A Decade of ATM Malware Evolution and Deployment
- ATM malware has been around for ten years now, and it's growing stronger.
- Attackers can trick the machine into dispensing all their cash out or steal card data.
- The number of samples and families is growing, but the field remains highly specialized.
Cisco Talos did an interesting retrospective in the last ten years of ATM (Automated Teller Machines) malware activity and evolution, how it got to be in the first place, and how it grew into what it is today. As Talos researchers point out, it all started with the discovery of "Skimer", after malware developers discovered that all ATMs are using a generic Windows extension for Financial Services API which they could leverage. Skimer was tricking the machines into spewing out cash (jackpotting) even without using a card. Skimer was used as the basis for the development of more sophisticated versions that we have today.
image source: blog.talosintelligence.com
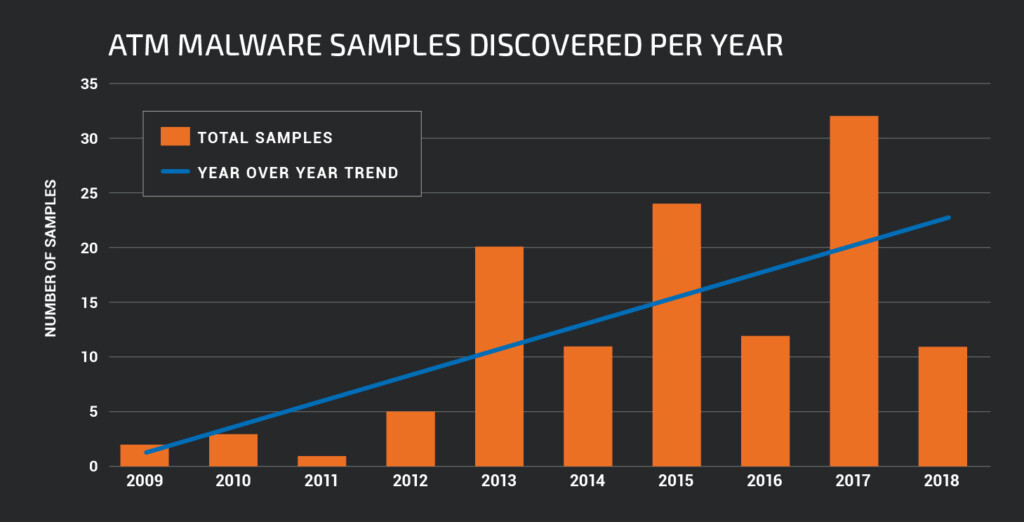
ATM malware is a very niche kind of malicious software, accounting for the smallest percentage of malware type. The Talos researchers report that each year, this small number of samples grows steadily. The kinds of malware that can infect an ATM machine include the following:
- Malware that has to be installed through USB, by physically accessing the machine.
- Malware that can be installed remotely after compromising the bank network.
- Malware that makes the ATM dispense all of its money bills.
- Malware that can steal the users' card details from the ATM machines.
image source: blog.talosintelligence.com
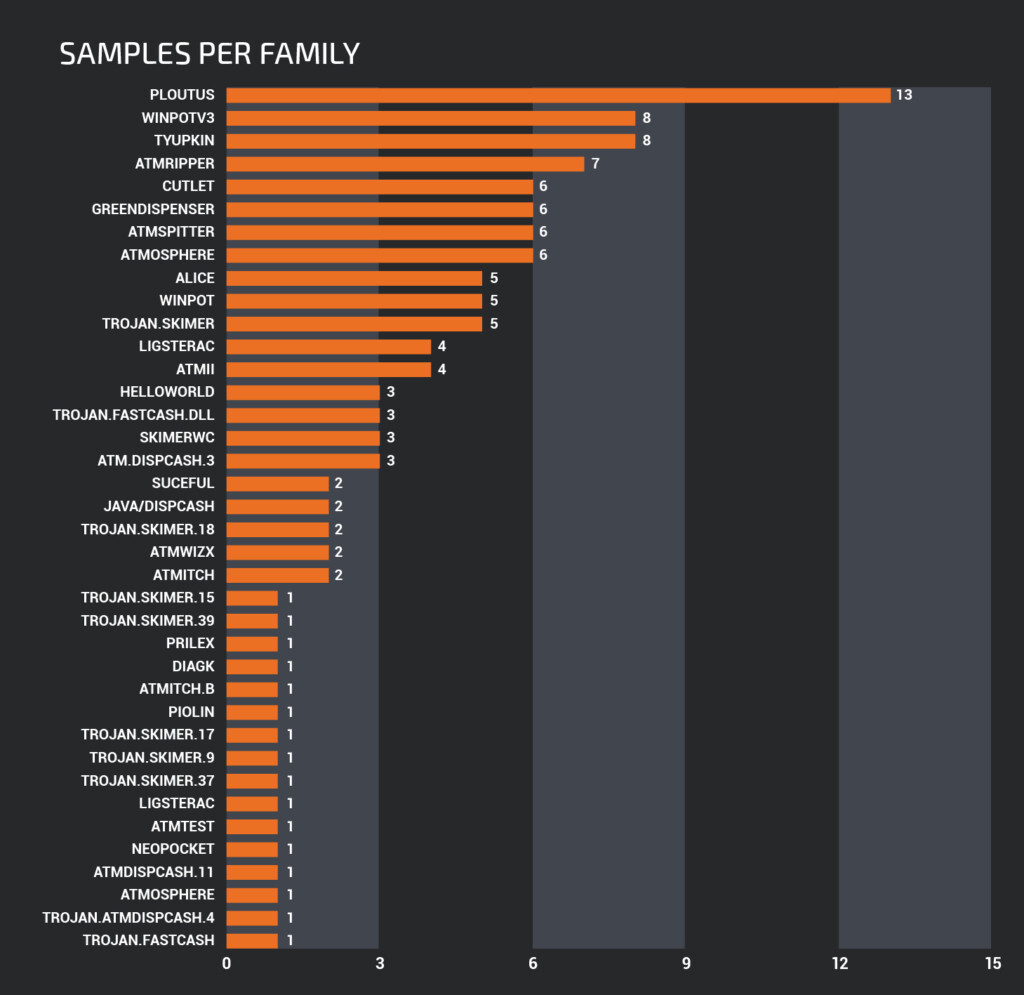
Talos has analyzed samples from more than 30 malware families in the past decade, with the most widely used being Ploutus, Winpotv3, Tyupkin, and ATMripper. Ploutus is mostly active in Latin America, and it's a jackpotting ATM malware. For its installation, the attackers will have to access the USB ports or CD-ROM drive of the ATM. Newer versions of Ploutus that are extensively deployed in the US as well are very versatile and work well with ATMs from various vendors while requiring only minimal modifications.
image source: blog.talosintelligence.com
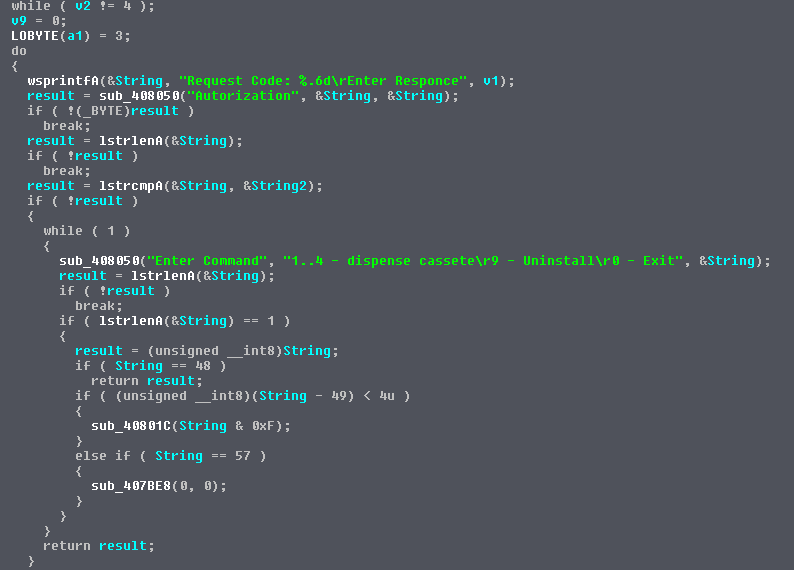
The Skimer, which was the one that started it all, is employing money mules to collect the stolen card data and dispense cash. It is activated by a secret code that activates a backdoor and displays a selection menu that lets the attacker empty one of the cash-dispensing modules of the ATM.
image source: blog.talosintelligence.com
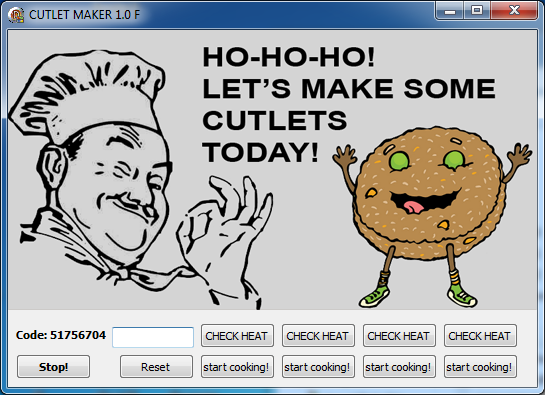
Among the many others, there's one that stands out due to the fact that lets attackers "cook" their own malware spin. Called the "Cutlet Maker" this is a do-it-yourself kit that has been available for sale in darknet marketplaces since 2016, even coming with instructions in Russian and English, detailing how one can acquire the cash-dispensing codes, etc. The instructions even offer advice on how to minimize the chances of getting caught, and there's also a testing sandbox called "Stimulator" that provides an opportunity for practice.
Are you ever afraid that the ATM you're putting your card inside may be infected with malware? Share your thoughts in the comments down below, and also on our socials, on Facebook and Twitter.