stolen access has been used to record inappropriate activity and are threatened that the alleged footage will be sent to their contacts unless they transfer a ransom of $1,200 in Bitcoin within 48 hours.
Email spoofing enables attackers to forge email headers, making it seem as though a message originated from the recipient’s own account. Although this tactic has been used in various phishing schemes, its implementation here is meant to heighten anxiety by creating the illusion of a compromised email account.
The njRAT malware mentioned in such scams has serious capabilities, including keylogging, stealing credentials, and enabling camera access, adding a layer of perceived credibility.
Clear indicators of a sextortion scam email are a spoofed sender address that appears to come from the receiver’s own email and accusations of inappropriate online behavior combined with claims of recorded footage.
So are references to Trojans like Pegasus or njRAT claiming control over your device, demands for Bitcoin payments, often with threats of immediate exposure, or messages presented in attachments that bypass spam filters.